This website uses cookies to ensure you get the best experience on our website. Learn more
Introducing: Continuous Compromised Password Scanning for Specops Password Policy
Table of Contents
Continuously protect against the persistent threat of password reuse with this daily check against our daily updated compromised password database
Today we’re introducing a new feature for Specops Password Policy, continuous scans for the Specops Breached Password Protection service. This feature finds breached passwords daily, instead of only at password change or reset.
The Breached Password Protection database is updated with passwords collected by our honeypot network system and newly discovered password leaks. Together with the daily updates to the Breached Password Protection database Specops Password Policy now offers one of the most complete compromised password monitoring solutions on the market.
The Persistent Password Threat is More Than Just Attackers
Passwords remain one of the most vulnerable pieces of an organization’s network. Microsoft found in 2022, 1,287 password attacks occur every second (more than 111 million per day). Reusing a known breached password in an attack (a “password breach replay” attack as Microsoft refers to it) grew to 5.8 billion per month in 2022.

The persistent threat of password attacks is a huge risk to organizations. However, the element that is driving that risk is an organization’s users themselves. Persistent password reuse by users in their work and personal lives is the reason that attackers continue to succeed using known compromised passwords to gain initial foothold within a network.
We know this because it repeatedly shows up in attack analysis and behavior data:
- 86% of attack initial access was gained through stolen credentials (Verizon, 2023)
- 44 million Microsoft users were found to be reusing password in analysis over a 3-month period (Microsoft, 2019)
- More than 60% of knowledge workers reuse the same password or a variation (LastPass, 2022)
This behavior from end users is not to blame though – the explosion of web services and Software as a Service has pushed the individual password management problem out of control.

