This website uses cookies to ensure you get the best experience on our website. Learn more

How to optimize Entra MFA with Specops uReset and Secure Service Desk
Table of Contents
At Specops Software, we work closely with many customers and assist with the challenges they face in transitioning to more secure authentication methods. This has become increasingly critical as both the complexity and frequency of cyberattacks have increased. Our mission is to provide solutions and expertise to help organizations deter and stop threat actors. One of the most powerful and popular tools for this is Microsoft Entra ID, especially when integrating Entra MFA with other 3rd party applications. This post will guide you on how to optimize Entra ID with two of our most popular products: Specops uReset and Specops Secure Service Desk.
Why use Entra MFA?
As cyberattacks have become increasingly frequent, sophisticated, and damaging, Microsoft introduced mandatory multifactor authentication (MFA) for all Azure sign-ins. Research by Microsoft shows that MFA can block more than 99.2% of account compromise attacks. When choosing the MFA methods to make available to your users, you’ll want to consider the security and usability of the available methods.
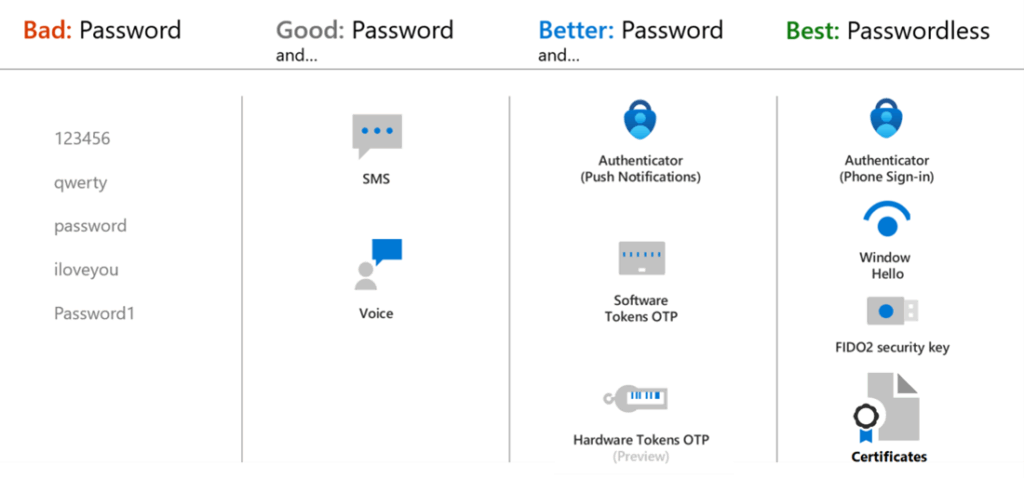
For the best flexibility and usability, many Azure customers use the Microsoft Authenticator app. It provides the best user experience and multiple methods, such as passwordless, and MFA push notifications.
Users will typically setup the Microsoft Authenticator with push notifications, where the sign-in experience includes:
- Enter the username
- Enter the password
- Confirm the sign-in with a push notification in the Microsoft Authenticator app (and verifying the push notification with a code and biometrics)
The passwordless option
Users can further secure and simplify their sign-in experience by setting up passwordless sign-in. Microsoft Authenticator can be used to sign in to any Microsoft Entra account without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometrics.
Instead of seeing a prompt for a password after entering the username, the sign-in experience includes:
- Enter the username
- Complete the sign-in with a push notification in the Microsoft Authenticator app (and verifying the push notification with a code and biometrics)
Microsoft recommends passwordless authentication methods such as Windows Hello, Passkeys (FIDO2), and the Microsoft Authenticator app because they provide the most secure sign-in experience. Although a user can sign-in using other common methods such as a username and password, passwords should be replaced with more secure authentication methods.
Implementing passwordless
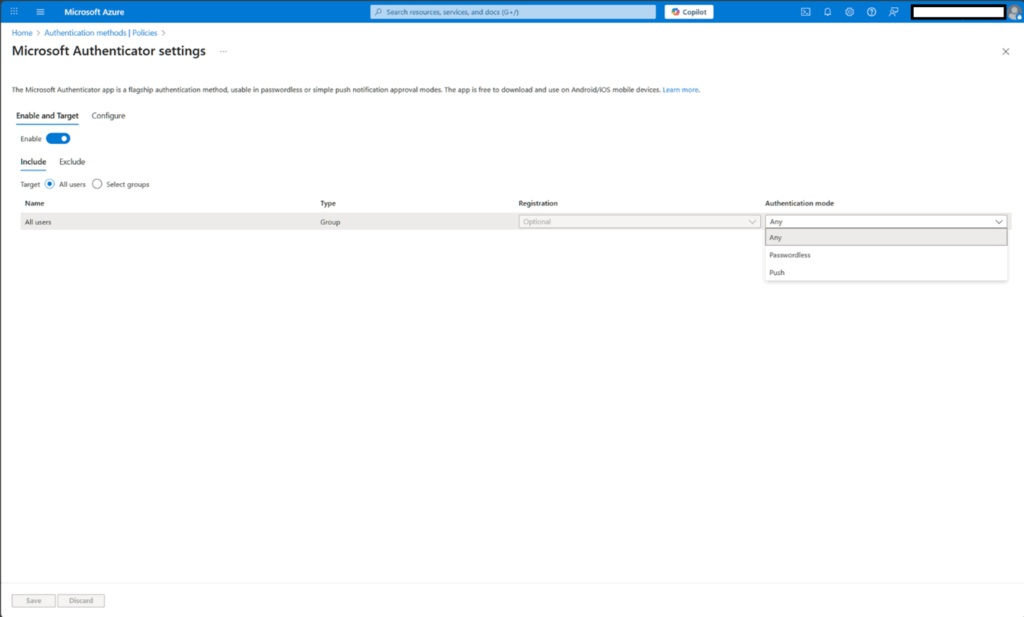
Entra administrators can confirm that the Microsoft Authenticator policy is configured to allow the use of passwordless sign-in.
- Sign in to https://portal.azure.com
- Browse to Microsoft Entra authentication methods > Policies > Microsoft Authenticator.
