This website uses cookies to ensure you get the best experience on our website. Learn more
[New research] Cracking bcrypt: Is new-gen hardware and AI making password hacking faster?
Table of Contents
Almost two years ago, the Specops research team analyzed how long it took to crack passwords hashed with the bcrypt algorithm. Two years is a long time in cybersecurity, so we’re revisiting the research with newer, more powerful hardware, to create a new table of bcrypt cracking times. The reason for this is two-fold: the AI boom causing a glut of consumer hardware, as well as the arms-race in consumer graphics performance.
The focus on compute power for both consumers and enterprises whether for general purpose compute (GPGPU) or training LLMs has caused arguably all three major graphics vendors to focus more heavily on compute performance than they may have in the past. This shows in the performance of Nvidia’s recent 50-series, as well as AMD’s upcoming transition to the ‘UDNA’ architecture. We’ve investigated what this boom and renewed focus on compute means for the difficulty of cracking a leaked password hash, and the future security of passwords.
This research coincides with the latest addition of over 70 million compromised passwords to the Specops Breached Password Protection service. These passwords come from a combination of our honeypot network and threat intelligence sources.
What’s driving the increase in computing power?
Post the release of the RTX 50-series cards, the availability and affordability of high-performance computing hardware has further increased, evolving the discussion of what should be considered a strong password. This increase of cheap powerful hardware is generally driven by the AI boom, and the reasonable affordability of high-power consumer GPUs.
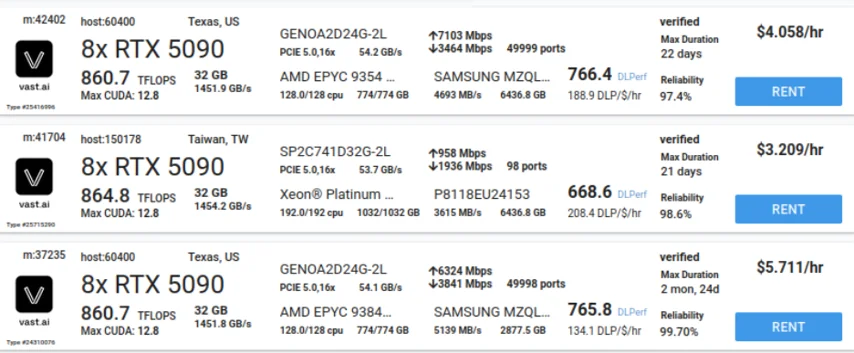
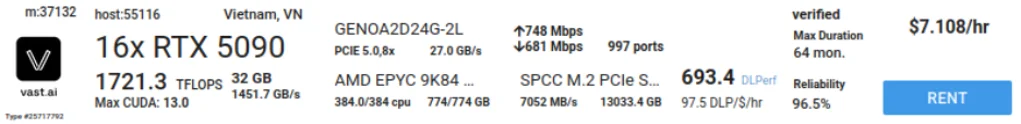
Typically, an organization will co-locate a machine with a number of consumer-level GPUs such as the 5090 and use it to train their models. When they’re not doing re-training, they list it on a service such as vast.ai for users to rent and in turn train their own models (or in our case, to crack hashes). This allows one to monetize the downtime, even if it is only a few dollars an hour, to offset the cost of the hardware. This hardware can range from 8-16 RTX 5090s to 8 Nvidia H200s.
Methodology
What hardware did we use?
AI-specific hardware such as the H200s do not provide a benefit in password cracking, as we don’t need the volume of memory they provide, we simply need the hashrate (a measure of a computer’s or network’s computational power, expressed as the number of hash calculations it performs per second). A reasonable expectation for the hardware being used to attack a given set of leaked hashes is now 5090-series hardware. This hardware costs somewhere in the ballpark of $5/hr to rent:
As such, these calculations were performed using 8xRTX 5090s for the example hardware, with the expectation that hackers could be using more (there are instances with 16 available in a single host).
Counter to previous time to crack tables, we didn’t use the Hashcat benchmark functionality to determine the hashrate that we based the table on. As best practices and hardware evolves, a cost factor of 5 (the cost factor used for Hashcat’s m3200 benchmark) is no longer a reasonable expectation of complexity. We’ll be discussing cost factors of 10+; that is iterations of 1024 and up. This better reflects a strong implementation at the time of writing in 2025.
