This website uses cookies to ensure you get the best experience on our website. Learn more
Securing ADFS against password spraying attacks
Table of Contents
Stolen account passwords provide the “path of least resistance” into a victim network for an attacker. Once compromised credentials are obtained, the attacker can easily access business-critical systems with little effort. Active Directory Federation Service (ADFS) is a solution that allows federating identity and access management and sharing entitlement and authorization rights across enterprise boundaries.
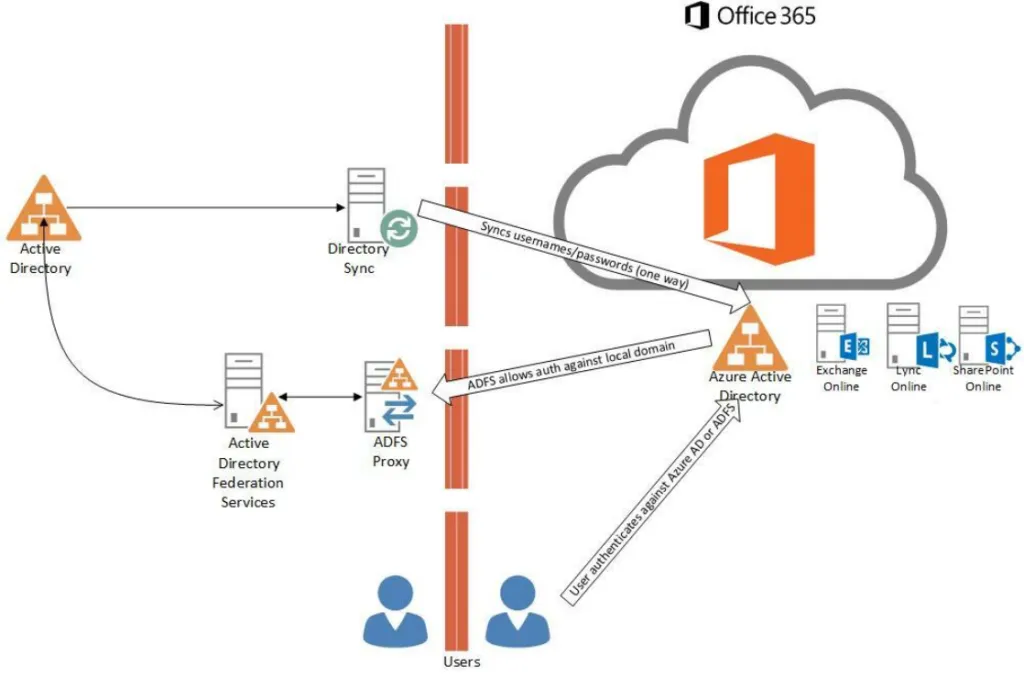
Companies often use it to federate IAM between on-premises and cloud environments and provide single sign-on for business-critical resources across infrastructure boundaries. So how can organizations protect their ADFS environment from password attacks, including password spraying and other threats that attempt to steal and compromise credentials?
What is a password spraying attack?
The password spraying attack is a specialized password attack commonly used by attackers that is reasonably effective and helps avoid detection by traditional password defenses. Instead of trying many different passwords on a single user account, the password spraying attack may try one or two common passwords across many different accounts and services. It may even span across many different organizations.
The attacker picks passwords commonly used by end-users or found on breached password dumps. Password spraying attacks help avoid detection by many available traditional security monitoring solutions since the attack pattern looks similar to normal failed login attempts. The attempts do not lock out accounts or trigger other monitoring thresholds.
Organizations using ADFS will have an Active Directory Domain Services infrastructure that typically uses the traditional ADDS password and account lockout policies. In addition, most organizations will have an account lockout policy that triggers after 3-5 unsuccessful login attempts, locking the user account. Password spraying stays under this threshold for the targeted user accounts to not trigger an account lockout.
Password spraying is all about playing the odds. Attackers know if they spray common passwords across thousands of accounts, most likely, they will have a few successes in users that have selected common or easy-to-guess passwords. You may wonder what they do with the initial successful account compromises?
Threat actors may use these initial successful password spraying victims to comb through emails, look for additional contacts, sensitive information, privileged information, or send phishing links to others in the organization.
How is password spraying different than brute force attacks?
As discussed, password spraying takes only a small number of passwords and attempts to log in with those passwords across multiple accounts, even in different organizations. In contrast, attackers use brute force password attacks to try different passwords against a smaller targeted group of user accounts.
After performing reconnaissance on an organization, an attacker may gather the details of users with higher-level access in the company, such as C-levels or administrators managing the infrastructure environment. Even if the brute force attack does not successfully compromise a password, it can lead to other types of problems for organizations using ADFS.