- Confirm that the Authentication mode drop-down list option is set to “Any” or “Passwordless”. The available options are:
- Any – Allows the use of either Passwordless or Push (this is the default)
- Passwordless – Allows the use of Passwordless only
- Push – Allows the use of Push only (password+MFA push notification)
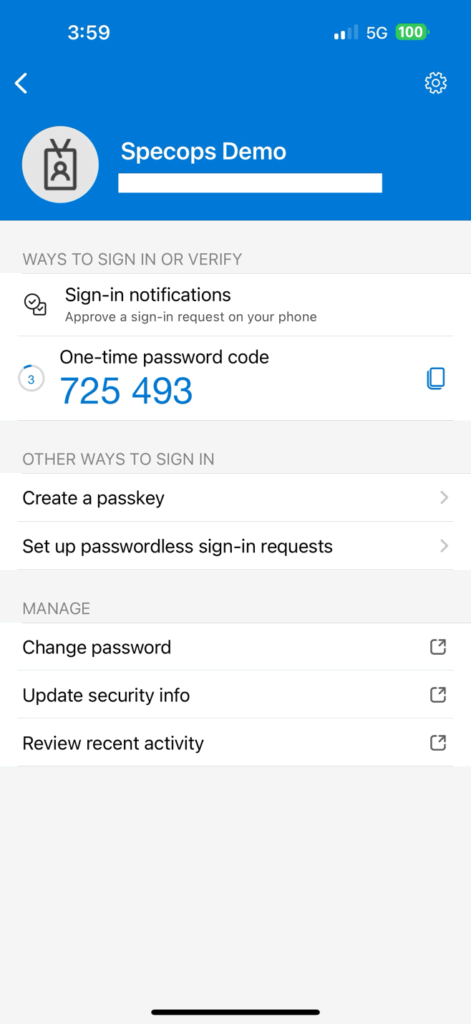
Users would select the “Set up passwordless sign-in requests” option in their account in the Microsoft Authenticator app.
See the links below for more information on passwordless sign-in from Microsoft:
- https://learn.microsoft.com/en-us/entra/identity/authentication/concept-authentication-methods
- https://learn.microsoft.com/en-us/entra/identity/authentication/howto-authentication-passwordless-phone
- Identity Architecture: Using passwordless with the Microsoft Authenticator App
Entra administrators can then set the preferred sign in method to passwordless for each user:
- Sign in to https://portal.azure.com
- Browse to Microsoft Entra ID > Users > All users.
- Choose the user you wish to perform an action on and select Authentication methods. Then in the right pane, set the Default sign-in method to “Microsoft Authenticator notification”.
Optimizing Entra passwordless sign-in and MFA with Specops Secure Service Desk & Specops uReset
Using Microsoft Entra passwordless sign-in secures and simplifies logins to Microsoft 365, as well as other 3rd party applications that integrate with Entra MFA, such as Specops uReset and Secure Service Desk.
- uReset: A self-service reset portal where users must verify themselves with MFA to reset their passwords from anywhere. And on AD joined laptops, cached credentials can also be updated as part of the reset process, allowing users to login immediately after resetting their password without the need for a VPN connection.
- Secure Service Desk: A portal for Service Desk agents to verify users with MFA before giving them any kind of assistance, as well as reset passwords for users once they’ve been verified.
Entra MFA optimization with uReset and Secure Service Desk allows users to use the same sign-in experience and methods that they already use with Microsoft 365, without the need for additional MFA setup or registration steps.
Some key considerations when using Entra MFA
- Specops uReset
- When a user needs to reset their password or unlock their account (scenarios where the user forgot or cannot use their current password for any reason), and if a user’s typical Entra MFA sign-in uses password+MFA, then requiring password as part of the sign-in process will create a problem, where the user cannot complete the sign-in.
- For users with Entra passwordless sign-in, users will be able to authenticate without the need to use password as part of the sign-in process, and complete the sign-in with a push notification (verifying the push notification with a code and biometrics)
- Specops Secure Service Desk
- For many Service Desk calls, a user may be able to verify themselves with a typical Entra MFA sign-in using password+MFA.
- When a user contacts the Service Desk for a password related issue, then requiring password as part of the sign-in process will create a problem, where the user cannot complete the sign-in.
Entra MFA passwordless sign-in allows for the successful use of Entra MFA for password reset and account unlock scenarios. Below are walk throughs of the password reset experience with Specops uReset, comparing Microsoft Entra MFA with password+MFA sign-in vs. passwordless sign-in.
