This website uses cookies to ensure you get the best experience on our website. Learn more

DragonForce: Inside the Ransomware-as-a-Service group
Table of Contents
The popularity of Software-as-a-Service (SaaS) has exploded over the past decade. The benefits for organizations are obvious – SaaS is scalable, cost-effective, and doesn’t need complex installation or maintenance. Gartner expects global spending on SaaS to reach $3 billion in 2025. So, is it any surprise that cybercriminals want a piece of the action? Ransomware-as-a-Service (RaaS) is the illegal but enterprising business model used by criminal groups such as DragonForce.
We’ll explore how the Ransomware-as-a-Service model works, explain who DragonForce are and how they operate, plus share some dark web screenshots of their disputes with other RaaS providers. We’ve also got some advice on how to avoid the initial breaches that lead to ransomware deployment.
What’s Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is where ransomware developers lease their malware to affiliates or customers, typically through dark web marketplaces. Instead of carrying out attacks themselves, the developers provide ready-made ransomware tools, user interfaces, technical support, and sometimes even negotiation services with victims. Affiliates carry out the attacks and the developers take a cut of the ransom payments. A prime recent example is the DragonForce RaaS group allegedly working with the Scattered Spider group to attack Marks & Spencer (M&S).
This model lowers the technical barrier to entry for cybercrime, enabling even those with limited hacking skills to launch ransomware attacks. It also makes ransomware more scalable and profitable, contributing to its rise as a major cybersecurity threat. For a cybercrime group, it carries all the same benefits as SaaS. Except the goal here is to extort organizations through ransomware, infecting their systems and encrypting their data until a ransom is paid.
Who are Dragonforce?
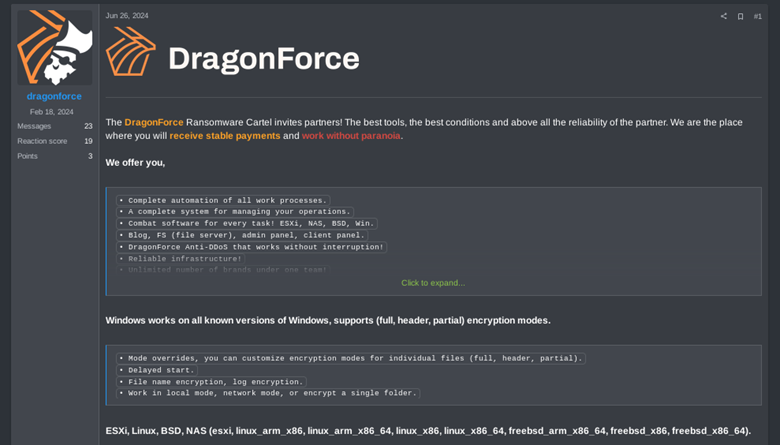
DragonForce is a relatively new ransomware group that first surfaced in August 2023, initially framing itself as a pro-Palestinian hacktivist collective before pivoting toward profit-driven operations. Its earliest ransomware payloads were forks of leaked LockBit builders, but it has since developed its own bespoke variants (drawing on Conti v3 code) to support Windows, Linux, ESXi and NAS targets. The group’s multi-extortion approach (combining encryption with data theft and public leaks) underscores its evolution into one of the more dangerous hybrid Ransomware-as-a-Service operations on the global stage.
Beginning in early 2025, DragonForce has aggressively targeted high-profile UK retailers (most notably Marks & Spencer, the Co-op, and Harrods) deploying its ransomware to encrypt networks, disrupt online orders and payment systems, and threaten the publication of customer and employee data. In the Marks & Spencer incident, affiliates reportedly used social-engineering attacks on service desks tied to Scattered Spider to gain initial access before unleashing DragonForce’s ransomware.
Beyond these headline UK incidents, DragonForce’s leak site history shows claims of dozens more victims. Earlier victims of its ransomware included the Ohio Lottery (2023), where over 600 GB of user data was stolen, and corporate targets such as Coca-Cola, Yakult and even the government systems of the island of Palau. In 2024, the group’s affiliates publicly listed roughly 93 distinct victims across various sectors and geographies, spanning Windows, Linux, ESXi and NAS environments.
Where are DragonForce based?
