This website uses cookies to ensure you get the best experience on our website. Learn more
Business email compromise: Practical ways to reduce your risk
Table of Contents
Everyone uses email – you’d struggle to find a business that doesn’t. Unfortunately, for a form of digital communication we’ve been using since the 80s, it’s still very easy for cybercriminals to attack. As a result, email is the starting point for many attacks, including business email compromise (BEC). The FBI estimate $44 billion was lost to BEC attacks between 2016 and the end of 2021.
We’ll explain how BEC works, offer some ways to harden your organization’s defenses, and provide a fast, free solution to solve a major vulnerability – unused email accounts with weak passwords within your organization.
What is business email compromise?
Business email compromise is a form of cybercrime where attackers impersonate a known, trusted source to manipulate others into transferring money, sharing sensitive information, or performing other unauthorized actions. Attackers can create spoofed email addresses and display names to mimic an impersonation target and look believable to a recipient at first glance. However, some more advanced email security can detect spoofed email addresses, so account takeover is the more effective attack route.
Account takeover is where attackers gain access to a legitimate email account, often by compromising an existing employee’s password through phishing or social engineering. Another effective and less risky method is to get hold of login details for an unused account within the organization. Once they control the account, the attacker will carefully study the organization’s structure, communication patterns, and financial activities before launching their scam.
How does a business email compromise attack work?
The term BEC covers a few different but similar scenarios. Note the common themes in the below examples: email is the attack vector, a known and trusted source is impersonated, and a victim is socially engineered into performing an act that benefits the attacker.
- Invoice and payment fraud: Finance departments are targeted with fraudulent email invoices or requests to make a wire transfer. Attackers will make sure they know enough about a process to appear legitimate, while using social engineering to convince finance teams to work around their usual processes.
- CEO fraud: Attackers impersonate a high-ranking executive, such as the CEO or CFO, and email a lower-level employee, usually in the finance or human resources department. Company websites and LinkedIn can show internal chains of command to attackers. The email requests an urgent wire transfer or release of sensitive information, taking advantage of the employee’s willingness to comply with the executive’s demands.
- Supply chain compromise: This type of BEC scam involves attackers posing as a trusted vendor or supplier. Again, it’s relatively easy to work out vendor relationships using legal, open-source information. They may send a fake invoice or request payment for goods and services that were never delivered, often providing new payment details to divert the funds.
Help employees to identify BEC scams
BEC attacks rely on social engineering rather than malicious links and files – it’s the message itself that convinces victims to make a payment or divulge information. This makes it easier for the emails to bypass secure email gateways and other signature-based detection systems that rely on cross-referencing databases of known threats. While emails are text-based, attackers can use deepfake technology to supplement them with video or voice recordings to make attacks even more convincing.
Awareness and vigilance are crucial in identifying and preventing BEC scams. Here are some social engineering red flags to look for:
- Urgency and pressure: BEC emails often emphasize urgency and demand immediate action, pressuring the recipient to comply without questioning the request.
- Unusual requests: Be cautious of emails asking for actions outside of standard procedures or requesting sensitive information to which the sender should already have access.
- Changes in payment details: Always double-check if an email requests changes to payment details, especially if it comes from a known vendor or supplier.
- Changes in communication style: Although not always the case, some BEC scams contain misspellings or awkward phrasing, which may indicate a non-native speaker or a hastily crafted message. It’s also worth paying attention if a known colleague or vendor seems to change their language choices and the way they communicate via email.
- Signs of spoofing: Fake email addresses and display names can look convincing at first glance, especially on mobile devices. Double-check if you’re suspicious of a message – but remember you can’t rule out an account takeover attack.
Practical ways to prevent business email compromise
To protect your organization from BEC scams, consider implementing the following measures:
- Employee education – Regularly train employees to recognize and report potential BEC scams, emphasizing the importance of vigilance and following established procedures.
- Strengthen email security – Implement measures such as multi-factor authentication, strong passwords, and routine monitoring of email accounts for unusual activity. Remember BEC attacks can evade secure email gateways and less advanced email security software.
- Establish clear communication protocols – Create guidelines for verifying requests for sensitive information or financial transactions, including multiple levels of approval and direct communication with the requester.
- Keep software up to date: Ensure all software, including email clients and security tools, are regularly updated to protect against known vulnerabilities.
A major underlooked problem for many organizations is the pool of unused accounts with weak passwords that are ripe for account takeover attacks. The rest of this article will concentrate on the risks of inactive accounts and we’ll also provide you with a free tool to scan your own Active Directory for unused accounts and weak or compromised passwords.
Inactive or stale accounts and business email compromise
A key tactic cybercriminals employ in BEC scams is exploiting inactive or stale accounts. These accounts typically belong to former employees or accounts that have not been used for an extended period. Attackers may target these accounts because organizations often overlook them and may not have updated security measures, making them more susceptible to compromise.
How attackers access inactive accounts
Inactive or stale accounts may be compromised through credential reuse, brute force attacks, or even data breaches from other services. In some cases, former employees may have left their account credentials behind, allowing attackers to gain unauthorized access.
