This website uses cookies to ensure you get the best experience on our website. Learn more
How and why the NHS should transform password policy for greater security
Table of Contents
As the largest employer in the United Kingdom, and the fifth largest in the world, the NHS has a responsibility to lead the way in cyber security. After all, there’s much at stake. For a high profile and public-facing organisation such as the NHS, strong security not only ensures compliance with today’s privacy and data protection regulations, but also drives public trust.
The NHS data security knowledge library, which includes their password recommendations, is currently under review. In the interim, the NHS points healthcare organizations to the NCSC for guidance. The update to the NHS password guidance should entail blocking weak and leaked passwords; it’s the only way to prevent the continued use of vulnerable passwords within the NHS.
Why is blocking compromised passwords so important?
As long as users continue to use common and predictable passwords, attacks will continue to work. However, hackers are not the only ones who can take advantage of password predictability. The best protection against this type of attack is using a password deny list of known breached passwords during the password creation process. This means checking a new password against the list, and preventing users from selecting passwords that are susceptible to attacks. For the NHS, implementing such a process would add a substantial layer of protection.
Limiting Password Risks
The death of passwords has long been predicted, but the fact that we use passwords to access all kinds of accounts including email, banks, portals, shopping, dating and social media applications, means passwords are here to stay. The average number of passwords a person deals with in their daily lives varies from 19 passwords (statistic from 2014) to 191 passwords (statistic from 2018). Think all of those passwords are unique? Think again. Password reuse is the result of people’s inability to come up with unique (and memorable) passwords for all of the services they access in their digital lives.
While the NHS remains a hot target for cyber criminals, many of the services used by their employees in their private lives have already been hacked, leaking billions of passwords onto the internet.
For example, over recent years we’ve seen data breaches across:
- 4 billion Yahoo user accounts
- 412 million Adult Friend Finder accounts
- 167 million LinkedIn passwords
- 10 million Dixons Carphone accounts
- 380,000 British Airways payment card details
With 1.7 million employees, the impact of a compromised service such as the above, can easily trickle down to the NHS. Hackers can break into other systems using the billions of leaked passwords from previous data breaches. As of January 2020, the NHS is blocking 100,000 weak passwords from being registered against NHSmail, however, it is not yet clear whether this will be rolled out to additional services.
How current NHS password policy works – and how it could be improved
Up until recently, the NHS had published the following password policy recommendations (Password Guidance for Health and Care Organisations):
- As a best practice guide, passwords should be created in the following format:
- A minimum of 8 characters long.
- Not contain a dictionary word of more than 4 characters.
- Contain at least two uppercase letters.
- Contain at least two lower case letters.
- Contain at least 2 numbers.
- Contain at least two special characters or non-alphanumeric characters, such as:
- ! ” £ $ % & * @.
The above guidance has since been removed as a result of the data security review. Organisation looking for the NHS password guidance should look to the NCSC, but additional, and sometimes conflicting, sources such as the NHSmail password policy, or that of any given Foundation Trust create confusion.
The new NHS password policy should limit password reuse by blocking compromised passwords. Today, hacking attempts are more sophisticated – hackers have moved beyond the outdated guidelines; which only serve to create passwords that are hard for people to remember, and easy for a computer to guess. The Password Strength comic from xkcd explains this well.
Ultimately this type of password policy results in passwords that meet all of the requirements, but are still weak – as a result of not being random. When people try to follow complexity requirements they rely on common character substitutions and fall into predictable patterns, such as adding a number to the end of their password.
With the potential of a single data breach to open the door to other systems, the NHS needs to stop users from using such vulnerable passwords. It is time to move away from policies that encourage users to create passwords that appear to be strong, but in fact are included in leaked lists.
Common examples of security risks that could have an impact for the NHS include;
Password Attacks: Password attacks are successful because they take advantage of the weakest link: the human. A common method of attack is to enter every word from a database of leaked passwords. The database is composed of common names and words, popular keyboard patterns and character substitutions (P@ssw0rd2018!), and lists of leaked passwords that are available online.
