This website uses cookies to ensure you get the best experience on our website. Learn more
Find AD accounts using Password-Not-Required (blank password)
Table of Contents
The landscape of passwords across an Active Directory environment can certainly be varied. Even with password policies in place there is still the potential for risky passwords assigned to user accounts in the environment. One such dangerous type of “password” is a blank password.
An Active Directory user account configured with password-not-required or blank password is extremely easy for an attacker to compromise. These types of accounts may exist in Active Directory either mistakenly or with the idea that a proper password would be assigned later. It can be extremely difficult for administrators to have a good handle on passwords across the environment, especially with built-in tooling found in Active Directory.
Blank passwords are numbered among very dangerous types of passwords that your organization needs to have visibility to and protect against. How can blank passwords be assigned even with a password policy in place? What tools can be used to find these types of accounts and other password risks in the environment?
Why and how are blank passwords assigned?
You may wonder why blank passwords would be set on user accounts. There are a number of potential reasons this can happen. If an admin is troubleshooting an issue for a particular user account, it can be cumbersome to continually type a user account password during a troubleshooting session. Therefore, a blank password may be temporarily set. The intention may be to come back and properly set a password later. However, this may not get done.
An admin who may either be unscrupulous or simply not use very good judgement may use this practice when setting up test accounts or temporary accounts for one reason or another. Additionally, an attacker who may have compromised an admin account may set blank passwords on user accounts for easy access.
You may also wonder, how can a blank password be set on an account if you have a password policy in place which dictates a minimum number of password characters? Under normal circumstances and configurations for a user account that is under the purview of a password policy, attempting to set a blank password will result in an error similar to below.
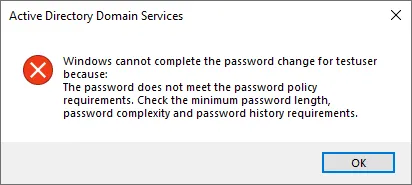
In this case, the password policy is doing its job and preventing a blank password from being set on the user account. Note that even a domain administrator receives this message when attempting to set a blank password on a user account in Active Directory Users and Computers.
How its possible to set a blank password
Even with a password policy in place that affects a user account, it is possible to set a blank password for that user. How can this be done? There is a special attribute that can be set for a user account called the Password-not-required attribute. Think of this like a special flag or setting on the user account itself that basically allows the requirements of any password policies to be bypassed and a blank password can then be configured on the user account.
How can this attribute be set on a user account? There are a couple of different ways.
- PowerShell
- Active Directory Users and Computers (ADUC)
You can use the following PowerShell cmdlet to set the Password-not-required attribute:
Get-ADUser -Identity testuser | Set-ADUser -PasswordNotRequired $true
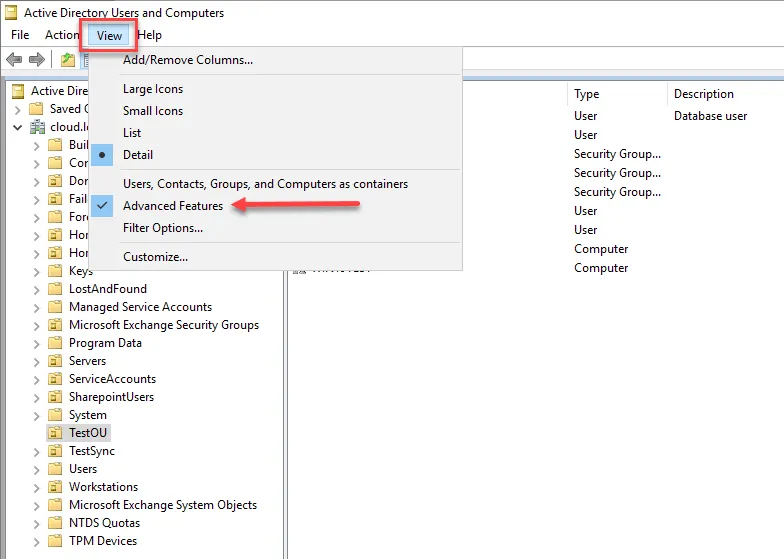
In Active Directory Users and Computers, it is not as obvious. With ADUC, you have to have ADUC configured to display advanced features which allows low-level attribute editing.
Once you have the advanced features display turned on, you will see the Attribute Editor tab. Here you can edit low-level Active Directory attributes on objects. There isn’t a standalone attribute called Password-not-required. Rather, this setting is contained in the userAccountControl attribute as a value held here as you can see below. It is defined as PASSWD_NOTREQD.
