This website uses cookies to ensure you get the best experience on our website. Learn more

Why cached credentials are causing account lockouts
Table of Contents
Active Directory user accounts can get locked out due to a number of reasons, especially when working remotely. Windows systems can cache credentials for users. Yet, cached credentials causing account lockouts is a major problem for remote users.
Cached Active Directory credentials
To understand the purpose of cached credentials, let’s look at the normal login process in general terms. When a user logs in on a domain-joined computer, the user credentials are passed to the nearest domain controller in the environment. The domain controller verifies the credentials, and either authenticates the user, or rejects the credentials entered.
Remote workers using domain-joined laptops to access business resources, will not directly connect to the corporate network. By extension, these users will not have access to a domain controller to answer authentication requests. The resolution to this issue is cached credentials. How do cached credentials work?
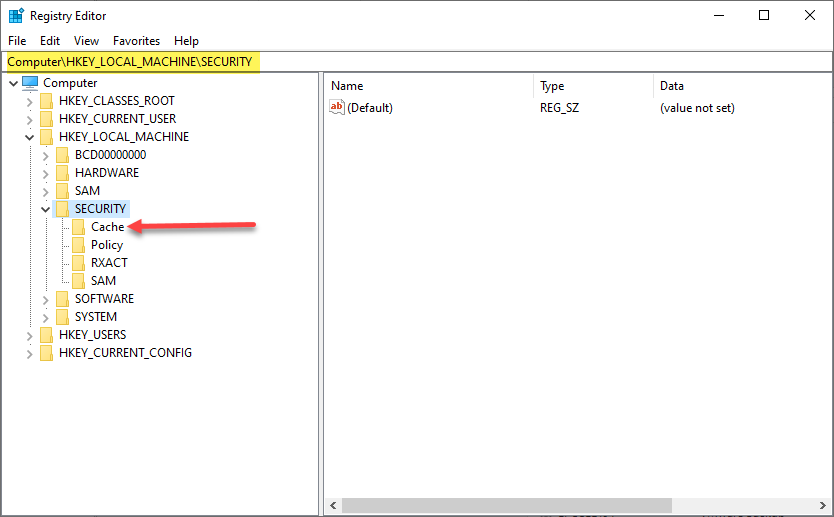
Cached credentials allow the remote workstation or laptop to store the hashed value for a successful login in a local credential cache that enables the computer to authenticate and log in locally, regardless of whether a domain controller is available. Microsoft stores the hashed value in the registry key HKEY_LOCAL_MACHINE\SECURITY key.
There is another registry value that organizations can control via Group Policy that configures logon caching. The key resides in HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\Current Version\Winlogon\ and is called CachedLogonCount. By default, this is set to 10 cached logons. If the key is set to “0”, this turns off logon caching.
The Group Policy setting is found in In the Group Policy dialog, there is a great explanation of the policy-setting as follows:
“Interactive logon: Number of previous logons to cache (in case domain controller is not available)
Each unique user’s logon information is cached locally so that, in the event that a domain controller is unavailable during subsequent logon attempts, they are able to log on. The cached logon information is stored from the previous logon session. If a domain controller is unavailable and a user’s logon information is not cached, the user is prompted with this message:
There are currently no logon servers available to service the logon request.
In this policy setting, a value of 0 disables logon caching. Any value above 50 only caches 50 logon attempts. Windows supports a maximum of 50 cache entries and the number of entries consumed per user depends on the credential. For example, a maximum of 50 unique password user accounts can be cached on a Windows system, but only 25 smart card user accounts can be cached because both the password information and the smart card information are stored. When a user with cached logon information logs on again, the user’s individual cached information is replaced.”
More about resetting a cached domain password can be found in our accompanying blog post.
Cached credentials causing account lockouts
Cached credentials allow a remote user, without access to a domain controller, log in to the machine locally. But, it can also cause account lockouts. Suppose a remote end-user is using cached credentials to log in to a domain-joined laptop locally. Even though the credentials allow the user to log in, the user account’s current state in Active Directory may have an aged password requiring the user to select a new password.
A user in this account scenario may assume the password is the same for any corporate resource to which they attempt to connect. What if they continue to attempt to connect to their web email using the old password? Additionally, suppose they connect to the corporate network with a VPN connection. In that case, the remote laptop or desktop will attempt to use the user’s cached credentials to access network resources. When this happens, the domain controller views the authentication attempts as failed logins, resulting in an account lockout after the specified failed login threshold is reached.
Reminding users of password expirations
Specops Software provides a free tool that allow organizations to deal effectively with cached credentials, especially for remote employees. One of the challenges for remote employees that leads to issues is the lack of visibility when account passwords expire. Often, a remote employee is not aware of their account password expiring. It leads to no action taken beforehand. Specops Password Notification includes the ability to effectively remind users of an impending password expiration so they can proactively set a new account password before it expires.
Updating the cached credentials when a domain controller can’t be reached
With a third-party password reset solution you can easily manage remote password resets. Specops uReset allows users to securely reset their Active Directory passwords right from the Windows logon screen. It also prevents account lockouts by updating the local cached credential, even when a Domain Controller cannot be reached.
(Last updated on April 30, 2025)