Brute force password attacks generally trigger organizations’ account lockout policies to protect against such attacks. Largescale brute force password attacks can lockout critical service accounts, user accounts, and others in the environment, leading to a denial of service, even if this isn’t the overall end goal.
Securing ADFS against password attacks
Microsoft’s recommendation for securing your ADFS environment from password spraying, brute force, and other types of password spraying attacks involves a multi-layered approach. The recommended security protections apply three levels of security, including:
- Level 1 – Baseline
- Level 2 – Protect your extranet
- Level 3 – Move to passwordless for extranet access
Level 1 – Baseline
One of the first recommendations from Microsoft is to run ADFS 2016, which is also known as AFFS 4.0. With ADFS 2016 you can implement extranet smart lockout. Extranet smart lockout protects users from account lockouts from malicious activity. It does this by differentiating from sign-in attempts from a familiar location for user sign-in attempts and those coming from malicious activity.
Other best practices at this level of protection are:
- Monitor and block suspicious IPs – you can use the Azure AD Premium Risky IP report and also Extranet Banned IP addresses feature.
- In conjunction with Azure AD Premium, you can use Azure AD Password Protection to prevent password guessing
Level 2 – Protect your extranet
Protecting your extranet using ADFS involves using modern authentication with mobile clients as well as using multi-factor authentication (MFA) to secure all extranet access. Modern devices and email clients can use modern authentication protocols for connecting to your ADFS federated extranet.
MFA can be used for additional protection from brute force and password spraying attacks. It can be used with Conditional Access Policies in Azure AD to provide a robust security context around user logins.
Level 3 – Move to passwordless for extranet access
Getting rid of passwords altogether helps to reduce the risk posed to user passwords significantly. Microsoft offers several password less technologies businesses can benefit from, including:
- Windows 10 & 11 Hello for Business
- Azure MFA OTP
- MDM-managed devices can take advantage of certificate-based logons
However, many organizations might find that passwordless authentication isn’t mature enough to replace passwords in their environments. As we saw when Microsoft all but abandoned Active Directory for Azure Active Directory, Microsoft pushing passwordless means passwords themselves are more vulnerable than ever. As we see Microsoft shift focus away from the number one authentication method in the market, organizations are left even more vulnerable. Rather than jump to technology that might not be able to deliver on the hype, organizations will need to protect current authentication methods and make use of simple strategies like multiple factors, blocking known breached passwords and encouraging the use of passphrases.
Secure ADFS against password attacks using Specops Password Policy
One of the significant weak points in traditional enterprise datacenter password security is the outdated password policies found in Active Directory Domain Services password policies. Unfortunately, the ADDS password policy is not designed for the modern password challenges facing organizations today, including password spraying attacks and dangerous end-user behaviors such as incrementing passwords.
Specops Password Policy is a robust password policy solution built on the Group Policy engine in Active Directory. It enables organizations to overcome the limitations of native Active Directory Password Policy capabilities. With Specops Password Policy, organizations have access to the following features:
- Length-based password aging
- Password character group requirements
- Custom disallowed password dictionaries
- Regular expression password filtering
- Passphrases
- Prevent the use of more than 4 billion compromised passwords with Breached Password Protection which includes passwords found on known breached lists as well as passwords being used in attacks happening right now
- Find compromised passwords in your Active Directory environment
- Intuitive and informative client messaging
- Block user names, display names, specific words, consecutive characters, incremental passwords, and password reuse
- GPO-driven implementation, aligning with current group policies already configured
With Specops Breached Password Protection, it provides continuous protection from breached passwords. Specops protects against known breached passwords and newly discovered passwords using brute force or other password spraying attacks.
The continuous Specops Breached Password Protection uses Specops own network of honeypots worldwide that capture breached password data. This data is then fed back into Specops Breached Password Protection and, by extension, Specops Password Policy.
IT admins can:
- Prevent breached passwords in the environment
- Continuously check for breached passwords
- Proactively force users to change passwords that become breached
- Notify users of breached password events
The Specops Express list is an optimized subset of the larger Complete list. When enabled, the service checks your users’ passwords during a password change and blocks them immediately from using a breached password. Admins can also run nightly scans against the Express list.
Using the Specops Complete API solution provides access to a database of over 4 billion passwords and connects to your network via an API key. The service checks your users’ passwords during a password change or reset operation and notifies them via email or SMS if the password is known to be breached.
Using Specops Breached Password protection in your environment helps strengthen your organization’s cybersecurity posture, including ADFS, against brute force and password spraying attacks. Learn more about Specops Password Policy and see how you can bolster Active Directory password protection in your environment.
(Last updated on March 17, 2025)