Password reset experience with Specops uReset using Microsoft Entra MFA with password + MFA sign-in
Follow these steps for a password reset with Specops uReset using Microsoft Entra MFA with password + MFA sign-in
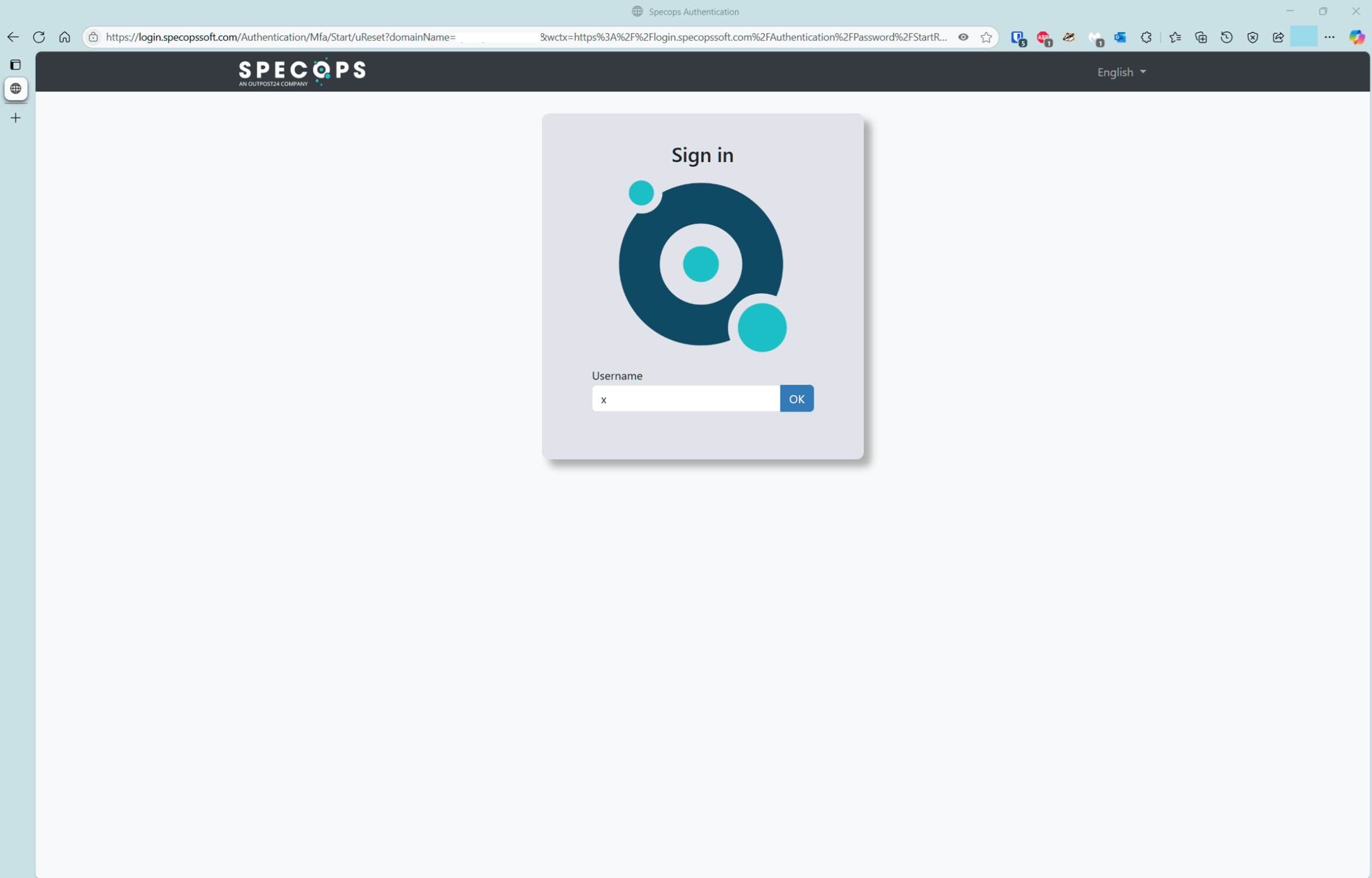
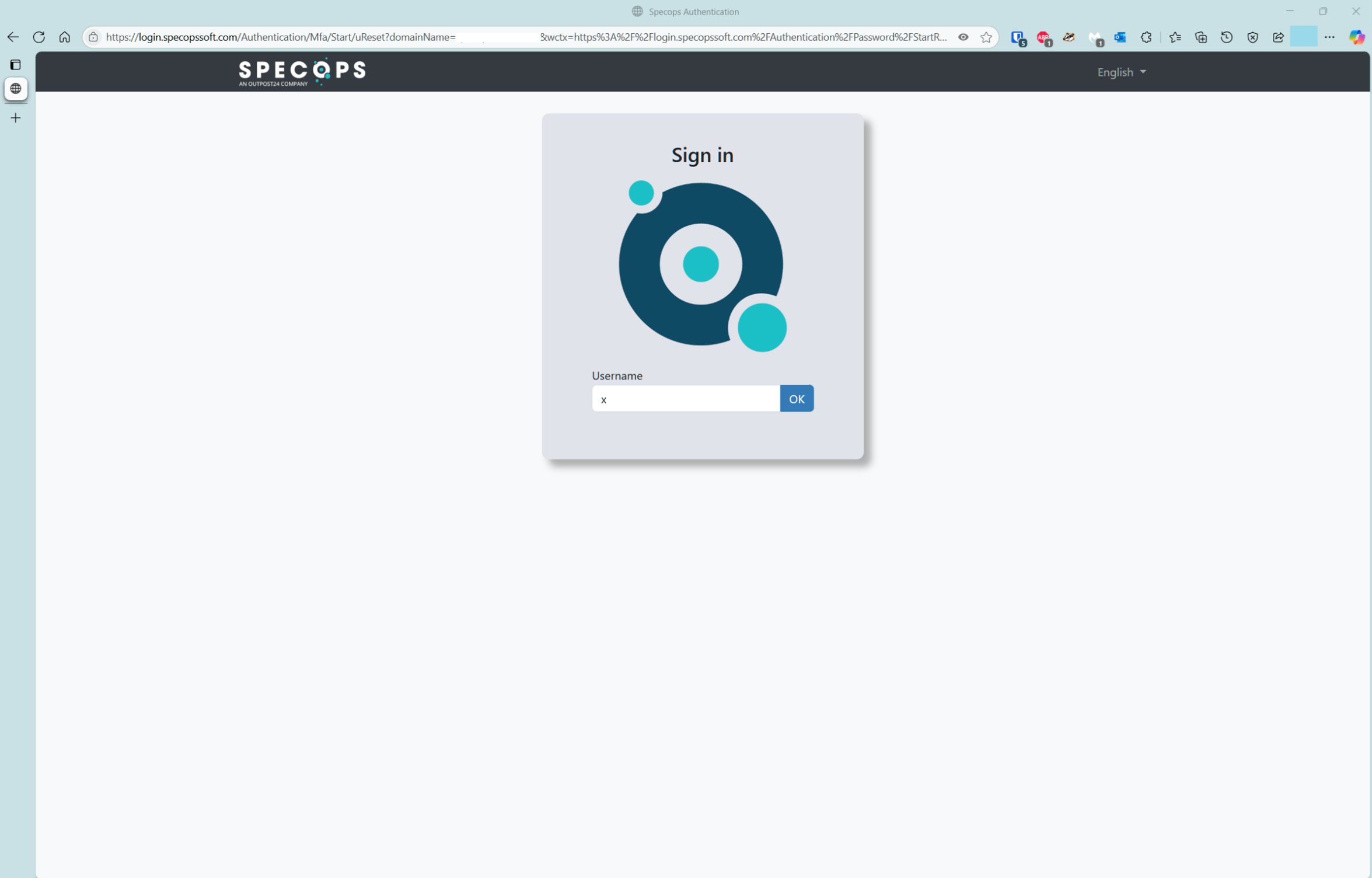
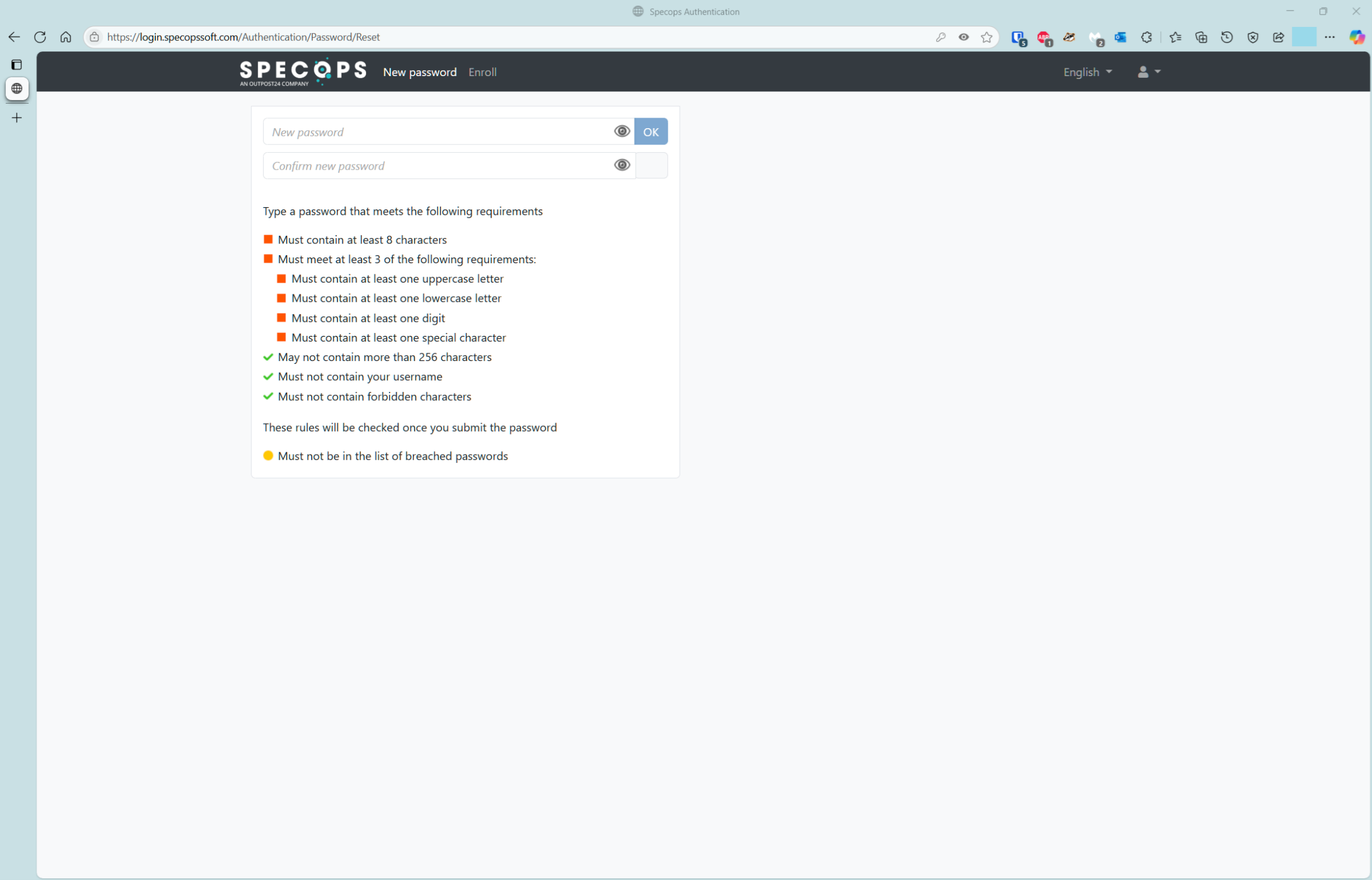
- Navigate to the password reset page
