This website uses cookies to ensure you get the best experience on our website. Learn more
Active Directory privilege escalation
Table of Contents
There is no shortage of vulnerabilities and risks in today’s digital world. Attackers are using any way possible to compromise business-critical data. However, one of the prevalent ways cybercriminals can get a foothold into your environment is by compromising user accounts. The holy grail of user account compromise is access to a privileged user or group.
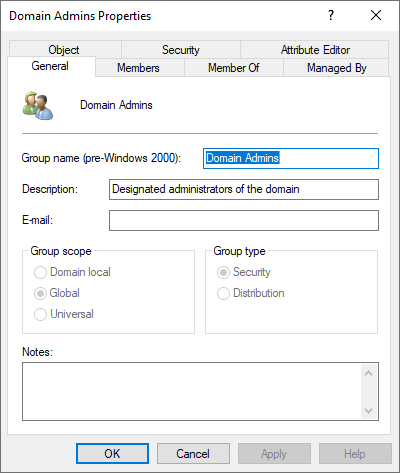
An Active Directory privileged account is an account with elevated rights or privileges to a system or other business-critical resource in the environment. In general, these may be accounts of very high-level administrator groups such as the coveted Domain Administrators, or Enterprise Administrators groups. An attacker with access to an account in one of these groups has the “keys to the kingdom.”
Active Directory privilege escalation attack
There are many ways that an attacker may start on their journey of a privilege escalation attack. They may attempt to access the internal network using a phishing email containing a malicious attachment or link. An unsuspecting end-user who installs the malicious app has given the attacker the means to harvest additional credentials. The attacker may be able to compromise a lower-level, non-privileged account using this method.
This first compromised account allows the attacker to perform reconnaissance and harvest other credentials in memory of the compromised workstation. If one of those accounts happens to be a privileged account, it is only a matter of time before the attacker can steal and impersonate the hashed password of the privileged user.
Once the attacker can get their hands on the hash of the privileged user, there is no end to the damage that may be caused. Despite having the ability to cause harm to data and network resources, an attacker will silently continue to investigate resources using the privileged account, and create more backdoors in case the initial account compromise is discovered.
Attackers can also use other means to begin a privilege escalation attack, such as password spraying, targetting different accounts with known passwords, or potentially breached passwords, that are in use in the environment.
Visibility on Active Directory password security issues
One of the challenges facing organizations with Active Directory is having visibility of the current state of user passwords. Using native Active Directory tools, there is no visibility to weak passwords, reused passwords, or even breached passwords.
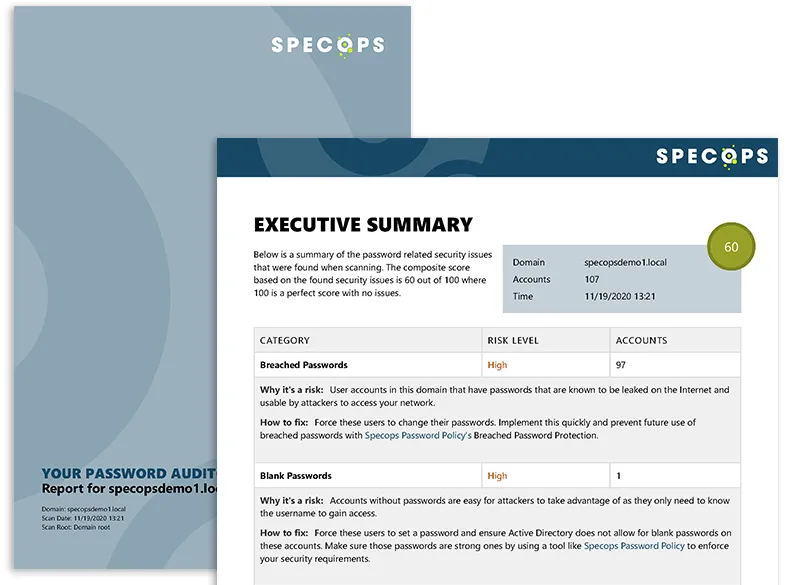
Specops Password Auditor is a freely available tool that allows businesses to quickly check the state of passwords in their Active Directory environment. Password Auditor performs the following checks in the environment:
- Blank passwords
- Breached passwords
- Identical passwords
- Admin accounts
- Stale Admin Accounts
- Password Not Required
- Password Never Expires
- Expiring Passwords
- Expired Passwords
- Password Policies
- Password Policy Usage
- Password Policy Compliance
When thinking about a privilege escalation attack, note the Breached Passwords and Stale Admin Accounts report. As mentioned earlier, hackers often use databases of breached passwords to compromise accounts in Active Directory environments. Also, a stale administrator account can be dangerous if left unattended in AD. In just a few minutes after a scan by Specops Password Auditor, administrators have complete visibility to significant password and account issues.
Wrapping up
Active Directory privilege escalation attacks are often made possible by weak, breached, or otherwise ineffective Active Directory passwords. Using the native tools provided in Active Directory, businesses struggle to have visibility to common password issues in their AD environments. Specops Password Auditor provides the tools needed for businesses to quickly scan user accounts for many different password and account vulnerabilities.
(Last updated on May 12, 2025)