This website uses cookies to ensure you get the best experience on our website. Learn more
How to delegate password reset permissions in Active Directory
Table of Contents
Least privilege access is a crucial part of security that protects against overprovisioning user permissions. Even with IT technicians, and junior administrators, this needs to be considered when configuring permissions in the environment. A case in point is helpdesk staff who need to reset end-user passwords in an Active Directory environment. How can organizations use the least privilege model in assigning permissions to IT helpdesk staff for everyday tasks such as password resets?
Least privilege access – why is it vital for security?
Let’s consider why the least privilege access model is essential in provisioning permissions, even for IT helpdesk staff. Often, attackers who look to compromise an environment do so using compromised credentials. Suppose an attacker compromises an end-user account with overprovisioned permissions (more than needed). In that case, the attacker now has an account with far more capabilities than if it was provisioned correctly with least privilege access.
In a perfect world, you want to have zero security compromises of your accounts. However, to design security properly, you have to plan for compromise at some point. If an attacker compromises your account credentials, you want the “blast radius” of the security compromise to be as minimal as possible. Find out more on how account admins pose a risk and how to handle admin accounts to protect sensitive information.
The holy grail of account compromise is for an attacker to compromise an admin account. Specifically, in Active Directory, this is known as a Domain Admin. With a domain admin account, an attacker has permissions to access just about any system or data on the network. Often, helpdesk technicians and other IT staff are placed in the domain admins Active Directory group. This provides an easy way to ensure they can carry out tasks they may need, such as password resets. However, this is a dangerous approach from a security perspective.
As a security best practice, even senior IT administrators who may legitimately need domain admin-level access, should not use this account for general day-to-day operations. IT administrators should typically have a low-level user account used for everyday activities, and only use a domain admin account when needed to carry out special server operations or other required activities.
Want to put the principle of least privilege into practice? Here are six ways you can apply least privilege to your Active Directory.
Delegated password reset permission in Active Directory
Active Directory includes the ability to delegate control of various permissions within Active Directory to specific users or groups. It allows IT admins to assign particular users or groups to perform granular tasks such as resetting an account password, and forcing the user to change their password at the next logon. Instead of adding IT helpdesk technicians or other users into dangerous groups such as the domain admins group, delegation allows assigning the specific permissions they need in the environment. It will enable aligning your IT helpdesk to a least privilege model.
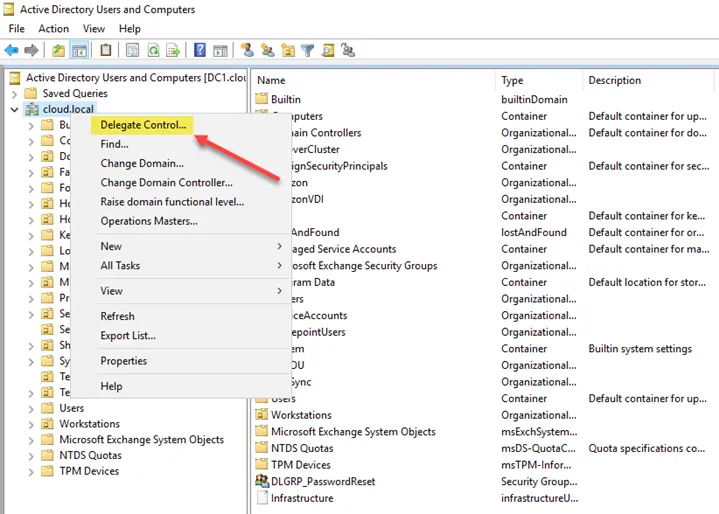
How are the password reset permissions delegated in Active Directory? To begin, right-click the object level in Active Directory you want to delegate permissions. Below, the parent domain level is chosen. However, you can delegate permissions at a specific OU level as well. Right-click the object and select Delegate Control.
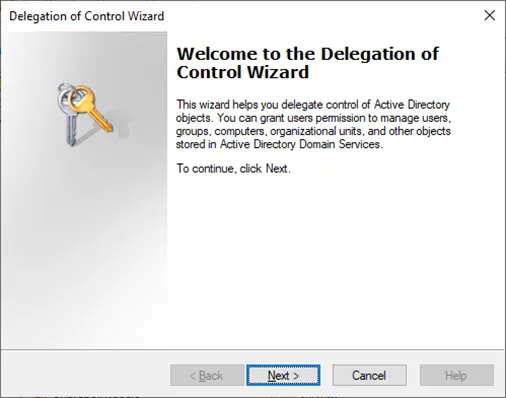
The Delegation of Control Wizard begins, which allows delegating specific, granular permissions.
Choose the user or group you want to delegate permissions. It is best practice to delegate permissions to a group instead of a user. In this way, administrators can take users in and out of groups delegated granular permissions. This approach provides a much better way to manage Active Directory permissions delegation.
Choose the permissions you want to delegate in the wizard. Since we are interested in password reset activities, choose the “Reset user passwords and force password change at next logon” permissions.
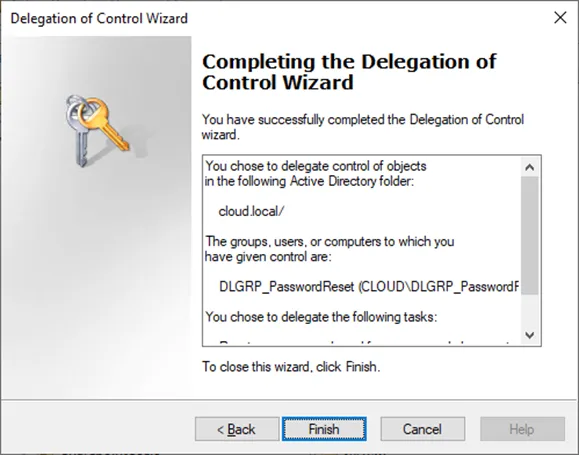
Complete the Delegation of Control Wizard to assign the granular permissions to the Active Directory user or group.
Securing self-service password resets
Delegating the appropriate level of permissions to IT helpdesk staff is extremely important to align with the least privilege access model. End-users can reset their password by default. However, this process can lead to problems for end-users who may not be logging in from a Windows device to receive the password change prompt, or have run into difficulty changing their password. Specops uReset is a self-service password reset solution that provides a robust platform to allow your end-users to change their passwords, and unlock their accounts. It does this by validating end-user identity with a wide range of multi-factor authentication solutions that your organization customizes. End-users can reset their password, regardless of location, device, or browser.
(Last updated on April 30, 2025)