Why inactive accounts are appealing to attackers
Some forms of email security use social graphs to measure previous communication between accounts. Once attackers gain control over an inactive or stale account, they can exploit the account’s existing relationships and trust within the organization. Since stale accounts are often neglected, the attacker’s activities may go unnoticed for longer, allowing them to gather valuable information and plan their BEC attack more effectively.
Risks associated with inactive accounts in BEC Scams
Using inactive or stale accounts in BEC scams can make these attacks more challenging to detect and defend against. Employees may be more likely to trust requests from a familiar email address, especially if the account belonged to a former colleague or manager. Moreover, the lack of monitoring and security updates on these accounts provides cybercriminals with an ideal environment for attacks.
Mitigating the Threat of Inactive Accounts in BEC Scams
To minimize the risk associated with inactive or stale accounts, organizations should take the following steps:
- Regularly audit user accounts – Conduct periodic audits to identify and remove inactive or stale accounts, ensuring that all accounts are accounted for and have a legitimate purpose.
- Implement a robust offboarding process – Establish a thorough offboarding process for employees leaving the organization, including deactivating or deleting their email accounts and revoking access to all systems.
- Monitor account activity – Monitor account activity, including inactive or stale accounts, to identify unusual patterns or signs of compromise.
- Strengthen account security – Apply strong password policies and multi-factor authentication across all user accounts, including inactive ones, to reduce the risk of unauthorized access.
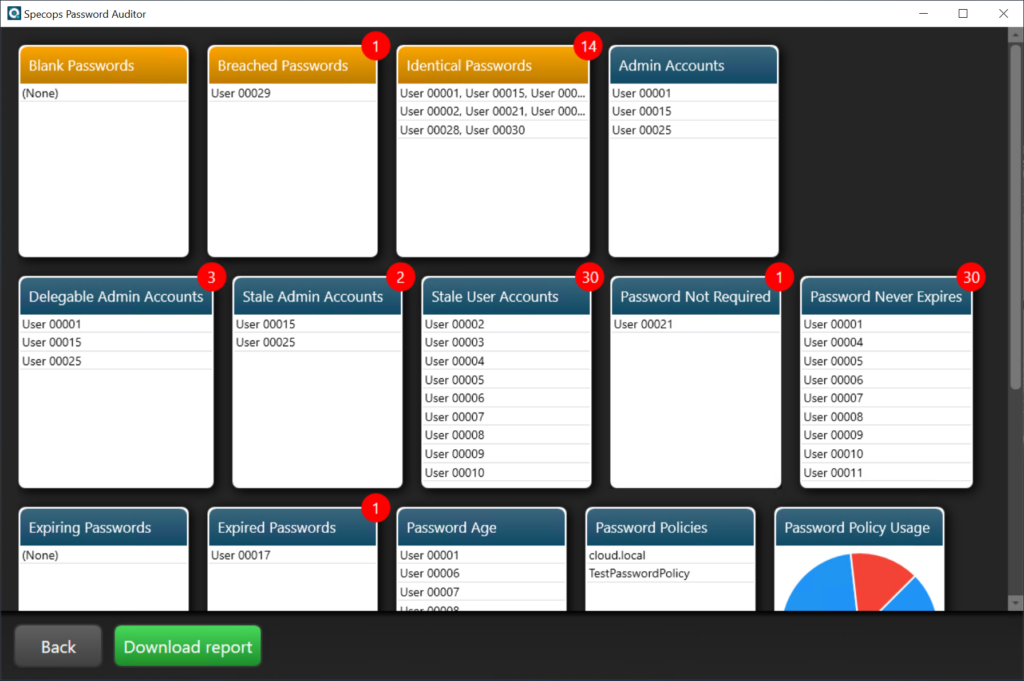
Minimize business email compromise risk with Specops Password Auditor
One effective way to reduce the risk of business email compromise is by ensuring the security of user accounts within your organization. Specops Password Auditor, a free tool from Specops Software, can help you achieve this by auditing and analyzing the password security of your Active Directory environment.
By using Specops Password Auditor, you can address common password vulnerabilities that may lead to BEC attacks:
- Strengthen password policies – Implementing strong password policies, such as minimum password length, complexity requirements, and regular password changes, can help prevent unauthorized access to email accounts.
- Detect and address compromised passwords – Identifying and resetting breached passwords can help mitigate the risk of attackers gaining control over an email account and using it for BEC scams.
- Regularly audit user accounts – Periodic account audits can help you identify and address inactive or stale accounts, minimizing the potential for attackers to exploit these accounts in BEC attacks.
- Monitor security group membership – Ensuring that only authorized users have access to sensitive information and systems can help reduce the risk of insider threats and unauthorized access to email accounts.
Reduce your BEC risk with a free Password Auditor trial
Email isn’t going anywhere soon. However, as we have discussed, it can be wrought with dangers and risks if the proper safeguards and processes are not in place. By proper offboarding processes, organizations can help ensure stale and neglected accounts are handled properly. In addition, using tools like Specops Password Auditor gives visibility to risky Active Directory accounts with expired or even breached passwords.
(Last updated on February 24, 2025)

