This website uses cookies to ensure you get the best experience on our website. Learn more

FFIEC password requirements
Table of Contents
Cyberattacks often target the financial industry due to the nature of the information they possess. One of the organizations that provide cybersecurity guidance and standards for financial institutions is the Federal Financial Institutions Examination Council (FFIEC). While the FFIEC does not offer specific password characteristics as part of its recommendations, we can use the guidelines to establish basic principle for FFIEC password requirements.
In its Joint Statement – Cyber Attacks Compromising Credentials report, the FFIEC details the importance of guarding against stolen credentials and the risks involved. The report recommends the following controls for critical systems:
- Encrypt sensitive data on internal and external-facing systems in transit and, where appropriate, at rest.
- Implement an adequate password policy.
- Review the business processes around password recovery.
- Regularly test security controls, such as web application firewalls.
- Implement procedures for the destruction and disposal of media containing sensitive information based on risk relative to the sensitivity of the information and the type of media used to store the information.
- Filter Internet access through Web site whitelisting. Where appropriate to limit employees access to only those Web sites necessary to perform their job functions.
- Conduct incremental and full backups of important files and store the backed-up data offline.
With the report findings highlighting the danger of compromised accounts, and the emphasis on implementing an adequate password policy and password recovery process, there are areas of password security that come into clear focus.
Meeting FFIEC password requirements
To summarize three critical areas of focus related to the FFIEC guidance, we can state the following:
- Protect against compromised credentials
- Implement a strong password policy
- Have secure mechanisms in place to recover or reset passwords
Protect against compromised credentials
In addition to written recommendations from the FFIEC, guidance related to password security and protection has been steadily changing over the past few years. Industry experts and cybersecurity organizations have published updated direction, noting that traditional password policies are no longer sufficient to secure passwords.
Both Microsoft and NIST recommend implementing dictionary-based password lists, as well as breached password protection.
Implement a strong password policy
The overall implementation of a strong password policy is still needed, and very much recommended. Businesses need to note industry cybersecurity framework recommendations regarding secure and robust password policies in their environment, including the NIST password standards.
Remember, the recommendation for strong password policies should include dictionary-based protection and breached password protection.
Secure password recovery and reset process
When an end-user calls the helpdesk and asks to have their password reset, how can helpdesk technicians securely verify they are who they say they are? It can be an eye-opening area of risk that many companies have not considered. There must be processes and technical solutions to securely verify identity using a multi-factor approach to guarantee the credentials are not falling into the wrong hands.
Meeting the FFIEC password requirements with Specops
Specops Software helps businesses secure password policies in their environment with custom dictionaries, breached password protection, and secure password reset solutions.
Specops Password Policy
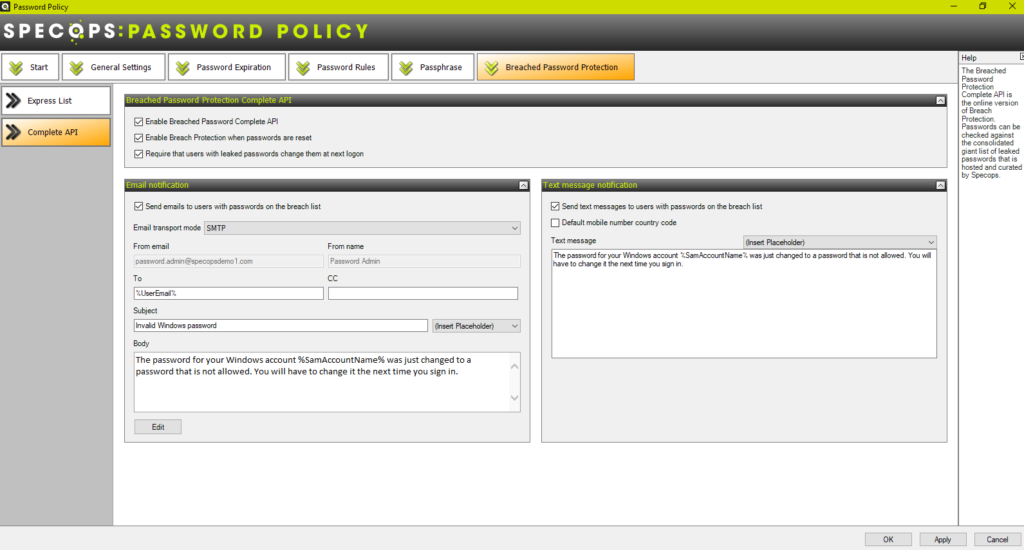
Specops Password Policy allows businesses to implement dictionary-based password policies and breached password protection, capabilities not easily implemented with native Active Directory functionality. Using Specops Password Policy, you can enforce breached password protection in your Active Directory environment that requires users with leaked passwords to change their password at the next logon.
Specops uReset
Using Specops uReset, organizations can easily implement self-service password resets (SSPR) in their Active Directory environment. The solution minimize helpdesk calls by verifying end-users with multi-factor authentication, before allowing them to securely reset their password.
Below is an example of a prompt the end-user will see when resetting their password. The user is required to verify their identity by multiple authenticators. Users can only reset their password when they have satisfied the number of required authentication factors.
Final thoughts
Cyberattacks are steadily on the rise across all business sectors and industries. However, financial services have always been a prime target of attackers. The FFIEC guidance related to password policies recommends strong password policies, protecting against compromised accounts, and secure password recovery and reset procedures. Specops Software allows companies to have a robust framework of password security protections in place to protect against account compromise.
(Last updated on May 9, 2025)