A user browses to the password reset URL, for example https://login.specopssoft.com/Authentication/Password/Reset, and enters their username, and clicks OK.
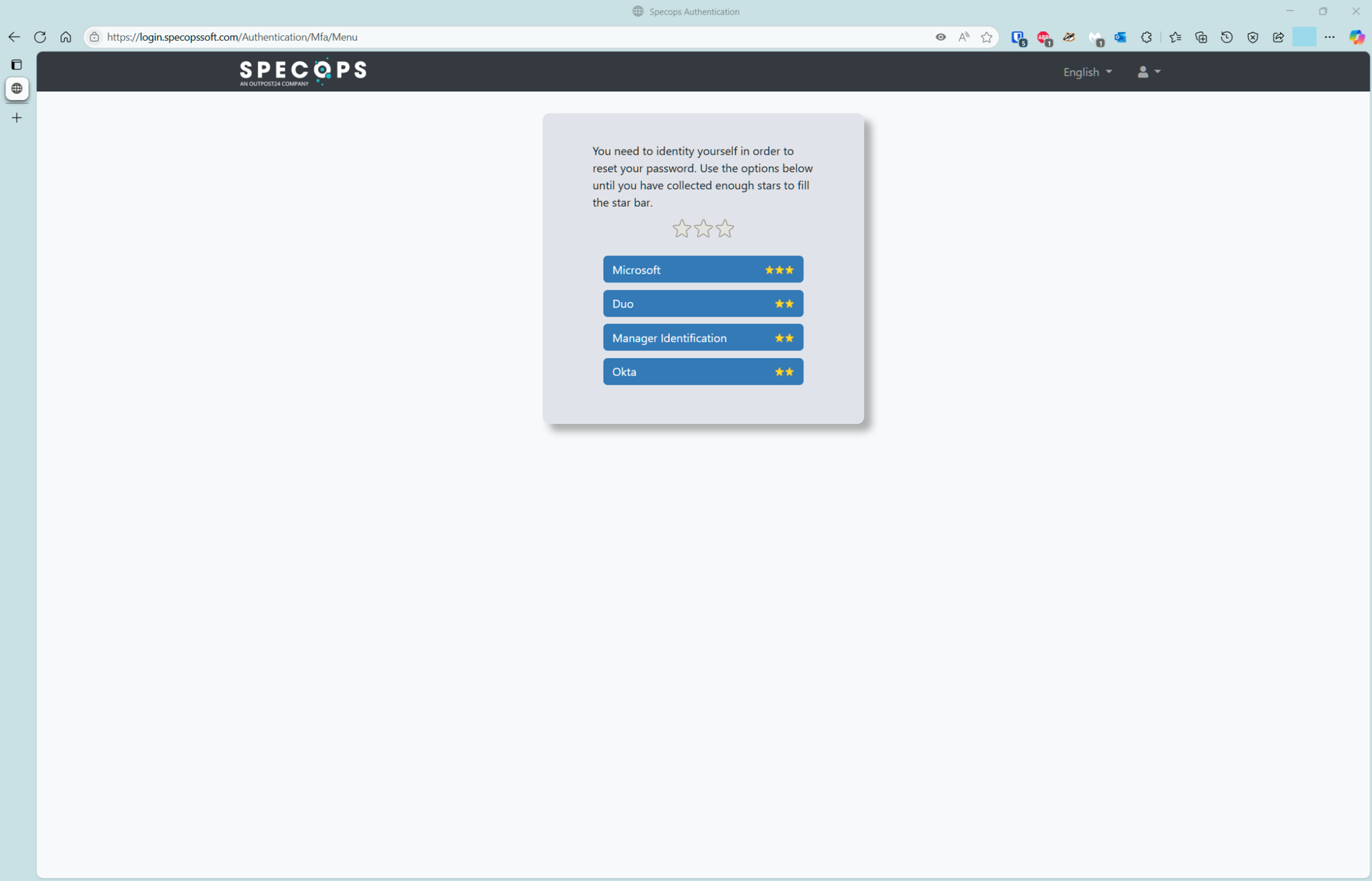
- Choose Microsoft as the MFA option
The user selects the Microsoft option from the list of available MFA options, which is defined by the Specops uReset administrator.