In their RaaS announcement, DragonForce have prohibited the use of their encryptor against CIS countries (Russia and allies). This could suggest DragonForce is a Russian group. However, the BBC says that “conversations with the Co-op hackers were carried out in text form but it is clear the hacker, who called himself a spokesperson, was a fluent English speaker.” In previous forum messages, we’ve seen DragonForce posting in both perfect Russian and English.
How does DragonForce’s RaaS model work?
Ransomware-as-a-Service (RaaS) outfits like DragonForce operate on a franchise model: core developers build and maintain the ransomware codebase (often forking or enhancing existing strains) and then lease access to affiliates. Affiliates gain access to a “white-label” affiliate portal where they can customize payloads, select encryption parameters, choose branding (or disguise DragonForce under another strain), and manage multi-extortion campaigns through dedicated leak sites. DragonForce developers handle the backend infrastructure (C2 servers, payment gateways, negotiation support).
Once recruited, affiliates target organizations to gain initial access via techniques such as:
- Phishing, smishing, or vishing
- Exploitation of unpatched vulnerabilities
- Compromised credentials – stolen or purchased from other threat groups
- Social engineering help desks to reset passwords and bypass MFA
After establishing a foothold, they deploy loaders like SystemBC to exfiltrate sensitive data quietly, disable or delete security tooling, and then unleash the encryptor to lock down files. Finally, the group uses “double-extortion,” threatening to both withhold decryption keys and publicly leak stolen data on dedicated leak sites. This pressures victims to negotiate ransom payments (usually in cryptocurrency) under the threat of reputational and operational damage.
How do DragonForce operate on the dark web?
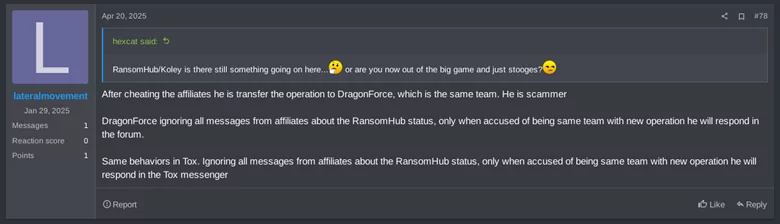
DragonForce started out in October 2023, but it was June 2024 when they announced the launch of their Ransomware-as-a-Service project in RAMP (dark web marketplace) to potential affiliates. Initially you could think about DragonForce as just another RaaS group, but interestingly they carried out the compromise of another ransomware project, Eldorado (aka BlackLock) and likely also compromised RansomHub (explored in detail in the next section).
DragonForce are also known for more complex “double-extortion” methods. This involves going beyond just deploying ransomware and calling victims while recording the conversation. The recordings are posted in their data leak site to increase the reputation damage and pressure on the victim. For example, DragonForce recently directly contacted the BBC to say that their compromise of British retailer the Co-op was bigger than the retailer was letting on.
DragonForce & RansomHub: Infighting among RaaS providers?