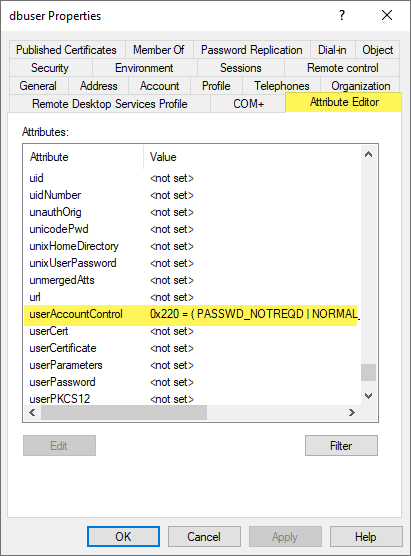
The PASSWD_NOTREQD value equates to an integer value of 544. When you use either PowerShell to set the attribute or configure with the integer value, the setting is configured either way. In fact, when you set it using PowerShell, the same integer value is configured in the userAccountControl attribute.
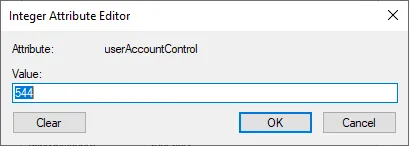
Once the PASSWD-NOTREQD is configured, you can now set a blank password on the user account.
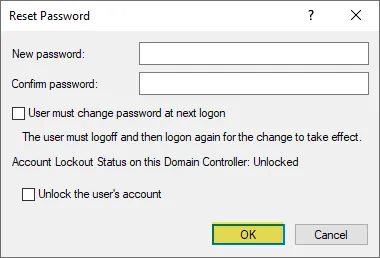
Whereas attempting to set a blank password failed before, now with the attribute set, we can set a blank password for the user account. Keep in mind, no changes were made to the password policy.
The above walkthrough of steps and configuration shows that even when users are subject to a password policy via Active Directory, there is still the possibility of having blank passwords in the environment. This underscores the importance of keeping a close eye on this possibility.
Finding Active Directory user accounts with Password-Not-Required configured
It is important to keep an eye on all users accounts in the environment and make sure that periodic checks are made to ensure there are no user accounts with this attribute and blank passwords configured. Let’s see how we can find these types of user accounts in Active Directory using PowerShell.
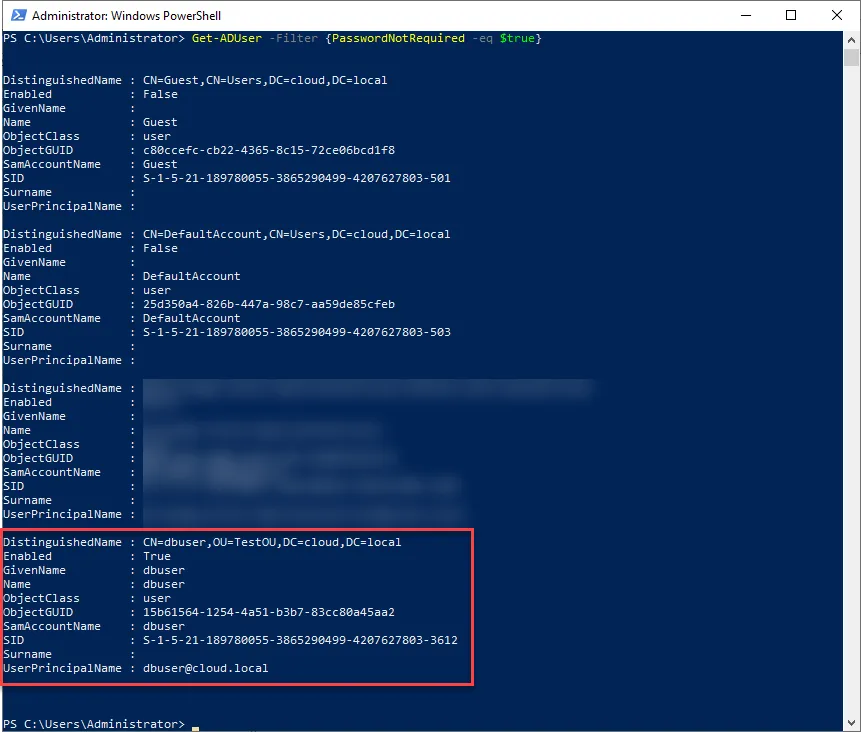
Since this is an attribute that is configured, we can use PowerShell to search Active Directory and find user accounts that potentially have the attribute configured. To do that, use the following cmdlet:
Get-ADUser -Filter {PasswordNotRequired -eq $true}

Other risky password types and attacks
While blank passwords are extremely dangerous and you certainly want to get a handle on those in the environment, there are many other types of risky passwords that can leave your organization open to cyberattack. What are these? These include weak, re-used, and breached passwords.