Credential stuffing: Another common password attack also takes advantage of the leaked passwords lists online. Credential stuffing is an automated hack where stolen usernames and password combinations are thrown at the login process of various websites in an effort to break in. With up to a 2% success rate, credential stuffers account for more than 90% of all login traffic on many of the world’s largest websites, and a spew of second-hand data breaches.
Blocking weak/breached passwords
A quick win for the NHS would be to block weak passwords altogether. By preventing predictable password behavior, this approach goes a long way to protecting the 1.7 million employees, and the sensitive data they hold. It can also help users cope with password overload as it takes the burden off the user, and places it on the authentication system. As always, changes are most effective alongside end-user training – users need to understand the why so they can make better choices.
Does your password policy align with best security practices? Our FREE password auditor tool takes just five minutes to detect breached passwords in your organization.
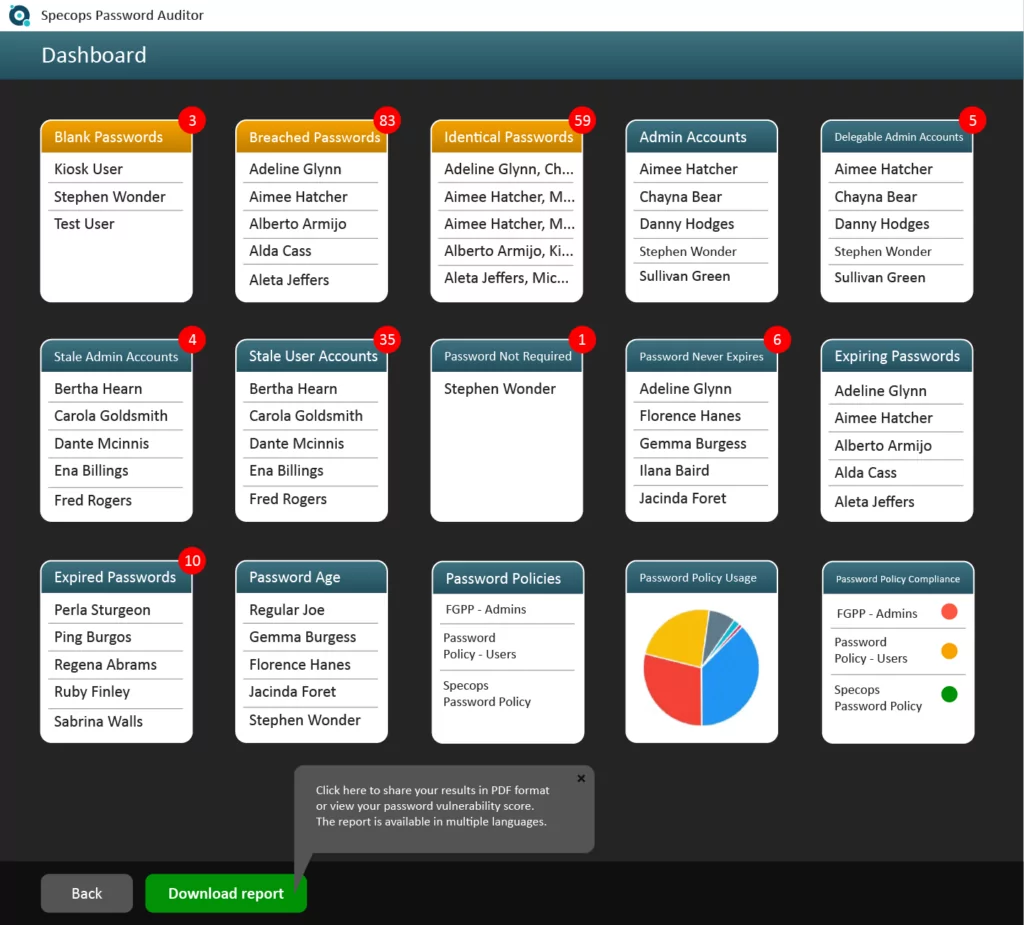
Download Specops Password Auditor for your FREE password security report, which includes:
- Overview of password policies and how resistant they are against brute-force attacks
- List of accounts using breached passwords
- List of dormant user accounts
- + more!
Contact our password security specialists in the UK:
Call us: +44 (0)203 002 1877
(Last updated on April 24, 2025)
