This website uses cookies to ensure you get the best experience on our website. Learn more
What is the NIST guidance on password managers?
Table of Contents
Today’s end-users are juggling many sets of credentials for accessing critical business resources. To prevent users from writing-down, reusing, or selecting weak but memorable passwords, businesses are turning to password managers. A password manager is an encrypted database used for storing, retrieving, and generating passwords. Enterprise password managers not only improve password security, but also simplify password management for end-users.
Many organizations use the cybersecurity guidelines from the National Institute of Standards and Technology (NIST) to protect their information systems and comply with other regulations. This examines the older NIST 800 63b password standards, specifically, its guidance on password managers. In 2024, NIST published their newest password guidelines.
NIST guidance on password managers
NIST does not endorse or recommend a specific password manager solution. It simply recommends capabilities that fit the functionality of most password managers. The NIST Special Publication 800-63: Digital Identity Guidelines recommends paste functionality in password fields to facilitate the use of password managers. The Frequently Asked Questions for NIST’s Digital Identity Guidelines also specifies the following when using a password manager:
- Choose a long passphrase for the master password to the password manager and protect it from being stolen. A passphrase can be made sufficiently long to protect against attacks while still allowing memorization.
- Create unique passwords for all accounts or use the capability of most program managers to generate random, unique, complex passwords for each account.
- Avoid password managers that allow recovery of the master password. Any compromise of the master password through account recovery tools can compromise the entire password vault.
- Use multi-factor authentication for program manager applications that allow that capability.
- Use the password generator capability in most password managers to generate complex, random text answers to online “security” questions for those sites still using them.
Anything new for 2025?
There have been no new guidelines or updates specifically for password managers planned for 2025. However, NIST frequently updates its cybersecurity guidelines to reflect the latest threats and best practices. While there may not be specific updates for 2025 yet, it’s a good practice to ensure your password manager usage aligns with the latest NIST recommendations. Here are a couple of ways you can take to stay informed:
- Check NIST Publications: Regularly visit the NIST website to review the latest publications and drafts. NIST often releases drafts for public comment before finalizing new guidelines.
- Subscribe to NIST News: Sign up for NIST’s email newsletters or follow their official social media channels to get updates on new publications and changes.
Good password hygiene needed even with password managers
Organizations should not be under the misconception that once they deploy a password manager, the need for password security is no longer needed. On the contrary, password security could not be more critical.
For most businesses, AD credentials are the core authentication mechanism. To simplify enrollment for users, the Windows password can be used to log on to the password manager. The problem is that many password managers offer no protection on that master password, especially when it is the AD password. This emphasizes the importance of making sure Active Directory credentials are secure, password policies are enforced, and businesses are checking for breached credentials. How can organizations secure Active Directory credentials and bolster password hygiene?
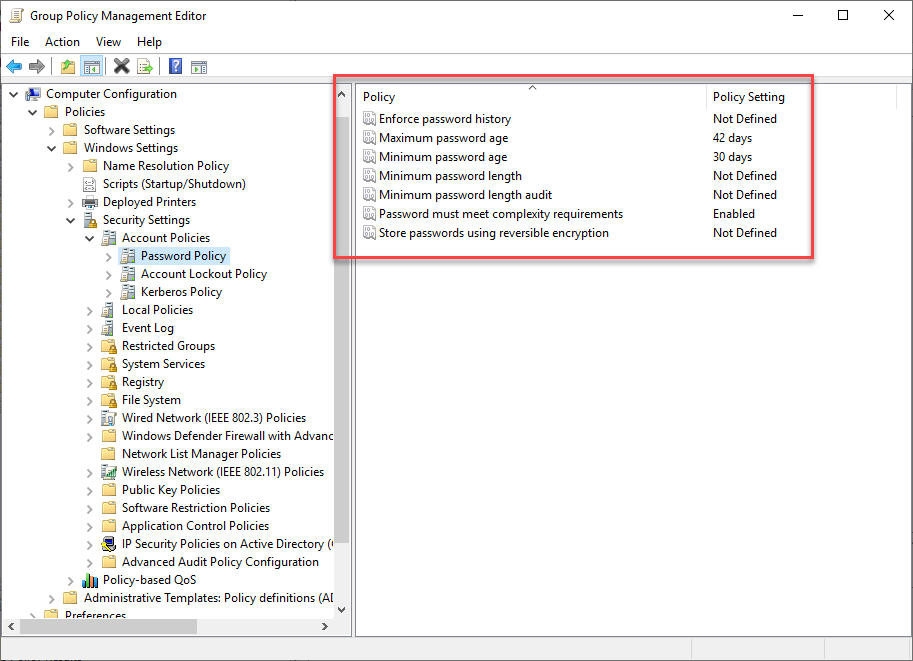
Active Directory password policies have been used by organizations to ensure compliance with company password policies, including length, complexity, and history requirements. However, these traditional password policies don’t meet today’s cybersecurity recommendations. As shown below, password policies on a Windows Server 2019 domain controller are still no different from a legacy Windows Server 2003 domain controller.
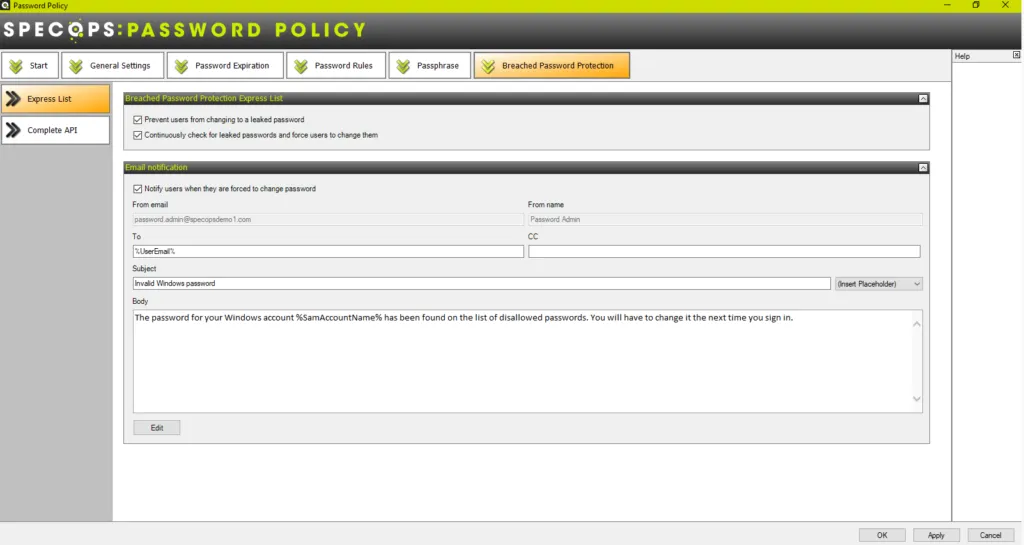
Specops Password Policy is a robust solution that allows businesses to implement modern password recommendations from NIST and other cybersecurity frameworks that include the traditional password policy characteristics, password dictionaries, breached password protection, and many other capabilities out of the box. It features the following:
- Find leaked passwords already in use in the environment
- Custom dictionary lists
- Passphrase support
- Block character substitutions (leetspeak)
- Intuitive client messages as to why chosen passwords fail
- Length-based password expiration
- Block user names, display names, specific words, consecutive characters, incremental passwords, and reusing a part of the current password
Learn more about Specops Password Policy and download a free, fully-featured trial version.
(Last updated on February 18, 2025)