This website uses cookies to ensure you get the best experience on our website. Learn more
What is the California default password law?
Table of Contents
Passwords have become a subject of scrutiny, not only in IT security operations, but even extending out into new legislative mandates that have brought passwords into clear focus. California’s Senate Bill 327 (SB-327) was enacted in 2018 and became effective on January 1, 2020. It gives specific direction in regards to passwords used on “connected devices.” What is SB-327? What specific guidance does is give in regards to passwords? How can organizations audit their network for default, weak, and even breached passwords in their environments, applying the principles of SB-327?
What is Senate Bill 327 (SB-327)?
With data privacy and other cybersecurity concerns on the forefront as more devices have Internet connectivity capabilities, new measures are being taken to help secure devices connected to the Internet. A huge problem with Internet of Things (IoT) devices has been the default configured passwords. Many home users and those who are not technically proficient do not understand the dangers of placing an IoT device on the Internet with a known, default password.
Manufacturers of IoT devices have for years used the same default passwords on specific IoT devices. These passwords are easily found by simply “Googling” the password for the device or downloading the product documentation. As an example, below are quick results for default camera password.
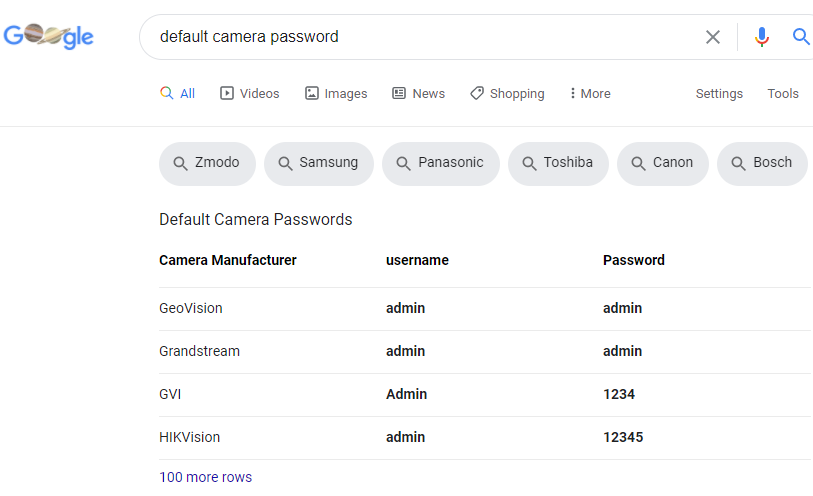
It doesn’t take much imagination to realize what can happen when these types of devices are connected to the Internet with the default password. IoT devices can become easy targets of an attacker looking to use them for malicious purposes.
The new Senate Bill 327 (SB-327) was enacted to help rectify this issue in California, USA. What is SB-327? SB-327 is a privacy law that protects devices that are sold or offered for sale in California. The security of connected devices section of the law contains the following directives:
- Appropriate to the nature and function of the device.
- Appropriate to the information it may collect, contain, or transmit.
- Designed to protect the device and any information contained therein from unauthorized access, destruction, use, modification, or disclosure.
- Subject to all of the requirements of subdivision (a), if a connected device is equipped with a means for authentication outside a local area network, it shall be deemed a reasonable security feature under subdivision (a) if either of the following requirements are met:
Two phrases in the above are worth clarifying. What is a connected device? According to the legislative documentation, a connected device is any device or physical object capable of connecting to the Internet, directly or indirectly, and is assigned an IP or Bluetooth address. As you can imagine, a connected device could contain any number of devices available today, such as smartphones, smartwatches, wearable devices, televisions, kitchen appliances, doorbells, thermostats, and many others.
Also, what is reasonable security? The law states explicitly that reasonable security is met if either of the following are true:
- The preprogrammed password is unique to each device manufactured.
- The device contains a security feature that requires a user to generate a new means of authentication before access is granted to the device for the first time.
So, in other words, the device must come preprogrammed with a unique password, or once the device turns on for the first time, the device will prompt to change the password. It could also be a combination of both. In this way, passwords are kept unique for IoT devices sold in the state of California.
