This website uses cookies to ensure you get the best experience on our website. Learn more
[New research] Heatmap of 10 million breached passwords: 98.5% are weak
Table of Contents
The Specops research team has analyzed 10 million random passwords from the 1 billion+ breached password list used by Specops Password Auditor. These are all real compromised passwords that have been captured by Specops, which you can scan your own Active Directory against right now. Our team have mapped out the most common length and complexity combinations in a visual heatmap, and found that only 1.5% of these 10 million passwords could be considered ‘strong.’
The findings show that organizations are still allowing users to create weak passwords that could be used as simple attack routes for hackers. This research coincides with the latest addition of over 13 million compromised passwords to the Specops Breached Password Protection service. These passwords come from a combination of our honeypot network and threat intelligence sources.
Darren James, Senior Product Manager, had this to say: “Despite years of training, many users still choose weak, easily guessed combinations that cybercriminals can crack in seconds. To bring this risk into sharp relief, our research team analyzed 10 million real-world passwords and plotted them on a heatmap measuring strength by both length and complexity. This visual ‘strength landscape’ show how organizations need to adjust their password policies to move end users’ Active Directory passwords away from the zone of risk into the zone of security.”
How did we define a strong password for this analysis?
The practical rule we used to define a ‘strong’ password for our 10 million-password heatmap is as follows:
Strong password = at least 15 characters in length and at least two different character classes
Why “15+ characters”?
- Exponential growth of combinations. Every extra character multiplies the keyspace by the size of your chosen alphabet.
- A 15-character password using only lowercase letters has 26¹⁵ ~ 1.7 × 10²¹ possibilities.
- Jump to 16 characters, and you get 26¹⁶ ~ 4.4 × 10²² possibilities – a 26x increase in brute-force work required to crack.
- Even with GPU- or ASIC-powered rigs churning through trillions of guesses per second, pushing beyond 15 characters pushes the expected crack time from hours into years or centuries. Once you introduce mixed character classes, a long hashed password can take billions of years to crack.
Why “At least two character types”?
- Avoiding single-class shortcuts. A long password of 15 identical-class characters (e.g. all lowercase) is easier to crack than one that mixes in digits or symbols.
- Marginal cost vs. security gain. Adding, say, digits to a lowercase alphabet expands its size from 26 to 36 characters. This boosts the keyspace by (36/26)¹⁶ ~ 2.5× on top of your length gain.
- Defense-in-depth. Even if an attacker optimizes a word-list or mask-based attack (targeting common patterns), introducing mixed classes forces them back into full brute-force territory.
- By adopting 15+ length and mixed character sets, you’re not just ticking a compliance checkbox – you’re shifting your password into a region where even state-of-the-art cracking farms can’t reach you within any realistic timeframe (see our SHA256 research for detailed cracking tables).
Keyspace calculations for 15-character passwords
| Character set | Size of set | Total combinations (Keyspace) | How long to crack? |
|---|---|---|---|
| 15 characters password of lowercase only (a–z) | 26 | 26¹⁵ ~ 1.68 × 10²¹ | Easily cracked with GPUs in days or weeks. |
| 15 characters password of lowercase + uppercase (a–z, A–Z) | 52 | 52¹⁵ ~ 2.53 × 10²⁵ | Much harder to crack, but still feasible over time. |
| 15 characters password of alphanumeric (a–z, A–Z, 0–9) | 62 | 62¹⁵ ~ 7.70 × 10²⁶ | Very strong passwords for most practical use cases. |
| 15 characters password of all printable characters (a–z, A–Z, 0–9, symbols) | 94 | 94¹⁵ ~ 2.25 × 10²⁹ | Approaches brute-force impracticality. |
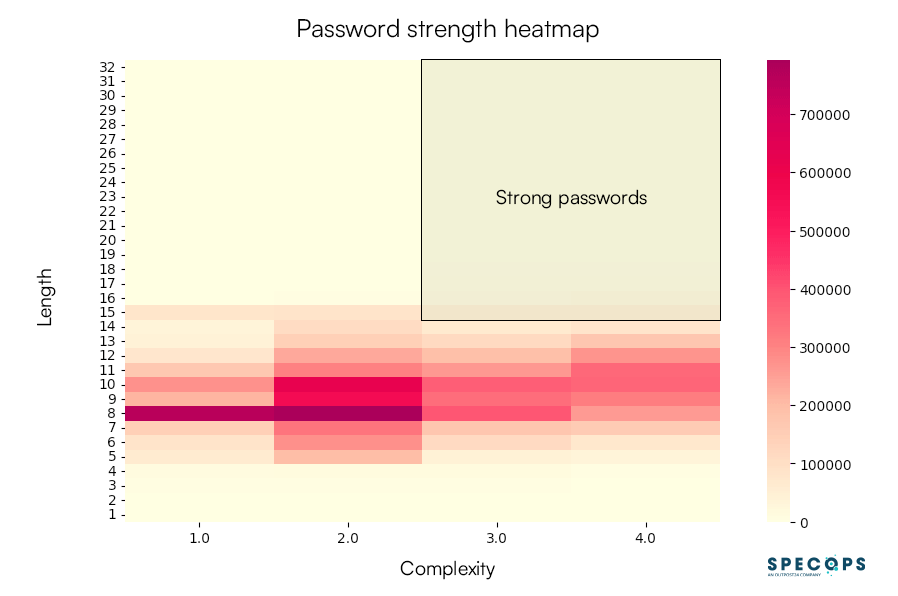
Password strength heatmap
The heatmap below shows that out of the 10 million passwords analyzed, only 1.5% sit in the ‘strong passwords’ zone that organizations should be aiming for. These passwords were over 15 characters in length with at least three different character types. If your Active Directory contains only passwords like this, your end users would be generally safe from brute force attacks.
