This website uses cookies to ensure you get the best experience on our website. Learn more
Enable Microsoft Entra Password Protection (formerly Azure AD Password Protection) in a hybrid environment
Table of Contents
With default Active Directory password policies, many organizations find that users create weak, easily guessed, or incremental passwords that attackers can easily compromise. Using Microsoft Entra Password Protection (formerly Azure AD Password Protection), organizations can have an additional layer of security for users’ passwords.
The good news is you don’t need to abandon on-premises Active Directory to implement stronger password policies or to block users from using breaching passwords. We’ll walk through how to enable Microsoft Entra Password Protection for your on-premises environment and where you can choose to augment its capabilities.
What is Microsoft Entra Password Protection (formerly Azure AD Password Protection)?
The Microsoft Entra Password Protection solution from Microsoft allows you to enforce the default global banned password lists defined in Entra ID (formerly Azure AD) in on-premises Active Directory Domain Services (AD DS) environments. You can also choose to create a custom banned list. The Microsoft security team analyzes Entra ID security data to add new weak or compromised passwords to the global ban list and apply it to all password change or reset operations.
When users change or reset their passwords, the password is checked using the Microsoft Entra Password Protection solution to ensure they are not found on the global banned password list defined in Entra ID. It allows organizations to define password filter lists in Entra ID and have these applied to on-premises AD DS environments in addition to their Entra ID tenant.
What’s the benefit of doing this? It’s an attempt to solve the age-old problem with end users using the same passwords for multiple accounts, including personal accounts. Users tend to create weak passwords and then exacerbate the risk of their credentials being compromised by reusing these passwords for personal devices and applications. Even passwords that may meet the traditional complexity requirements of Active Directory Domain Services (AD DS) password policies can still be weak and easily guessed with common “leetspeak” transformations. Multiplied across many end users, this creates significant organizational risk.
Enabling on-premises Microsoft Entra Password Protection
If their environments are hybrid prior to implementing Microsoft Entra Password Protection, organizations can extend the password protection to their on-premises AD DS environments with the following steps:
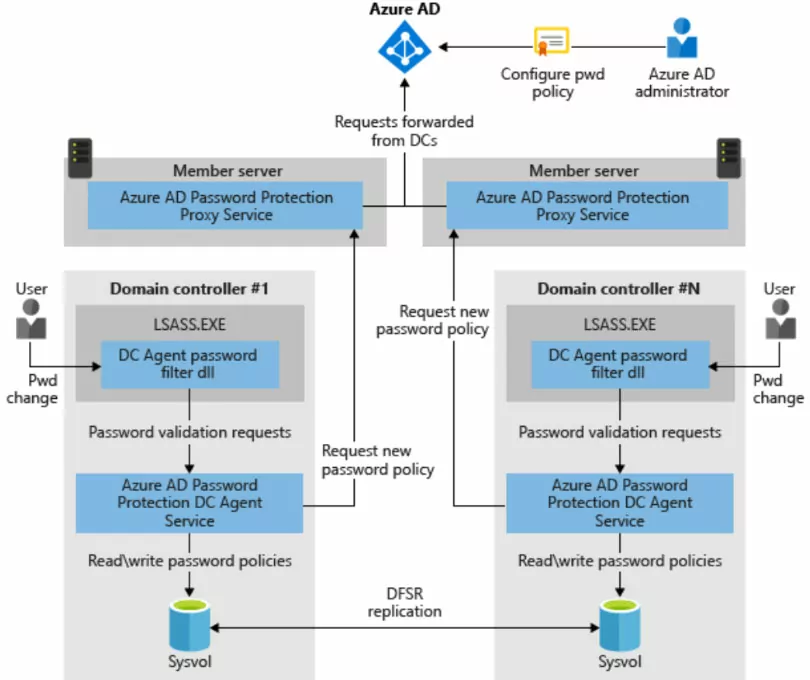
- The Microsoft Entra Password Protection Proxy service instance is advertised to on-premises domain controllers in the forest by creating a serviceConnectionPoint object. This object is created in the AD DS environment.
- The domain controller Agent service for Microsoft Entra Password Protection also creates a serviceConnectionPoint object in Active Directory. It uses this object for reporting and diagnostics operations.
- The agent installed on each domain controller initiates the download of new password policies from Entra ID. The forest is queried to find the Microsoft Entra Password Protection Proxy service using the serviceConnectionPoint objects.
- Once found, the domain controller agent sends a password policy download request to the proxy service. The proxy sends the request up to Entra ID. Then it returns the response to the domain controller Agent service.
- Once the domain controller Agent service receives a new password policy from Entra ID, the policy is stored in a dedicated folder at the root of its domain SYSVOL folder. The domain controller Agent service also monitors this folder in case newer policies replicate from other domain controller Agents in the domain.
- The domain controller Agent service requests a new policy at the service startup. After the DC Agent service is started, it checks hourly the age of the current policy it has available. If the policy is older than an hour, the domain controller Agent requests a new policy from Entra ID via the proxy service, as described previously. If the policy is within the hour threshold, it continues to use the existing policy.
- When a domain controller receives password change events, the cached policy determines if the new password is accepted or rejected.
Microsoft Entra Password Protection on-premises limitations
There are a few limitations to note with the Microsoft Entra Password Protection on-premises solution. Note the following considerations you need to make:
- Microsoft Entra Password Protection on-premises cannot be applied to a subset of users. It is a global solution, and all users receive equal security benefits.
- It does not validate existing passwords after it’s installed. It can only enforce password policy on cleartext passwords during the password change or set operation.
- Licensing – you must have a valid Entra ID subscription to use the Microsoft Entra Password Protection and an Entra ID Premium P1 or P2 subscription.
- The end user experience for Microsoft Entra Password Protection can leave a lot to be desired, especially when compared to a third-party solution like Specops Password Policy.
Two identity sources can create password compliance headaches
Many organizations today are using Microsoft 365 with Active Directory Domain Services, meaning there is the potential to have multiple identity sources and password policies. Businesses can choose to synchronize passwords between their Active Directory Domain Services and Entra ID. However, they must think about their identity architecture, how they will centralize password compliance, and if they will leverage services like Microsoft Entra Password Protection.
Those with an Entra ID subscription can use something called Password Writeback. Password Writeback is used when Entra ID has to check with on-premises policies via Entra ID. Note the following:
- It’s included with your Azure subscription
- It can synchronize changes to your Active Directory identities to Entra ID at a specified interval. There is a delay with this process
- You can sync custom attributes to third-party solutions
Specops Password Policy with Microsoft Entra Connect (formerly Azure AD Connect) password synchronization
In addition to Microsoft Entra Password Protection for on-premises, many organizations choose Specops Password Policy to provide robust modern password policies and breached password protection. With Password Writeback enabled, Microsoft Entra SSPR (formerly Azure AD SSPR) will check on premise password policies prior to confirming password reset or change from Entra ID.
If controlled by Specops Password Policy, the password must meet the specified requirements from Specops Password Policy. If the changed password meets the requirements, the password will be changed in Entra ID and be synced to your on-premises Active Directory Domain Services (AD DS) environment.
Note the following SSPR user password synchronization flow with Password Writeback:
As noted by Microsoft, you can use multiple password protection solutions with password filter DLLs. So, Specops Password Policy will work seamlessly with Microsoft Entra Password Protection to add another layer of password protection in your environment, including a Breached Password Protection feature. Additionally, with the Password Writeback feature enabled, on-premises password policies can be the centralized point of compliance, helping to eliminate password compliance headaches when juggling multiple identity sources. Learn more about Specops Password Policy and try it for free.
(Last updated on May 19, 2025)



