Did Specops Expire My Password?
*This article is for 7.10 and higher*
Often questions arise regarding Specops and password expiration. Below are the steps that can be followed to verify whether or not Specops caused a password to expire.
Checking the Periodic Scanning tab
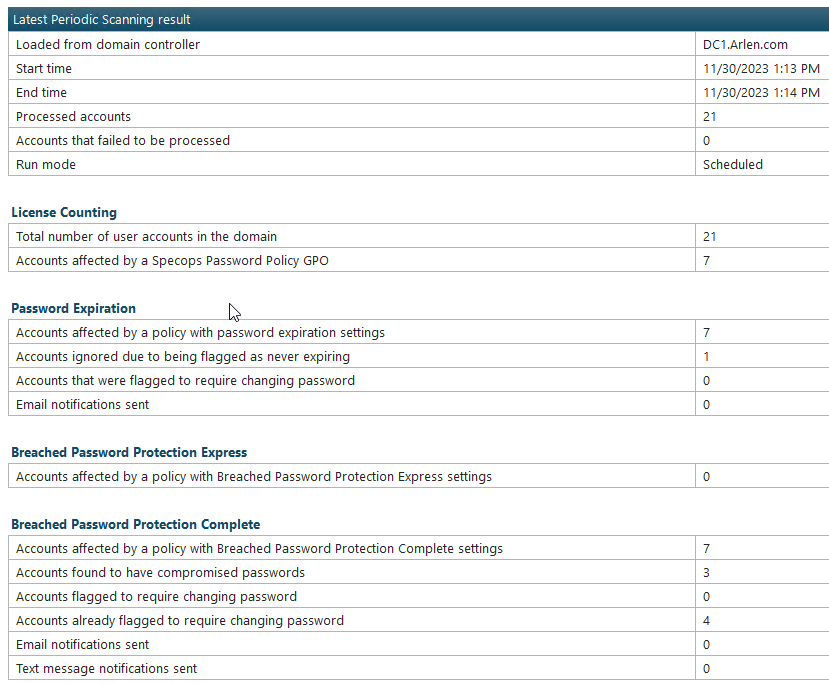
This tab provides counts of users affected by Specops Password Policy, along with license information, password expiration, users whose passwords have been affected due to breached password protection:

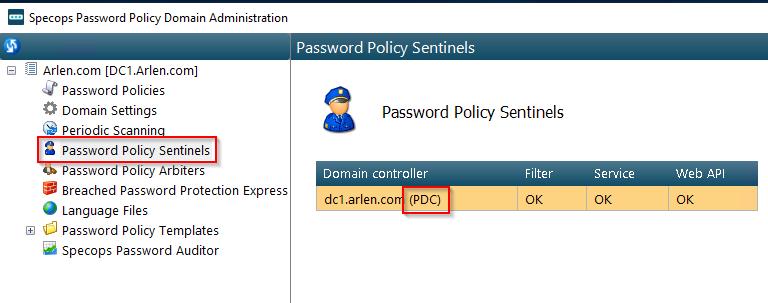
We can also take this a step further by first confirming the PDC by going to the Password Policy Sentinels tab and seeing which DC is marked with the (PDC):
Then utilizing the logs in the event viewer under Applications and Services Logs, under the Specops filter:
We see the cause of 1094 is a user found on the breached password protection express list and a 1089 is Specops expiring the password based on the age of the password.
| Event Source | Event ID | Description |
|---|---|---|
| Password Sentinel Service (Specops) | 1094 | [Breached Password Protection Express] Expiring the password of 'user' |
| Password Sentinel Service (Specops) | 1089 | [PasswordExpiration] Expiring the password of user |
Password Change-Breached Password Protection Complete
If these options are enabled in the policy, it can cause a user to change their password if it is found in the complete API after a successful password change, which is logged under the Application event log on the domain controller where the password change/reset was processed as Event 102 (successful user password change) or Event 103 (successful admin password reset).
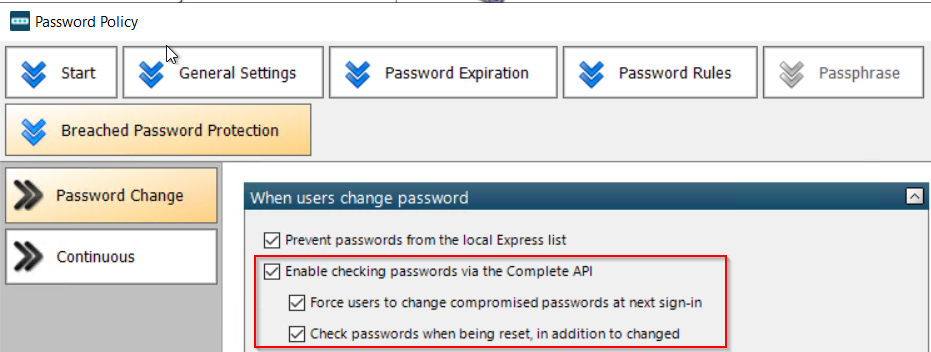
The corresponding events can be found on the Arbiter server in the Windows Applications and Services Logs/Specops log. The table below shows the list of events when a password is rejected by the Arbiter when checked against the complete list.
| Event Source | Event ID | Description |
|---|---|---|
| Password Arbiter (Specops) | 2016 | Request to Breached Password Protection API completed. Password for user 'testuser' was blacklisted. |
| Password Sentinel Service (Specops) | 1011 | The password that was set for 'testuser' was found in the breach list, user will be forced to change it at next logon. |
