This website uses cookies to ensure you get the best experience on our website. Learn more
Microsoft adds phishing protection to Windows 11
Table of Contents
With the recent release of Windows 11 version 22H2, Microsoft has introduced some new capabilities that are designed to protect users against phishing attacks. These phishing protection features are designed to prevent users from making some of the mistakes that most commonly lead to credentials being stolen.
Enabling phishing protection on Windows 11
You can access the Windows 11 phishing protection tools by opening Settings and then clicking on Privacy and Security, followed by Windows Security. Next, click on App and Browser Control and then click on the Reputation Based Protection Settings link. You can see the Phishing Protection settings shown in Figure 1.
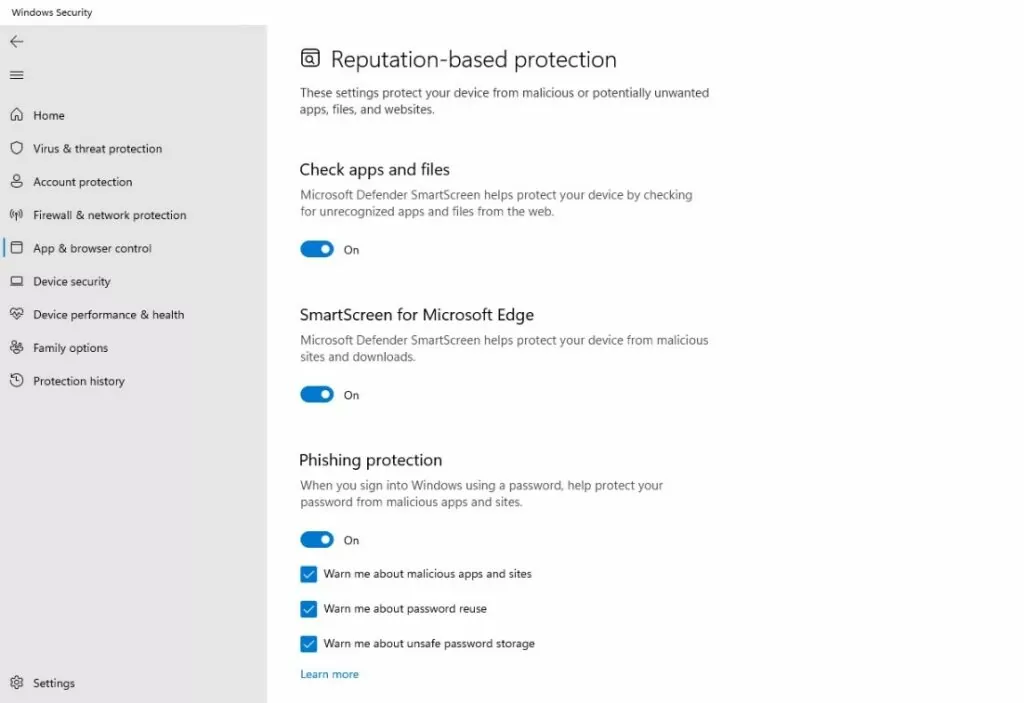
The Windows 11 Phishing Protection settings are found on the Reputation-Based Protection screen.
As you can see in the figure above, there is an on / off switch that you can use to enable or disable phishing protection. Additionally, there are three check boxes that are used to enable the individual phishing protection mechanisms.
The first of these checkboxes is the Warn Me About Malicious Apps and Sites checkbox. Simply put, when you enable this checkbox, Windows will watch for situations in which a Chromium-based browser connects to a known phishing site. If the user enters their password into such a site, Windows will prompt the user to change their password.
The second checkbox is designed to warn users about the dangers of password reuse. If a user enters their local, Active Directory, or Azure AD password into a site, then Windows will warn the user about the dangers of password reuse.
The third checkbox, when enabled, will warn users about unsafe password storage. If a user were to enter their password into Notepad, a Microsoft 365 document, or something like that, then Windows will assume that the user is trying to make a note of their password and will warn them against doing so.
Are credentials still vulnerable?
Microsoft’s new phishing protection features represent a major step forward in protecting Windows users against phishing attacks. By adding these features, Microsoft is essentially acknowledging that phishing attacks have become a huge problem and that something needs to be done to keep users safe. Even so, the new phishing protection mechanisms should not be relied upon to provide comprehensive protection. There are still several ways in which user’s passwords may still be vulnerable, even with phishing protection enabled.
These vulnerabilities are not tied to anything that the new phishing protection features are doing wrong or to any known bugs, but rather stem from the general approach that Microsoft uses to keep users safe.
The one thing that all three of the phishing protection mechanisms have in common with one another is that they are all designed for real-time protection. In other words, if the user makes a mistake such as entering their password into a phishing site, reusing a password, or saving their password to a file then Windows 11 will intervene. That’s great. The problem however, is that Windows 11 does not consider anything that a user might have already done in the past.
Take the issue of password reuse for example. While Windows 11 might stop a user from reusing their Active Directory password, odds are that a user who is inclined to reuse passwords has probably already done so. The same could also apply to a user entering their password into a phishing site. Even though Windows might prevent users from being tricked by phishing sites in the future, there is no guarantee that the user has not already falling victim to a phishing scam in the recent past.
Don’t forget breached passwords
The key to keeping your users safe against phishing attacks is to treat the Windows 11 phishing protection features as a part of a more comprehensive solution. While Windows may do a good job of guarding against phishing attacks, your best bet for dealing with situations that may have already occurred is to use third-party software to monitor for credential theft.
Specops Password Policy maintains a database of billions of passwords that are known to have been breached. This means that if a user has previously used their Active Directory on multiple sites and one of those sites has suffered a breach, then the user’s credentials have likely been stolen. Specops can automatically alert you to the compromised credentials and force the user to change their password immediately.
(Last updated on May 12, 2025)