The number of work identities an individual manages is only part of the burden that leads to passwords reuse. The personal identity management burden has also increased. In 2023, Bitwarden found 68% of internet users report managing passwords for 10 websites or more with 84% admitting to password reuse. For 34% that burden is more than 25 sites or apps. (source)
With so many identities and logins to manage, end users are always going to fall into poor password behavior like password reuse.
What this Means for Your Network
The increased identity burden on end users in their work and personal lives means increased risk for your network.
While many industry surveys (like the above referenced Bitwarden survey) include the average number of passwords an individual has to manage as 20-30, LastPass found that number to be much higher when you don’t rely on self-reports.
In 2021, LastPass found the average number of passwords an employee has to keep track of is 191. That’s a 7x increase over self-reported numbers that LastPass attributes to people not realizing just how many accounts they have to manage.
If we look at just the work identity burden, we can quickly see what this means for an organization’s password reuse risk.
A self-reported average of 10 logins per employee means a potential 5,000 password compromise opportunities for a 500-user organization. For a 1,000-user organization, that’s 500,000 potential points of compromise.
LastPass found in reality, the estimated total passwords in an average 250-employee company to be more than 47,000 passwords.
This increased risk from user behavior paired with the increased attacks on passwords from bad actors means organizations need increased protection.
For organizations using “never expire” the password reuse risk is even higher.
For organizations who have embraced a “never expire” approach for Active Directory passwords, this risk is even more increased. Most compromised password checks on the market, including Azure AD (Entra ID) Password Protection, rely on the password change or reset event. Without that event, the risk posed by user password reuse is unchecked.
How do organizations solve for the password reuse problem?
The risk of password reuse for your organization is clear. But how do organizations solve for it? There are quite a few options but most employed today have gaps.
Train Users on Better Password Behavior
Cybersecurity training to correct user behavior is one option organizations employ to try and fix poor password behavior. If the users are the problem, fix the users, right?
Unfortunately, this rarely solves the issue as illustrated by what LastPass found in their 2022 research:
With 65% of those surveyed claiming to have some type of cybersecurity education, the majority (79%) found their education to be effective, whether formal or informal. But of those who received cybersecurity education, only 31% stopped reusing passwords. (LastPass, 2022)
Get Rid of Passwords
The risk of password use is clear which makes the idea of removing them entirely enticing. However, removing passwords completely is not a realistic option for most organizations
Bitwarden found the top reason organizations have not gone passwordless is that the applications in use are not designed to go passwordless (almost half of IT decision makers surveyed reported this reason)
Just Add MFA
While removing passwords completely is not possible for most organizations today, adding MFA to more use cases is. However, second factors are not invulnerable.
One such method for compromising a second factor, MFA prompt bombing (also known as MFA fatigue attack), made headlines when Uber fell victim to this attack in 2022.
Microsoft found MFA fatigue attacks occurred over 31,000 times per month on average in a recent 15-month study. They also found YoY attacks increasing for this attack method with August 2022 seeing a 26% increase over August 2021.
Most MFA fatigue attacks require the bad actor to first have access to the first authentication factor, the password. Defending the password from compromise eliminates the opportunity for MFA prompt bombing.
No single authentication factor is immune to attack. Adding MFA does not remove the need to protect the password and protecting the password does not remove the need to add MFA. Protecting both the password and any secondary factors in a layered approach is the more pragmatic and secure approach.
Just check for compromise at change or reset
Most solutions on the market, including Azure AD (Entra ID) Password Protection, only check for the use of compromised passwords at a change or reset event.
With IT departments wanting to increase password age limits and decrease the frequency of forced password resets (or getting rid of expiry altogether), this infrequent check for the use of compromised passwords leaves an increasing gap.
IBM reports that it takes organizations on average 204 days to discover a breach in 2023 (source) and 73 days to contain it.
With that gap in detection, checking passwords at just change or reset every few months is not enough.
What do to instead
The answer for what to do about the continuous threat of password reuse is to continuously check Active Directory passwords against a frequently updated compromised password database.
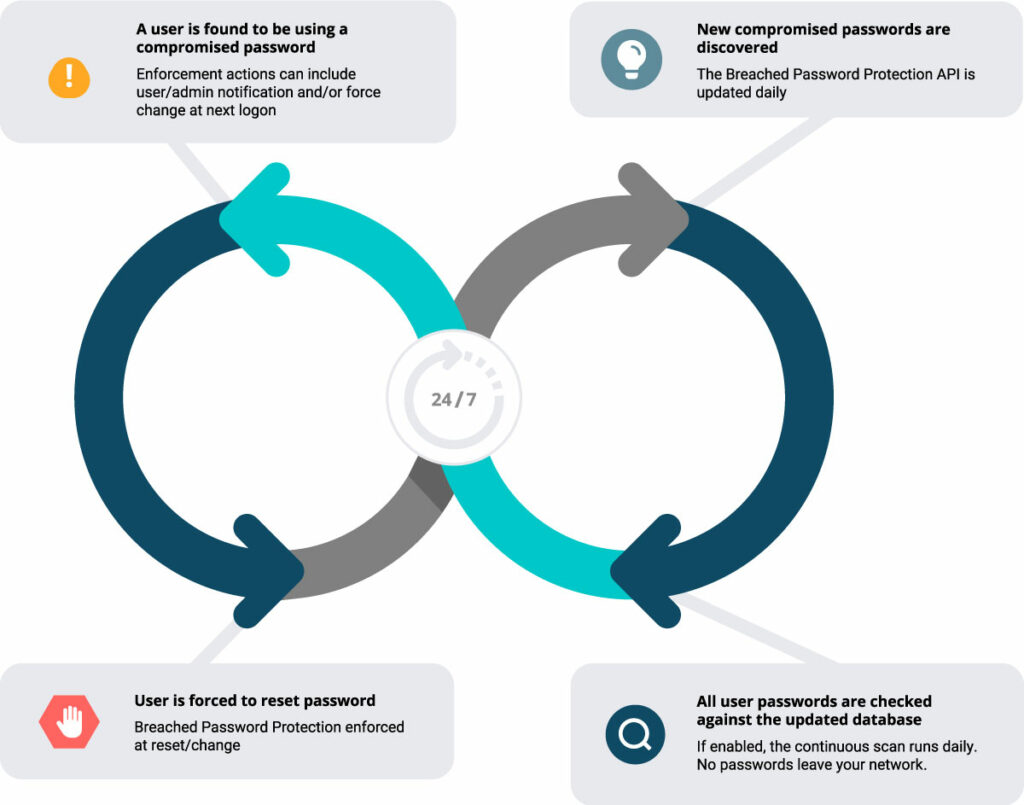
How Continuous Scanning with Specops Breached Password Protection Works
The continuous scan feature checks all Active Directory passwords against the Breached Password Protection API for compromise once a day. The API is updated daily with newly discovered compromised passwords from our password honeypot system in addition to newly discovered password leaks when they occur.

Administrators can review results of the latest continuous scan in the Domain Administration Tools.

Daily scans paired with smarter and more comprehensive compromised password data
Specops Password Policy with Breached Password Protection can now offer even more protection for your organization against the constant threat of attack.
The Breached Password Protection service:
- Protects against the use of more than 4 billion unique known compromised passwords
- Includes password data from both known leaks, our own honeypot system that collects passwords being used in real password spray attacks, and stolen credentials obtained by malware (powered by the threat intelligence unit at Specops Software’s parent company, Outpost24).
- Updated daily with newly discovered passwords
The daily update of the Breached Password Protection API, paired with continuous scans for the use of those passwords in your network, equals a much more comprehensive defense against the threat of password attack and the risk of password reuse.
Try it today
Interested in seeing how this might work for your organization? Have questions on how you could adapt this for your needs? Contact us.
(Last updated on February 19, 2025)