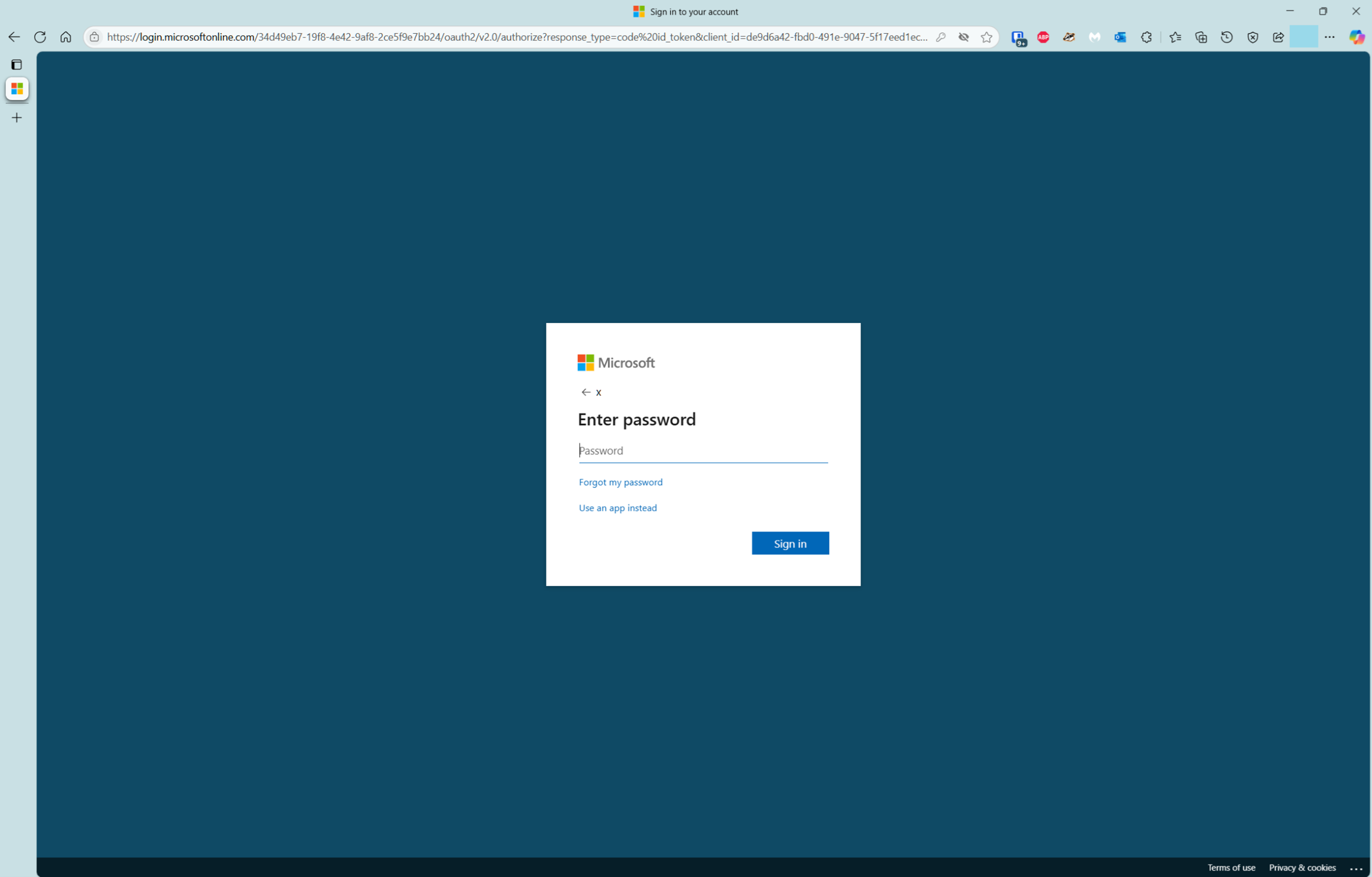
- Redirected to password prompt – reset cannot proceed
The user is redirected to the Microsoft Entra sign-in page, and is presented with the password field. Since the user is attempting a password reset because they’ve forgotten or otherwise cannot use the current password, the user cannot proceed to complete the password reset.