The new SB-327 highlights an important consideration for all connected devices, not just IoT. Passwords are arguably the weakest link in the cybersecurity of most organizations. Even with password policies on various IT systems, end-users can still use passwords easily guessed or vulnerable to brute force and password stuffing attacks. Users may even attempt to pick a unique password. However, the password may be one that has been exposed in a cybersecurity breach.
How can the principle found in SB-327 apply to not only device passwords but also user passwords?
Securing Active Directory from weak and breached passwords
Microsoft Active Directory is the de facto standard for enterprise authentication used by most organizations. It provides the identity “source of truth” used to apply permissions and login to many enterprise systems. Even with password policies that dictate the use of certain characters and password lengths, users tend to create easy to remember passwords. It leads to common character transformations used by end-users and other easily guessed substitutions. Attackers know this, and with a few readily available tools, they can use brute force or password spraying to compromise passwords.
Also, attackers often use large databases of breached passwords found on the “dark web” exposed in previous breaches in other environments. Humans tend to think alike. If a user in one organization thinks of a specific character substitution for a password, someone else may likely think of the same one. These large breached password databases are often very successful in compromising user account passwords in totally different environments.
We could even draw the parallel of a default password of sorts when users choose weak or breached passwords. Finding these types of passwords in the environment is extremely important before an attacker does. How can this be accomplished effectively?
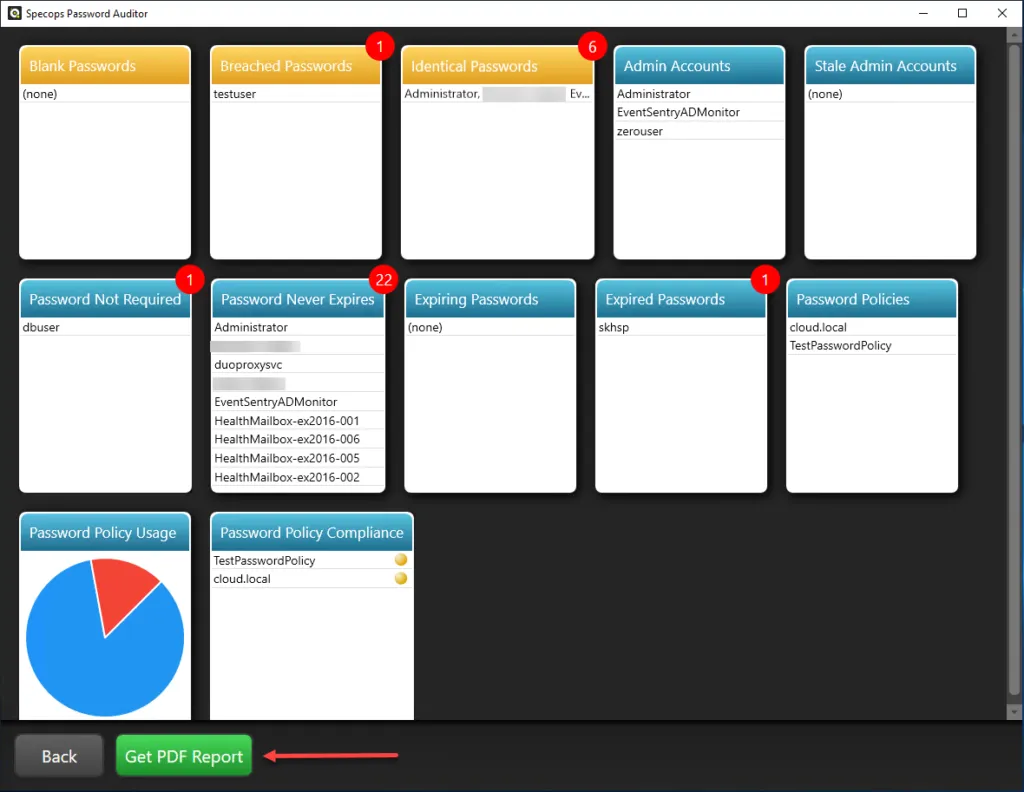
