This website uses cookies to ensure you get the best experience on our website. Learn more
SSO vs Enterprise Password Manager: Which is better for reducing your password risk?
Table of Contents
Organizations looking to reduce the burden of passwords on their users often consider Single Sign On (SSO) vendors or deploying an enterprise password manager. Each has their advantages, so which one is best for an organization to choose?
Single-sign on solutions and enterprise password managers are not necessarily mutually exclusive but how do they compare?
Both allow employees to use one login to manage their access to many different websites and apps. Password managers do this via a vault of stored passwords protected by one password. Single sign-on solutions do this via the Secure Access Management Protocol (SAML) standard which allows identity providers (like SSOs) to pass authentication details to service providers (various websites and apps).
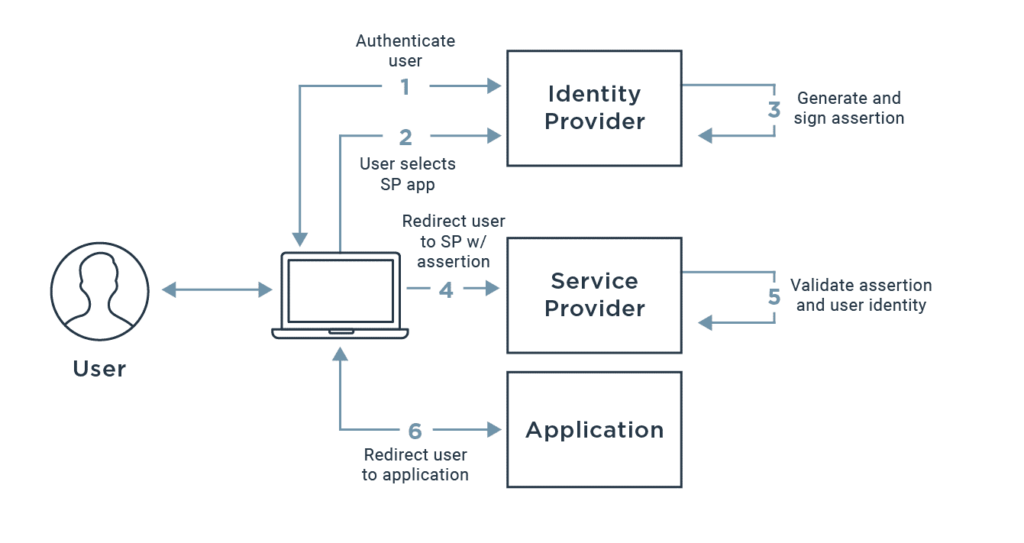
Both lift the burden of managing many passwords off of employees. The average employee has 11 or more passwords they have to remember just for work. At the same time, Google reports that over 65% of people surveyed admit to reusing passwords across sites. This burden of logins makes password reuse understandable but is also why work credentials outside the Active Directory password are a risk vector. Single-sign on solutions reduce the number of logins an individual employee has to remember for sites that are compatible with SSO. Enterprise password managers use autosave and autofill functionality to life the burden of password management and reduce the number of logins an individual employee has to remember for all sites and apps, regardless of SAML support.
Both increase password security. For sites that accept single sign-on, the password for that site is removed and replaced with the SSO authentication. Reducing the number of passwords in play has an obvious benefit on the risk unmanaged passwords pose to an organization. Passwords used by employees that aren’t managed by IT will often be weak or reused since IT departments cannot control the password policies of other websites. Password managers make it easy for IT departments to remove this risk by giving end users a tool that will generate long, complex and random passwords that are automatically saved and entered on their behalf when logging in to a website. On top of that, a good enterprise password manager will give flag to end users and admins when saved passwords are reused or known to be compromised.
For organizations choosing between single sign-on and an enterprise password manager, an enterprise password manager will cover more use cases.
| Use Case | Single sign-on | Enterprise password manager |
| Reduce number of passwords users need to remember | Yes, but not for all websites (SAML required*) | Yes, can store any credentials |
| Increase password security for individual employees | Yes, but only for SAML websites | Yes, automatically saves long random passwords, flags weak/reused/compromised passwords |
| Increase password security for shared logins | No, shared logins not supported | Yes, can securely share passwords with shared vaults |
| Supports multiple identities for one user (e.g., multiple email address logins) | No, can only support one identity per session | Yes, can save any email & password pair, whether tied to main work email address or not |
| Increase password security for Shadow IT apps and websites | No, can only support websites and apps IT is aware of | Yes, end users can save any credential pair |
* SSO only works with websites that support SAML; however, some websites require premium plans to support SSO, as seen here, adding extra cost to SSO implementation
As you can see in the above chart, while both password managers and single sign-on reduce the password burden, SSO solutions still have some gaps. The better approach for IT departments is to use single sign-on paired alongside an enterprise password manager to achieve almost universal password protection.
(Last updated on February 24, 2025)