Password reset experience with Specops uReset using Microsoft Entra MFA with passwordless sign-in
Follow these steps for a password reset with with Specops uReset using Microsoft Entra MFA with passwordless sign-in:
- Navigate to the password reset page
A user browses to the password reset URL, for example https://login.specopssoft.com/Authentication/Password/Reset, and enters their username, and clicks OK.
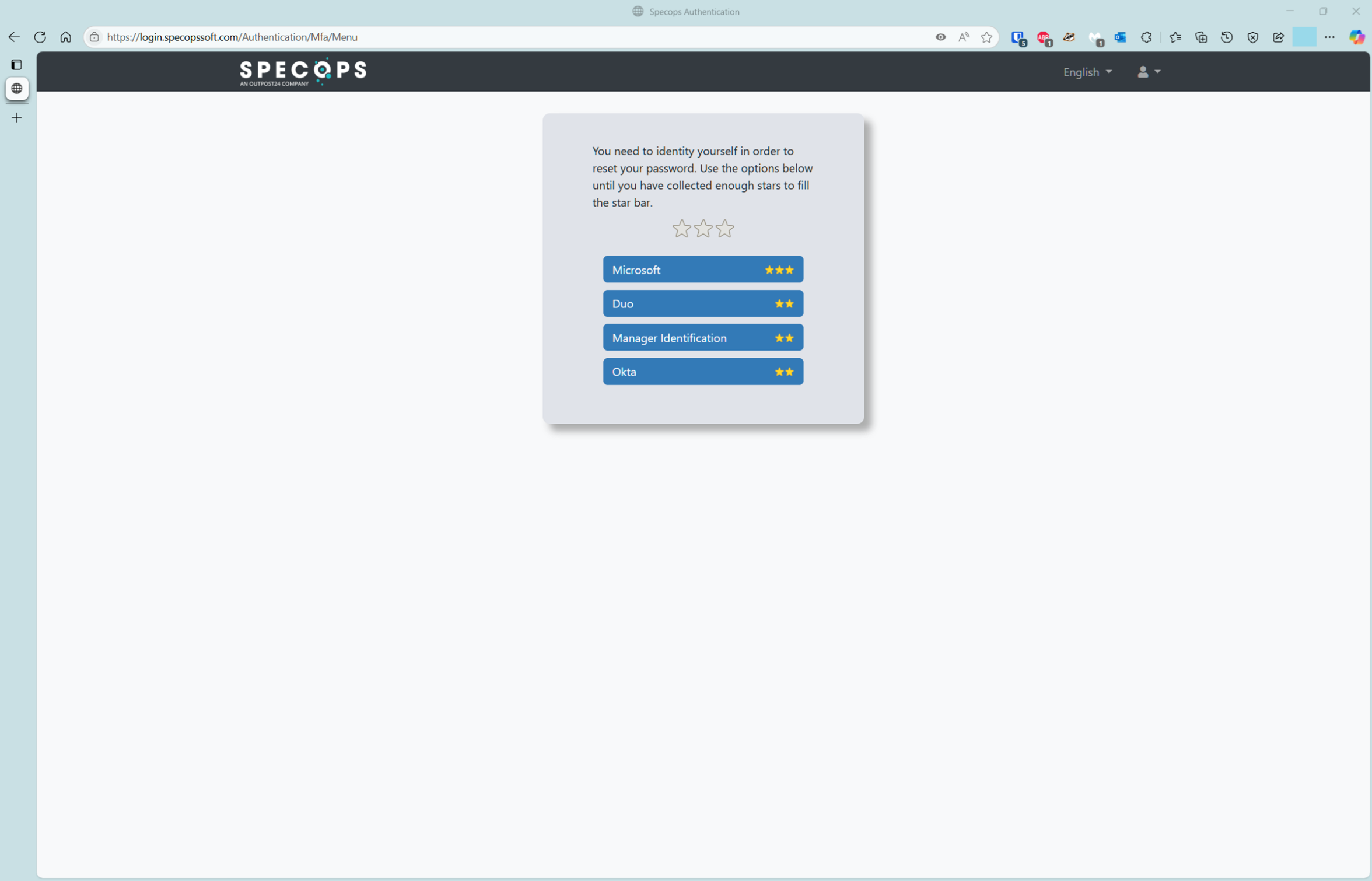
- Choose Microsoft as the MFA option
The user selects the Microsoft option from the list of available MFA options, which is defined by the Specops uReset administrator.
- Redirect to Microsoft Entra sign-in
The user is redirected to the Microsoft Entra sign-in page, and is presented with the option to Send a notification to their Microsoft Authenticator app. The user clicks Send notification to proceed.