Generating the hashes
A sample of 750,000 hashes was taken from the well-known wordlist rockyou.txt and hashes were generated of cost factors 10, 12, and 14. This can take some time, since as the cost factor goes up making the hashes harder to crack, this in turn makes the hashing process slower. The higher iterations hit you on both ends.
Deciding which cost factor to use for a given implementation necessitates considering how often you’ll need to hash the records in question and how much time can be spared to do so. For example, the sample data was generated on a reasonably powerful workstation. Generating the cf12 hashes took 1.2 hours; generating cf14 hashes (from the same data) takes nearly 5 hours.
After the data was generated, a cloud instance of 8xRTX 5090 GPUs was spun up, the data was transferred to the host along with a copy of rockyou.txt, and attacks were performed to produce an expected hashrate. Both mask attacks and wordlist attacks were performed to provide sample data. This data is then used to generate the expected time to crack a given password via brute force. These hashrates were then used to produce the time-to-crack for a given password complexity.
What did we find?
Over the two years since our previous bcrypt cracking writeup, the colossal investment in AI infrastructure by various organizations and financial backers (see: OpenAI, Anthropic) have improved the availability of heavy compute hardware by leaps and bounds. While previously one could expect to be under attack from a set of something like the RTX 4090, the next generation of flagship cards are more available and faster than ever: an RTX 5090 is approximately 65% faster when tackling bcrypt (an intentionally slow hashing algorithm that does not lend itself to GPU compute).
However, we need to take into account that we also increased the cost factor for this piece of research, which would slow hacking attempts down. While high cost-factor bcrypt hashes do require a great deal of compute and time to crack, we can see that the availability of more powerful hardware is balancing it out. All of this extra overhead can then be used to weaken stronger hashes that would have been impossible to crack with less powerful hardware.
As you can see in the below table, short, non-complex passwords can still be cracked relatively quickly, highlighting the huge risks of allowing users to create weak (yet very common) passwords such as ‘password’, ‘123456’, and ‘admin’. However the high cost factor of bcrypt makes longer passwords extremely secure against brute force attacks thanks to its slow-working hashing algorithm. Once a combination of characters are used in passwords over 12 characters in length, the time to crack quickly becomes a near-impossible task for hackers. This shows the value of enforcing longer passwords.
| Number of characters | Numbers Only | Lowercase Only | Upper and Lower | Number, Upper, Lower | Number, Upper, Lower, Symbols |
|---|---|---|---|---|---|
| 4 | Instantly | Instantly | Instantly | Instantly | 17 minutes |
| 5 | Instantly | 2 minutes | 81 minutes | 194 minutes | 26 hours |
| 6 | Instantly | 66 minutes | 70 hours | 200 hours | 102 days |
| 7 | 2 minutes | 29 hours | 151 days | 517 days | 317 months |
| 8 | 22 minutes | 31 days | 262 months | 88 years | 2449 years |
| 9 | 212 minutes | 797 days | 1117 years | 5437 years | 230158 years |
| 10 | 36 hours | 690 months | 58064 years | 337125 years | 21634796 years |
| 11 | 352 hours | 1495 years | 3019333 years | 20901760 years | 2033670809 years |
| 12 | 147 days | 38864 years | 157005327 years | 1295909100 years | 191165056.1k years |
| 13 | 49 months | 144351 years | 8164277025 years | 80346365k years | 17969516m |
| 14 | 41 years | 25912012 years | 424542405k years | 4981474577k years | 1689134436m years |
| 15 | 402 years | 673712313 years | 22076205m years | 308851423m years | 158778637b years |
| 16 | 4017 years | 17516520142 years | 1147962664m years | 19148789b years | 14925192t years |
| 17 | 40168 years | 455429524k years | 59694059b years | 1187224873b years | 1402968036t years |
| 18 | 401675 years | 11841168m years | 3104091044b years | 73607943t years | 131878996q years |
| 19 | 4016746 years | 307870358m years | 161412735t years | 4563692412t years | 12396626Q years |
| 20 | 40167451 years | 8004629308m years | 8393463q years | 282948930q years | 1165282803Q years |
| 21 | 401674504 years | 208120363b years | 436460034q years | 17542834Q years | 109536584s years |
| 22 | 4016745033 years | 5411129413t years | 22695922Q years | 1087655686Q years | 10296439S years |
What can we learn from brute force calculations?