If we lower the criteria down to an ‘okay’ password that’s over 12 characters in length with at least two different characters, then 16% of the analyzed passwords would meet that criteria. So in other words, 84% of these unique breached passwords (from real world end users) should be considered weak and vulnerable to brute force attacks.
As you can see from the dark red area of the heatmap, the most common type of password is 8 characters in length with two character types (7.9% of all passwords). This is closely followed by 8 characters in length with a single character type (7.6% of all passwords). Passwords 8 characters and under (regardless of complexity) can be cracked in hours by brute force techniques.
Password length trends
As the chart below shows, only 3.3% of the passwords in this analysis were over 15 characters in length. Enforcing longer passwords in your Active Directory is the easiest way to increase their strength. A 12-character password using a 94-symbol set has ≈ 94¹² possibilities. But jump to 16 characters, and you get ~ 94¹⁶ – a 94⁴ ~78 million-fold) increase in brute-force work for just four extra characters.
To make long passwords easier for end users to remember, we’d recommend encouraging the use of passphrases. Users are more likely to remember and correctly enter a meaningful 20-character phrase (e.g. “SunsetCoffeeMaroonReview”) than a shorter string riddled with odd symbols and capitalization (e.g. “!x9#A7b!”). This reduces help-desk resets and “password fatigue.”
Password complexity trends
Brute-force time grows exponentially with each additional character and character class (uppercase, digits, symbols). But if your password uses only one class (say lowercase letters), all that entropy greatly reduces. A 6-character lowercase password has just 26⁶ (~ 300 million) combinations, which is crackable in seconds.
The heatmap shows that 55.3% of passwords in this analysis had two character types or less. Adding more complexity is an easy way to add password entropy and make brute force techniques less effective. But in recent years, updated NIST password guidelines have advised to focus more on length when building your password policy. In practice, you’ll get far more protection from pushing your password length into the 16–20+ character range than from increasing complexity.
Find weak and compromised passwords in your network today
This month’s update to the Breached Password Protection service includes the addition of just under 6 million compromised passwords to the list used by Specops Password Auditor. The list also includes the 10 million breached passwords we analyzed in this study. You can find how many of your end users’ passwords are either compromised or identical with a read-only scan of your Active Directory from Specops Password Auditor. You’ll get a free customizable report on password-related vulnerabilities, including weak policies, breached passwords, and stale/inactive accounts. Download your free auditing tool here.
Why are weak passwords a problem?
- Easy entry point for attackers: Weak passwords are the low-hanging fruit that automated cracking tools exploit first. Once an attacker gains one set of valid credentials, they can pivot through the network, escalate privileges, and exfiltrate sensitive data – all without tripping more sophisticated perimeter defenses.
- Amplified impact of password reuse: With an average employee juggling hundreds of logins, many simply recycle passwords across systems. A breach of an externally facing service then opens doors to internal applications, databases, and even administrative consoles.
- Regulatory and compliance fallout: Data-protection regulations like GDPR, HIPAA, and PCI DSS mandate “appropriate” access controls. Weak or reused passwords are a direct violation, inviting hefty fines, mandatory audits, and potential legal liability.
- Vulnerability to brute-force attacks: A GPU-powered rig can attempt upwards of 100 billion SHA-1 guesses per second; cloud services amplify that into the trillions. What once took days or weeks on a CPU now collapses to minutes for sub-8-character passwords, and under an hour even for many 10-character lowercase strings.
- Diminished return on salting and hashing: Proper salting and strong hash algorithms (shown in our research into bcrypt) slow down each guess, but they can’t turn a weak password into a strong one. An 8-character password with minimal complexity still falls in the “easy” zone on our heatmap (even if hashed and salted) because the attacker’s time-cost per guess remains lower than the total entropy.
- Distributed attacks and botnets: Attackers often distribute their workload across thousands of compromised endpoints, shifting brute-force traffic to evade rate-limiting and intrusion detection. This “botnet cracking” can test passwords against online services at scale—making weak credentials especially vulnerable to lockout-bypass and credential-stuffing campaigns.
Continuously block weak passwords and compromised passwords
We’ve shown that most of the passwords in this analysis were weak – but there were strong ones in the data too. That’s because even passwords that could be considered ‘strong’ can be stolen by malware or compromised through password reuse. Blocking weak passwords is important but it’s only half the battle.
Specops Password Auditor offers a great starting point for assessing your current password risks, but it’s only a snapshot. With Specops Password Policy and Breached Password Protection, organizations can continuously protect themselves against over 3 billion more known unique compromised passwords (4 billion in total).
Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. It also includes passwords found on breached password lists on the dark web and elsewhere. Breached Password Protection continuously scans your Active Directory for breached passwords and allows you to alert end users with customizable messaging that helps reduce calls to the service desk.
Interested in seeing how this might work for your organization? Have questions on how you could adapt this for your needs? Contact us or see how it works with a demo or free trial.
Last updated on November 11, 2025