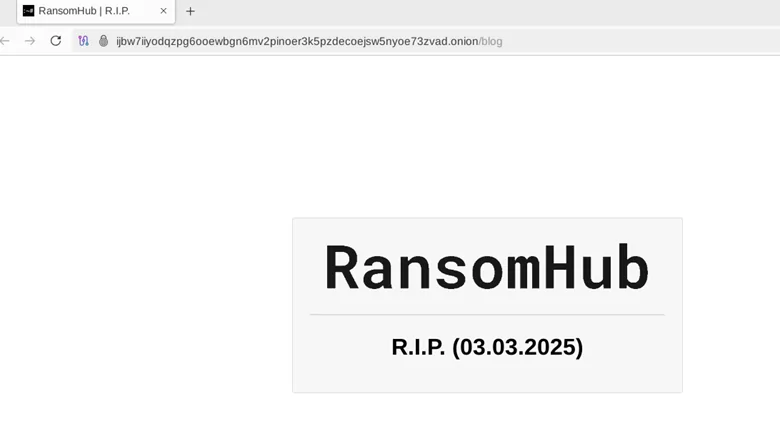
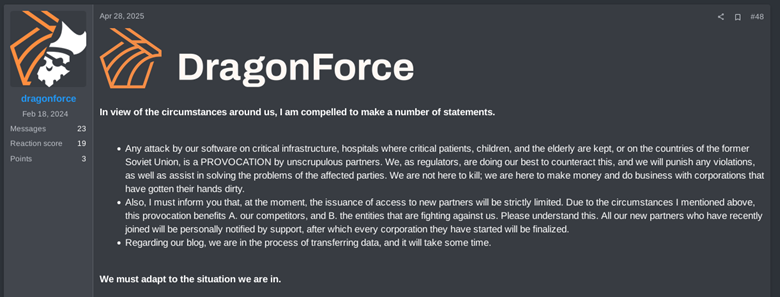
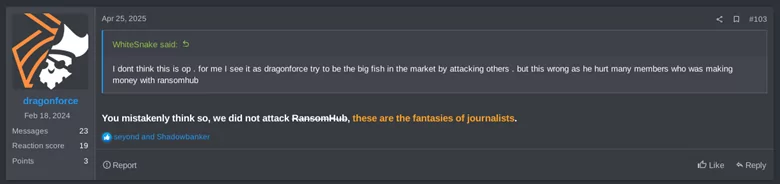
On April 1st, 2025, RansomHub’s data leakage site (DLS) stopped working and the managers stopped answering, according to complaints posted by affiliates in underground forums. On April 2nd, 2025, DragonForce published an announcement “suggesting” RansomHub should join them and move to their infrastructure, in what can be interpreted as a mockery for their infrastructure being down.
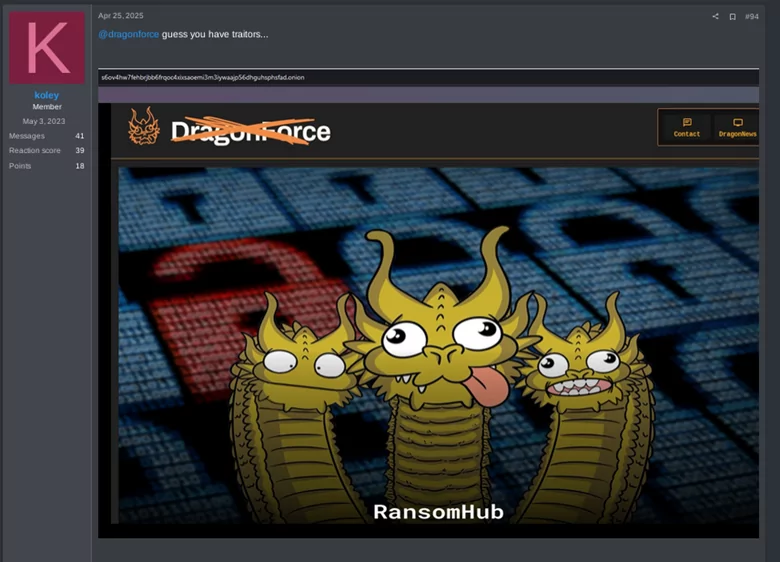
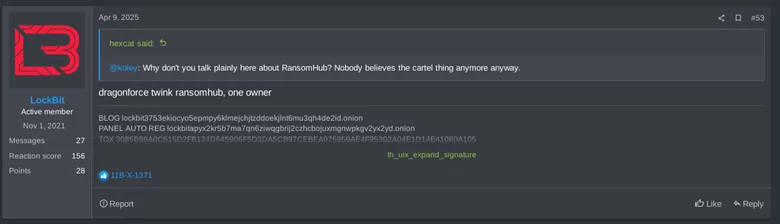
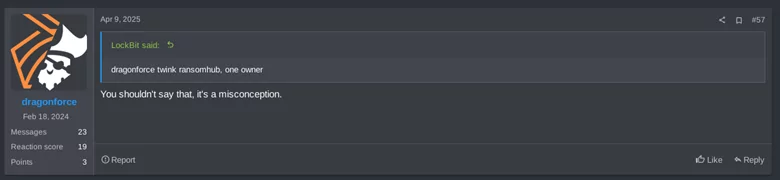
On April 23rd, 2025, “koley“, the spokesperson of RansomHub, reappeared in the forum claiming to have suffered an attack coming from the state, and exposed an alleged traitor. A couple of days later, on April 25th, koley shared an image of DragonForce’s DLS being compromised and defaced with a message that suggests that the attack was carried out from within by “traitors”.