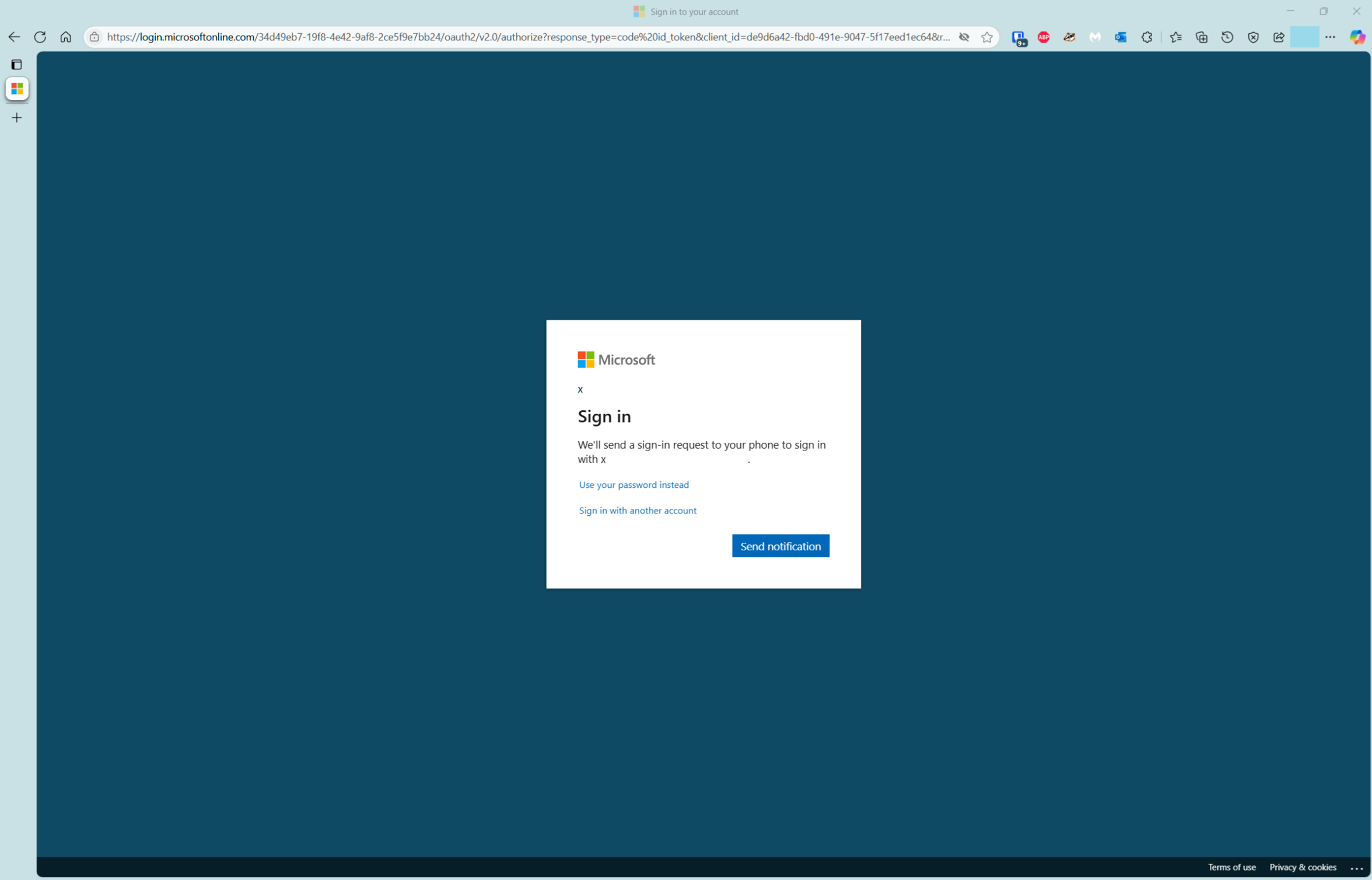
- Receive Authenticator app code
The user is then presented with a code to enter into the Microsoft Authenticator app to verify the push notification.
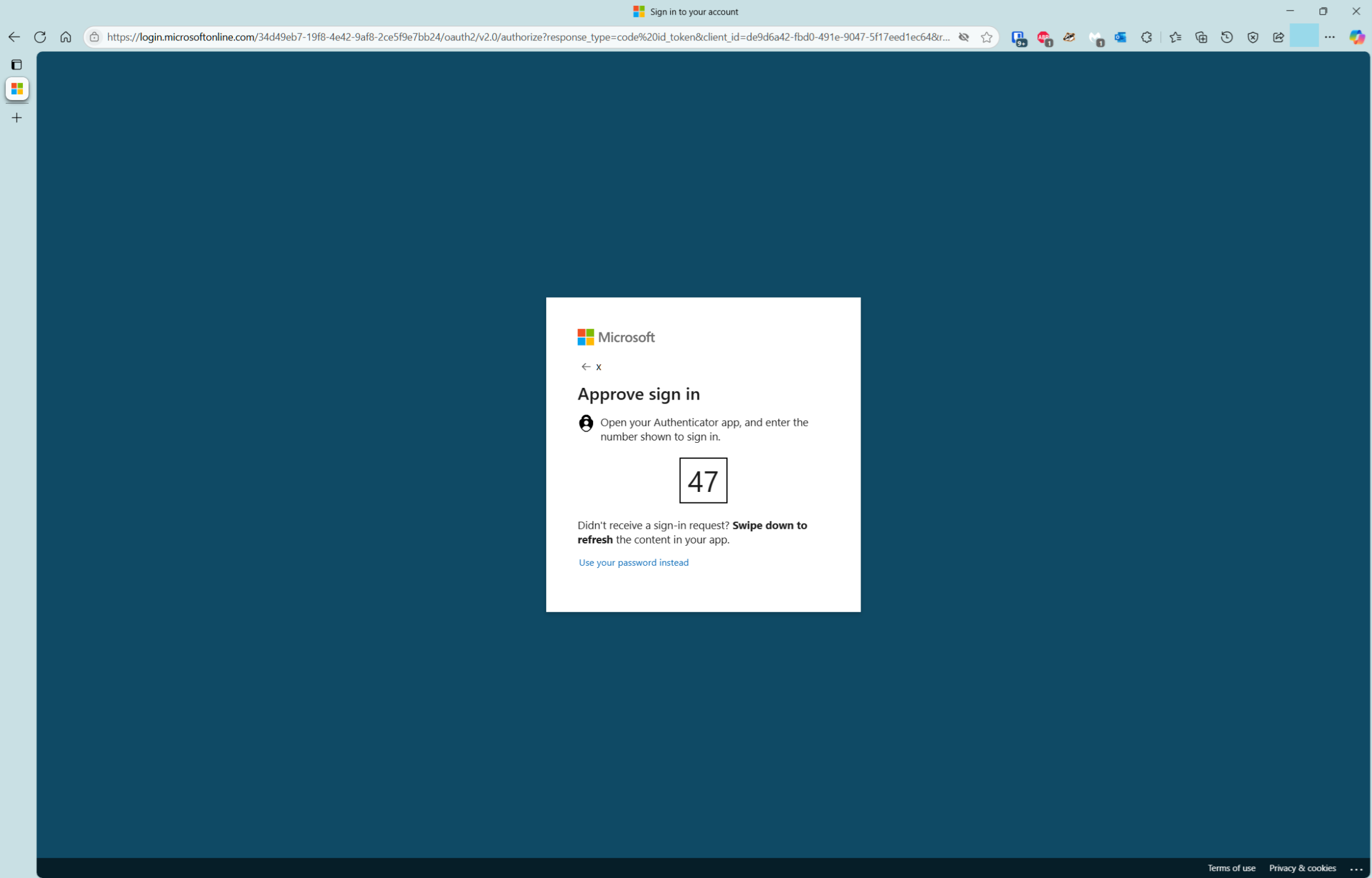
- Verify notification in Authenticator app
The user enters the code into the Microsoft Authenticator app to verify the push notification, then taps Yes to proceed.