While certain weak variations of passwords can be handled with good password policies in Active Directory, as shown with the blank passwords, password policies are not the “end all be all” of password security in your environment. A case in point is passwords that may have been exposed in previous data breaches. Breached passwords are passwords that have been exposed by previous cyberattacks or data leak events where user accounts and passwords are part of data that has been obtained by an attacker.
Attackers use entire databases of leaked or breached passwords in attacks called “password spraying”. With password spraying attacks, an attacker tries only a few passwords against a multitude of accounts. In this way, the attack is less visible and more likely to succeed against common deterrents such as account lockout policies. Due to the fact that the attacker is only trying a small number of passwords, the lockout policy may not even be triggered. Additionally, the failed logon attempts may be just a small blip on the radar and go undetected.
Automated Password Scans and Breached Password Detection
Performing manual checks on your Active Directory environment is a good place to start looking to see if there are dangerous settings enabled such as the Password-not-required flag. However, for long term and consistent password security and risk mitigation having an automated solution for scanning your Active Directory environment and looking for risks such as blank passwords, re-used passwords, and breached passwords is a much more powerful way to mitigate potential cybersecurity risks that come from passwords in your environment.
Specops Password Auditor (free tool) provides a great way to provide automated scans of your environment for many different types of password risks including an updated database of breached passwords. Notice the following types of risk it highlights in your Active Directory environment as well as additional insights:
- Blank passwords
- Breached passwords
- Identical passwords
- Admin Accounts
- Stale Admin Accounts
- Password Not Required
- Expiring Passwords
- Expired Passwords
- Password Policies
- Password policy usage
- Password policy compliance
Specops Password Auditor sheds light on the Password-not-required attribute and blank passwords as described earlier along with many other risks in the environment. Additionally, you can export the findings to PDF for proper documentation or hand offs to business stakeholders and for compliance/audit documentation which is a great feature.
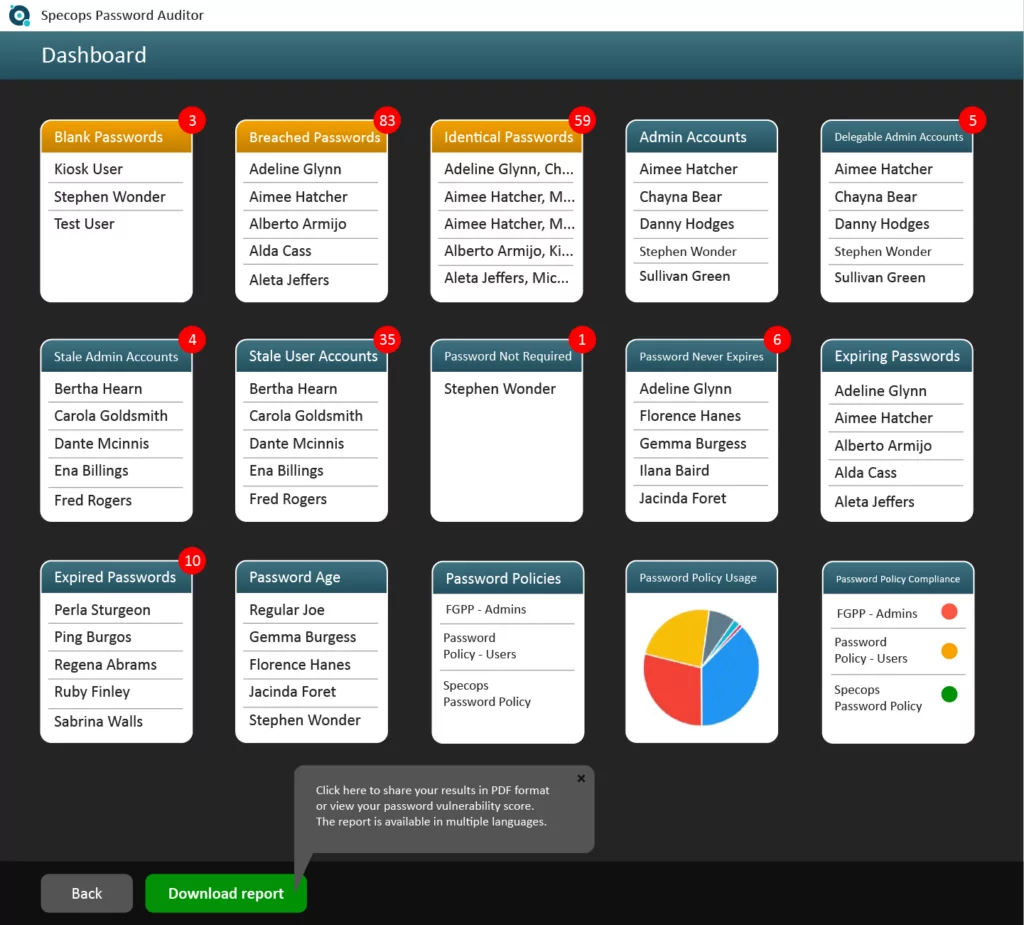
You can also drill down further in each of the result categories to see additional information such as where the user account is located, last logon timestamp, as well as which password policy it is subject to. You can also export the user(s) as a CSV file from each of the screens for further input into automation tools or other scripts.
