This website uses cookies to ensure you get the best experience on our website. Learn more
Introducing Live Attack Data to Specops Breached Password Protection (plus what passwords you should block right now)
Table of Contents
Today, Specops Software released the latest update to its Breached Password Protection list. This release includes, most notably, the addition of passwords observed in real attacks.
Prior to this release, Specops Breached Password Protection sources included lists of known compromised passwords and common dictionaries used in attacks. Today, those lists are expanded on as Specops adds live password attack data to its Breached Password Protection service.
“This expansion of what Breached Password Protection does is a big win for our customers,” said Darren James, Product Specialist at Specops Software. “Not only are they covered on the ‘must block breach corpuses’ regulatory side but now our customers’ networks are also protected against passwords used in attacks happening right now.”
This new live attack data comes from the team’s recently deployed global honeypot system which collects passwords used in attacks on the system’s endpoints. This data is especially useful for IT admins who are looking to protect against attacks on Windows networks because the honeypots are made to look like real Windows networks.
What do we know about these attacks in the wild? Let’s take a look.
Fulfilling Regulatory Requirements Not Enough
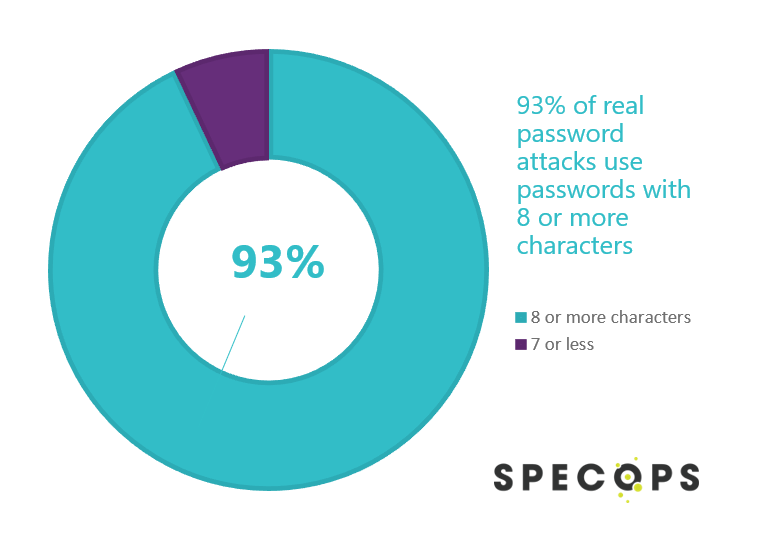
Minimum password length is a good start at defending against brute force attacks; however, you’ll have to go beyond regulatory requirements to protect against real attacks. For example, NIST requires a minimum of 8 characters or more and it seems attackers are aware of this as 93% of the passwords used in these brute force attacks include 8 or more characters.
What about requiring special characters or complexity? Standards like PCI or HITRUST require different character types as part of your organization’s password rules. Attackers seem to be taking these standards into account as well as our research team found that 68% of passwords used in real attacks include at least two character types.
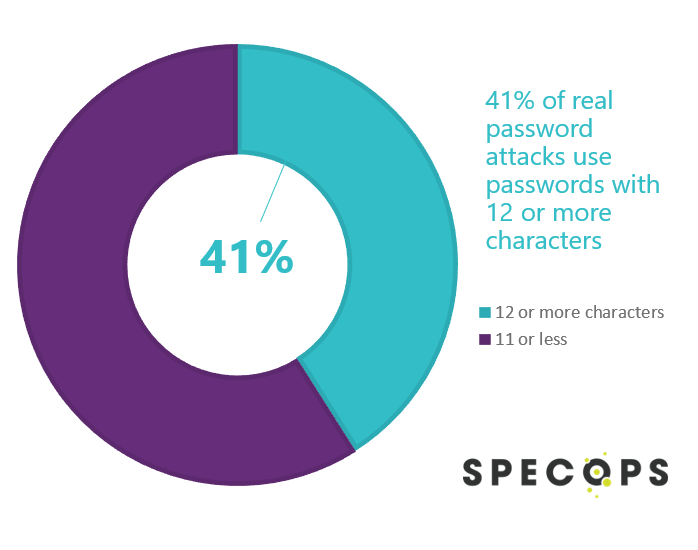
Top Passwords 12 Characters or More
We hear from customers that 12 characters is a common password length requirement so we asked our research team to pull some analysis for that length. Our team not only found that 41% of passwords used in real attacks are 12 characters or more but also pulled a list of the actual passwords.
Here are the top 10 passwords used in real brute force attacks that are 12 characters are more:
- ^_^$$wanniMaBI:: 1433 vl
- almalinux8svm
- dbname=template0
- shabixuege!@#
- P@$$W0rd0123
- P@ssw0rd5tgb
- adminbigdata
- Pa$$w0rdp!@#
- adm1nistrator1
- administrator!@#$
“This data shows us that attackers know even us administrators can fall into predictable weak patterns when setting passwords,” noted James. “The good news is that if organizations have Breached Password Protection setup, there’s nothing more they need to do to gain access to this expansion of protection.”
Curious if you have any of these passwords in use in your organization’s Active Directory? You can find out how many of your Active Directory users are using compromised passwords like these by running a free read-only scan with Specops Password Auditor. Read more and download our Free Password Auditor.
With Specops Password Policy and Breached Password Protection, companies can block over 4 billion compromised passwords in Active Directory. These compromised passwords include ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as NIST or NCSC. Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real world password attacks happening right now. The Breached Password Protection service blocks these banned passwords in Active Directory with customizable end-user messaging that helps reduce calls to the service desk.
About Specops Software
Specops Software is the leading provider of password management and authentication solutions. Specops protects your business data by blocking weak passwords and securing user authentication. With a complete portfolio of solutions natively integrated with Active Directory, Specops ensures sensitive data is stored on-premises and in your control. Every day thousands of organizations use Specops Software to protect business data.
Media Contact
outpost24@eskenzipr.com
(Last updated on April 8, 2025)