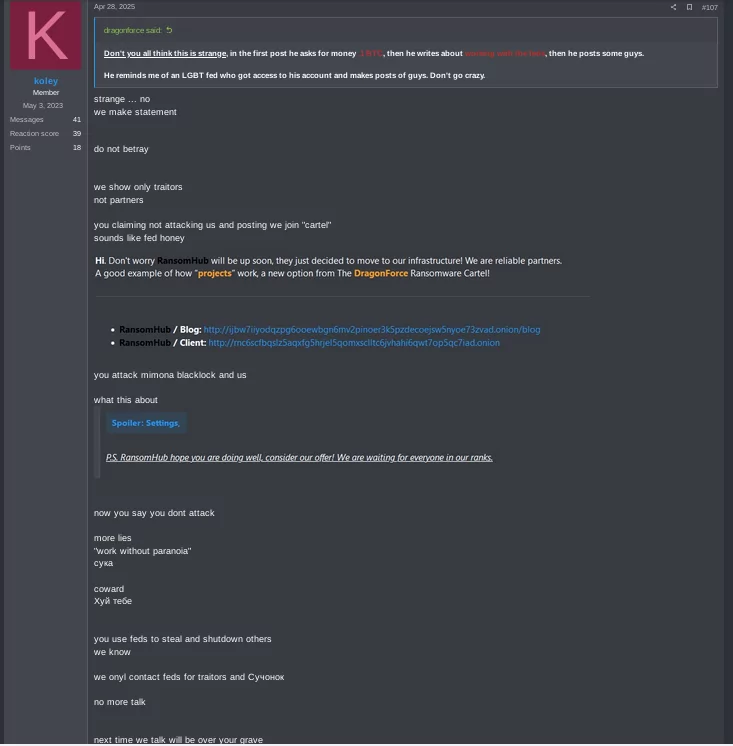
A post from DragonForce on April 28th on the thread where they advertised their RaaS, claims that they are on a pause when it comes to “accepting collaborators” because of the recent events. This idea would fit with the fact that they were compromised by a “traitor”.
What’s next for DragonForce and RansomHub?
Based on current underground forum rumors, there are a couple of possibilities here:
- That RansomHub did an exit scam and they are the same as Dragonforce
- Dragonforce and RansomHub are more enemies than allies
Another possibility is that DragonForce is compromising other RaaS providers. They compromised BlackLock in the past and some rumors say they also compromised Everest and now RansomHub.
There have also been suggestions that DragonForce is collaborating with federal agents to compromise other RaaS providers. koley’s messages seem to indicate that they believe DragonForce was responsible for the attack on them, just like they were responsible for the attack on “Eldorado” (aka BlackLock/Mamona), and that they were collaborating with law enforcement to shutdown others.
koley also said “we only contact feds for traitors and bastards”. This means RansomHub could have collaborated with law enforcement sometime. In addition to this conflict with DragonForce, there are other users who insinuate that RansomHub’s infrastructure was taken down by Russian law enforcement because of them attacking Russian companies or institutions.
Reduce the risk of initial access to your organization
Easy-to-guess and stolen credentials are some of the easiest ways attackers can get initial access to your environment to deploy ransomware. Strong password security is your first line of defense against the credential-theft and brute-force methods attackers use to gain a foothold in your environment.
Specops Password Policy makes it simple to enforce long, complex passwords (or passphrases) that are unique to each account, dramatically increasing the time and resources an attacker needs to crack or guess them. Your Active Directory will also be continuously scanned against our database of over 4 billion unique breached credentials. Book a free demo today.
Critically, strong password policies need to be paired with effective multi-factor authentication (MFA) such as Specops Secure Access. Even if an attacker phishes or brute-forces a password, MFA adds a vital second barrier. In combination, these measures close off the most common initial access vectors for ransomware operators. This forces them to move on to softer targets or buys defenders precious time to detect and respond before encryption or data exfiltration can occur. Try Specops Secure Access for free.
Concerned about the risk of ransomware? Talk to us today.
Last updated on November 11, 2025