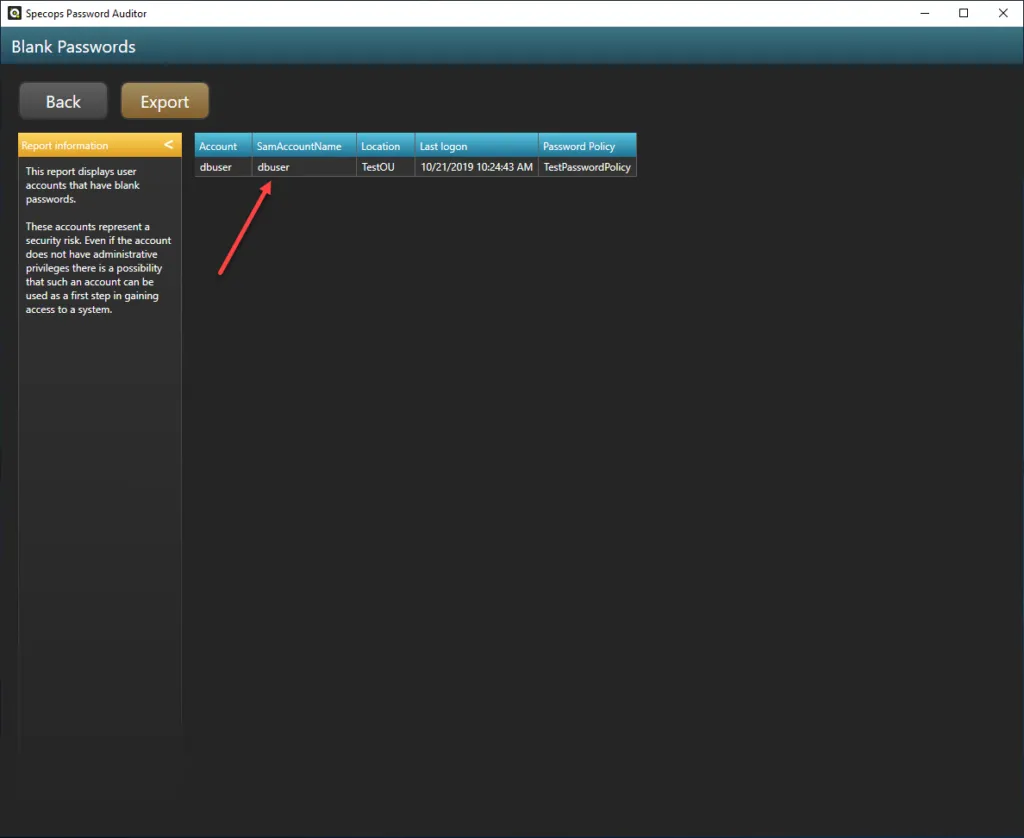
Find blank passwords in your Active Directory
Blank passwords in your environment are especially dangerous as these can easily allow an attacker to gain access to resources in the environment with ease. Even when you have a password policy defined in Active Directory that prevents blank passwords, the Password-not-required attribute overrides password policy configuration and allows a blank password to be set on a user account.
Having visibility to this configuration as well as other dangerous password settings in the environment is especially important to prevent password spraying attacks and other types of password attacks. Using PowerShell, you can search Active Directory for the Password-not-required attribute and see which accounts on which this may be configured.
A much better approach is using a solution that provides an automated way to gain visibility to not only blank passwords, but also many other dangerous passwords such as re-used passwords and breached passwords. Specops Password Auditor is a free, read-only tool that provides a simple way to see these types of risks in the environment and mitigate them before they can be exploited by an attacker.
(Last updated on April 30, 2025)