It’s true that expecting an attacker to attempt to brute force a given dataset is unrealistic. Crackers will typically use a variety of attacks to attempt to crack a given set of hashes. This can range from dictionary attacks and rule-based attacks, to association attacks. They may generate specific wordlists based on the source of the hashes, such as scraping a corporate website with a tool like Cewl, to provide a targeted wordlist.
However, brute force gives a baseline to perform calculations when discussing the raw compute provided by a given set of hardware, as well as a baseline to perform strength calculations from. It’s important to be mindful of how attacks are performed, and attempt to build well-founded password policies that reduce the risk of passwords being guessable via simple wordlist and rule attacks.
This can come in the form of length and complexity requirements at a basic level, while ranging to custom blocked dictionaries and breached password corpuses – such as the functionality provided by Specops Password Policy combined with Specops Breached Password Protection. When possible, a combination of these functionalities should be used to make it as hard to generate a valid candidate as possible. As shown by the new cracking table, entropy is crucial, and length is an easy-to-remember source of password entropy.
Writing policy rules when expecting multiple 5090s to attack any leaked hashes
In order to protect against this kind of attack, there are a number of settings that can be configured within Specops Password Policy that will assist in making it more difficult to crack, should a bcrypt hash leak (whether from an internal system, or from a third party). As demonstrated in the cracking table, optimally an organization should be implementing a combination of protections, such as:
- A minimum length of 18
- Multiple character classes required, optimally: upper, lower, digits and special characters
- Enable passphrases with minimum length 18 and multiple character classes when possible
- Implement a custom dictionary that blocks words relevant to your organization, especially company name and product names; CeWL can be useful in determining a blocklist when run against public company resources
- Implement Specops Breached Password Protection (optimally Breached Password Protection Complete)
Can bcrypt hashing prevent password compromise?
As the cost factor (and number of rounds) increases, both the cost (and required computational power) of cracking, and hashing the initial password increases. Weighing this cost when implementing any authentication system is necessary to determine what hashing algorithm should be used; whether that’s a high round bcrypt, or something like argon2. A cost factor of over 10 increases the security of any password policy that is implemented, preferably in accordance with NIST 800-63B.
However, if the attacker has the password in question, whether due to re-use, or the password directly being leaked through infostealers, or another exploitation method this time becomes functionally 0 since the attacker can simply use the given password. No amount of complex hashing algorithms is a replacement for good security hygiene and implementing strong password policies through Specops Password Policy, as well as using a breached corpus such as Specops Breached Password Protection to prevent re-use of passwords across accounts. It’s now more important than ever to defend against infostealers leaking credentials.
Time to crack: Known compromised passwords
| Number of characters | Numbers Only | Lowercase Only | Upper and Lower | Number, Upper, Lower | Number, Upper, Lower, Symbols |
|---|---|---|---|---|---|
| 6 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 7 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 8 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 9 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 10 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 11 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 12 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 13 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 14 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 15 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 16 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 17 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 18 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 19 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 20 | Instantly | Instantly | Instantly | Instantly | Instantly |
Find weak and compromised passwords in your network today
This month’s update to the Breached Password Protection service includes the addition of more than 70 million compromised passwords to the list used by Specops Password Auditor. You can find how many of your end users’ passwords are either compromised or identical with a read-only scan of your Active Directory from Specops Password Auditor.
You’ll get a free customizable report on password-related vulnerabilities, including weak policies, breached passwords, and stale/inactive accounts. Download your free auditing tool here.
Continuously block weak passwords and compromised passwords
Specops Password Auditor offers a great starting point for assessing your current password risks, but it’s only a snapshot. With Specops Password Policy and Breached Password Protection, organizations can continuously protect themselves against over 4 billion known unique compromised passwords.
Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. It also includes passwords found on breached password lists on the dark web and elsewhere. Breached Password Protection continuously scans your Active Directory for breached passwords and allows you to alert end users with customizable messaging that helps reduce calls to the service desk.
Interested in seeing how this might work for your organization? Have questions on how you could adapt this for your needs? Contact us or see how it works with a demo or free trial.
Last updated on September 19, 2025