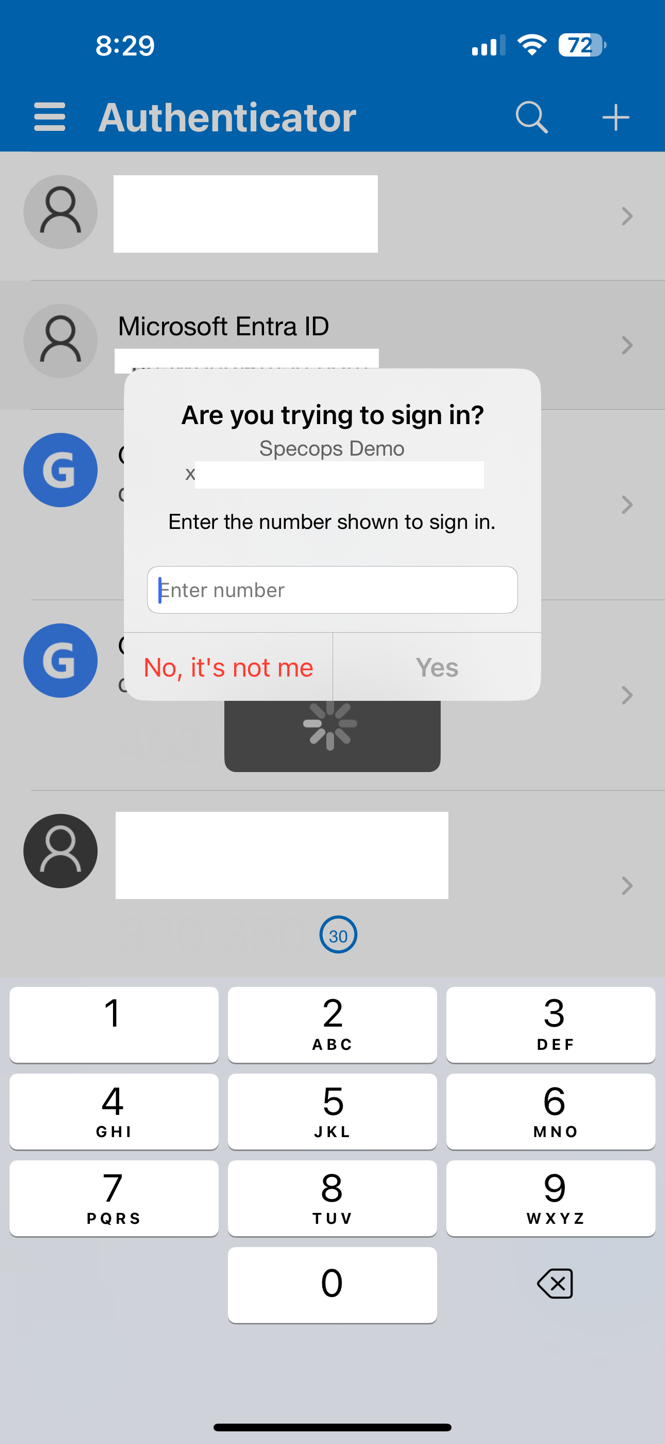
- Confirm with biometrics or PIN
The phone prompts for biometrics or PIN to verify the user’s identity to access the private key on the device, and the passwordless sign-in is complete.
- Reset password in Specops uReset
The user is redirected to the password reset page for Specops uReset, where the user can enter a new password to successfully complete the password reset.
Conditional access
For Entra customers that may have Conditional Access configured to not require MFA in certain scenarios, such as while on the corporate network, a new Conditional Access policy may be required to enforce MFA with Specops uReset and/or Secure Service Desk from any network or location.
Entra administrators can create a new Conditional Access policy to always require MFA with Specops applications.
- Sign in to https://portal.azure.com
- Browse to Microsoft Entra Conditional Access > Policies > New policy
- Name – Set a name for the policy, such as “Require MFA with Specops uReset”
- Assignments
- Users – Include > select “All users”
- Target resources – Include > Select resources > Select > search for and select the Azure app registration for Specops uReset, which may be a custom name, such as “Microsoft MFA for Specops uReset”
- Network – Include > select “Any network or location”
- Conditions – Locations > select “Any network or location” (This condition may be set automatically once the previous Network option has been set to “Any network or location”)
- Access controls
- Grant – Grant access > Require authentication strength > select “Passwordless MFA”
- Session – Can be left unconfigured
- The required Conditional Access policy may vary depending on other existing Conditional Access policies in the environment.
Note that Conditional Access cannot be configured to require passwordless sign-in for Specops uReset and/or Secure Service Desk only. Conditional Access policies are only evaluated after the initial authentication – As a result, authentication strength doesn’t restrict a user’s initial authentication. Suppose you want to require passwordless sign-in with Specops applications only. A user can still type in their password as the initial authentication method, so whether a user uses password+MFA or passwordless sign-in, as long as the Microsoft Authenticator notification is used at any point during the sign-in process, then the Conditional Access policy would be satisfied.
Find out more here: https://learn.microsoft.com/en-us/entra/identity/authentication/concept-authentication-strengths#limitations
Need support optimizing Entra MFA with Specops uReset and/or Specops Secure Service Desk?
If you have questions or are looking to expand your use of Microsoft Entra ID to better secure and simplify processes like self-service password reset and identity verification at the Service Desk, Specops is here to help. Our solutions, Specops uReset and Specops Secure Service Desk, integrate easily with Entra MFA to deliver a more secure and user-friendly experience. Get in touch for support here.
Last updated on November 11, 2025