Specops Password Auditor is a freely available robust tool that quickly finds risky passwords in your Active Directory environment. You can easily see which accounts have weak passwords, identical passwords, and even breached passwords. It provides visibility to the following:
- Blank passwords
- Breached Passwords
- Identical Passwords
- Admin Accounts
- Stale Admin Accounts
- Password Not Required
- Password Never Expires
- Expiring Passwords
- Expired Passwords
- Password Policies
- Password Policy Usage
- Password Policy Compliance
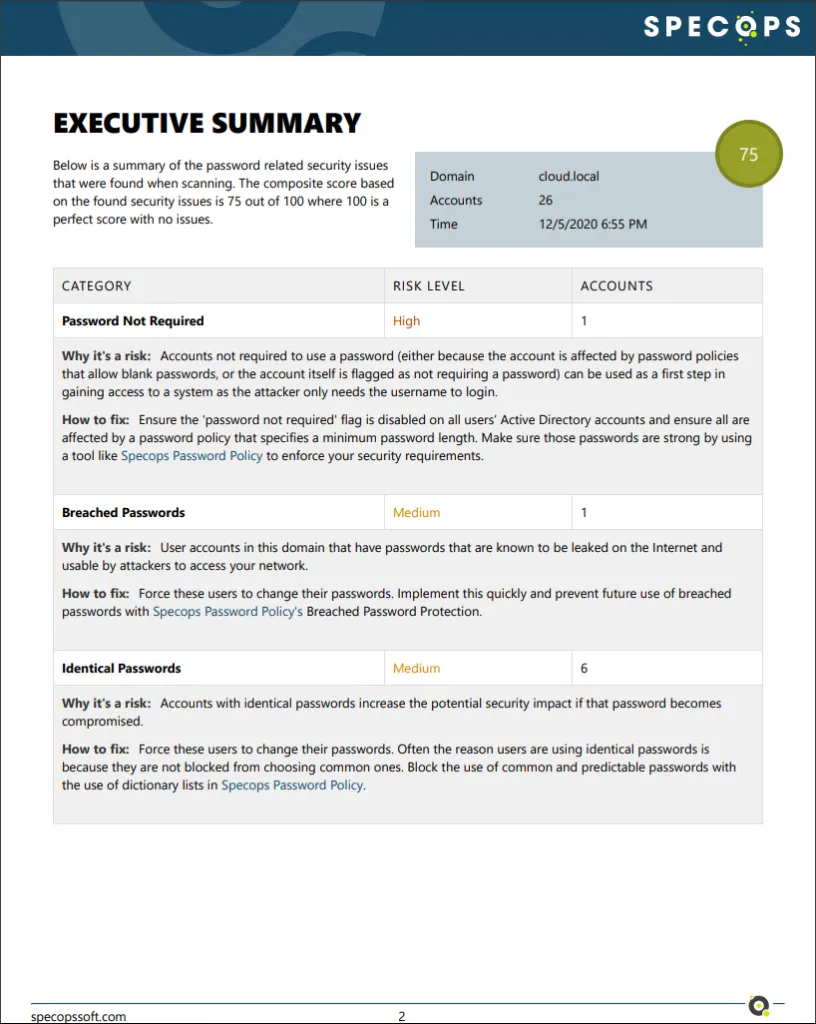
Specops Password Auditor allows IT teams to have the visibility needed to risky password usage in the environment and even auditing password policy compliance. With the password compliance audit, existing password policies are compared to leading cybersecurity standards such as NIST and others. You can also generate executive reports as needed for auditors or other business stakeholders to detail password policy compliance in the environment.
Wrapping Up
The new California SB-327 regulation dictates that all IoT devices that are sold or offered in the state of California must adhere to specific regulations in regards to passwords configured on the device. All passwords are required to either be unique or prompt for a password change before the user has access to it. In this way, default passwords are no longer the culprit when IoT devices are connected to the Internet and compromised.
For businesses, preventing risky passwords across all IT resources, including user accounts, can significantly strengthen the environment’s overall cybersecurity. Finding dangerous passwords in Active Directory is extremely important and helps organizations ensure user accounts are safe. Specops Password Auditor makes this process extremely easy. Within just a few minutes, IT admins can gain visibility to password risk they can remediate.
(Last updated on April 8, 2025)

