This website uses cookies to ensure you get the best experience on our website. Learn more
How to enforce password complexity in O365?
Table of Contents
As organizations continue migrating data and services to the cloud, management and enforcement of strong password policies has never been more important. When it comes to Office 365 cloud-only users (not synchronized with a corresponding to an Active Directory account) the configurable options are quite limited – the more important it becomes to enforce the Office 365 default password policy on-premise.
Office 365 Password Policy
Office 365 cloud-only users are subject to the hard-coded password policy built into Azure AD. Per Microsoft, the complexity requirements of the Office 365 password policy are as follows:
| Property | Requirements |
|---|---|
| Characters allowed | • A – Z • a – z • 0 – 9 • @ # $ % ^ & * – _ ! + = [ ] { } | \ : ‘ , . ? / ` ~ ” ( ) ; |
| Characters not allowed | • Unicode characters • Spaces • Cannot contain a dot character “.” immediately preceding the “@” symbol” |
| Password restrictions | • A minimum of 8 characters and a maximum of 256 characters. *this is a recent change; the former maximum was 16 characters • Requires three out of four of the following: – Lowercase characters – Uppercase characters – Numbers (0-9) – Symbols |
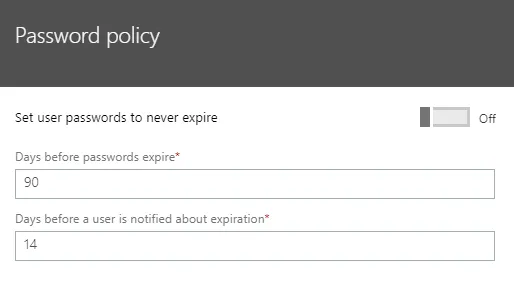
| Password expiry duration | Default value: 90 days. Global setting affecting all users in the organization. |
| Password expiry notification | Default value: 14 days (before password expires). Global setting affecting all users in the organization. |
| Password expiry | Azure AD Supports disabling password expiry on a per-user bases or for the entire organization. |
| Password change history | The last password can’t be used again when the user changes a password. |
| Password reset history | The last password can be used again when the user resets a forgotten password. |
Microsoft has recently launched Azure AD Password Protection, which adds dictionary capabilities to passwords for customers with an Azure AD Premium subscription. There are two layers to the Microsoft solution:
- Global Banned Password List – a Microsoft-provided list of “commonly used and compromised passwords.” Microsoft does not disclose any details about the contents of this list – there is, by design, no information on what sources Microsoft has used to compile the list, nor any details about its size.
- Custom banned Password List – available with an Azure AD Premium P1 or P2 subscription, customers can block a custom list of words from appearing in user passwords.
Microsoft also has support for extending the Password Protection feature to your on-premise Active Directory. Key limitations there include:
- As with all other Azure AD policies, it is a global setting (cannot target specific users/groups/OUs).
- Users do not get any feedback as to why their on-premise password was rejected during Ctrl+Alt+Del password changes on their laptops.
Increase your O365 password complexity
In order to get better control over your Active Directory and Office 365 passwords, administrators should look to 3rd party solutions. These solutions will need to leverage the on-premises Active Directory along with synchronizing or federating Office 365 password authentication, as Microsoft also does not support 3rd party password solutions for cloud-only Office 365 users.
With such solutions, you can achieve extremely granular control over both the scope and requirements of your password policies for both on-prem AD and Office 365 authentication.
Last updated on November 12, 2025