This website uses cookies to ensure you get the best experience on our website. Learn more

ALIEN TXTBASE Data Leak: How Data Recycling Impacts Risk
Table of Contents
ALIEN TXTBASE has emerged as one of the most active distributors of infostealer data on the dark web. Specops analysts have been monitoring this actor’s activity for months, reviewing each new batch of stolen credentials as it is released.
With the continued appearance of ALIEN TXTBASE data leaks, our latest analysis focuses on the quality and freshness of these datasets. The results point to a consistent pattern of data recycling, where older infostealer logs are mixed with newer material. This trend affects how organizations should interpret both the scale and severity of these leaks.
Below, we break down what Specops has newly uncovered, what it means for defenders, and how our tools help mitigate the risks from infostealer-driven credential exposure.
ALIEN TXTBASE Data Leak Latest: Specops adds 27 million new passwords to breached password database
Specops researchers analyzed consecutive ALIEN TXTBASE releases and found that many daily dumps include substantial amounts of recycled data. While the total daily file sizes appear massive, a significant percentage of the entries had already been released by ALIEN TXTBASE in previous dumps.
This pattern indicates that ALIEN TXTBASE is combining both new and old infostealer logs, which inflates the size of each release and makes it difficult to determine the true volume of newly exposed credentials at a glance.
However, despite the recycling, genuinely new data continues to appear in these dumps. In particular, one of the most recent ALIEN TXTBASE archives claimed more than 611 million records. After filtering and validation, this dataset still contributed more than 27 million new passwords to Specops monitoring systems.
It’s worth noting that depending on the day, anywhere from approximately 7% to more than 30% of the dataset had already appeared in the previous day’s release.
Even within the compressed window of a week, the recycling of old data was easily visible. When extended across several months, the pattern becomes even more pronounced, as shown in the tables below:
| Day of Release | Total Count | Unique Count | Delta with Previous Day | % Change | % Overlap |
|---|---|---|---|---|---|
| May 30 | 94161865 | 91223444 | 81179362 | 0.8898958255 | 11.01041745 |
| May 28 | 126574419 | 123304665 | 109531633 | 0.8883008035 | 11.16991965 |
| May 27 | 122357445 | 115334806 | 79040240 | 0.6853112494 | 31.46887506 |
| May 26 | 107905615 | 101389879 | 83831040 | 0.8268186216 | 17.31813784 |
| May 25 | 113794973 | 111190458 | 103295553 | 0.9289965601 | 7.100343988 |
| May 24 | 120059586 | 117047371 | 87802544 | 0.7501453749 | 24.98546251 |
| May 23 | 239312944 | 224329357 | 183320538 | 0.8171937033 | 18.28062967 |
The above table shows overlapping data from a single week. When we extrapolate that out across a three-month period, the trend looks like this:
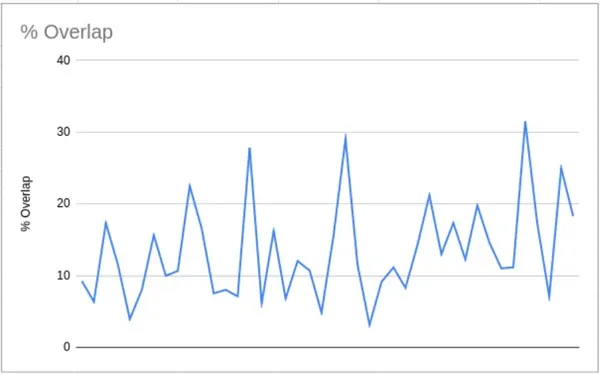
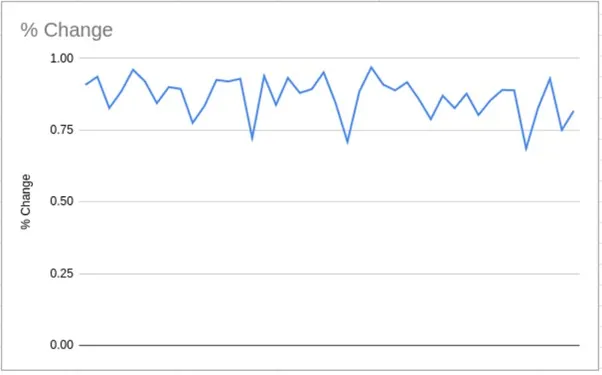
What organizations need to consider when assessing risk
Large credential collections regularly make the news and often create pressure for IT teams to respond immediately. However, our analysis shows that organizations need a more nuanced understanding of these infostealer dumps. We recommend the following things to keep in mind when accessing the risk posed by a data-dump:
- Not all large dumps represent new breaches. A dataset containing hundreds of millions of lines may include only a fraction of newly harvested credentials. Much of the content may be months old.
- Recycling inflates risk perception. Threat actors often combine old and new data to increase the size of dumps and draw attention from buyers or researchers. It is in the interest of attackers to inflate their figures to increase the perceived value of the data and clout.
- The real threat is in the new data, not the total size. Even a small number of newly exposed passwords is enough to enable credential stuffing attacks, leading to account takeover and lateral movement. Understanding which credentials are new and whether they belong to active accounts determines whether an incident response is warranted.
- Credential exposure is not a one-time event. Continuous monitoring is vital so that you can address new threats as they arise rather than reacting only when a major leak is publicized.
- Infostealer attacks will continue to rise in popularity. It’s likely that we haven’t heard the last of the ALIEN TXTBASE leaks and more will follow from other threat actors. Therefore, it is important that organizations take proactive steps to implement controls that minimize risk.
How Specops can help your organization defend against infostealers
The best defense against infostealers is a combination of strong password controls, compromised password monitoring, and continuous scanning. Specops products are purpose-built to help organizations defend against exactly this type of threat.
Protect your organization from password attacks
Specops Password Policy is the best defense against attacks that rely on these datasets. Specops Password Policy ensures users follow modern password requirements that reduce the likelihood of successful brute force or credential stuffing attempts.
In addition, it also continuously scans your Active Directory for breached and compromised passwords. If a user is found to be using a compromised password, they are notified immediately and required to change it. This ensures that stolen credentials cannot be reused during authentication and is one of the most effective defenses against infostealer-derived attacks.
You can try Specops Password Auditor for free and see the results for yourself. This tool gives you immediate visibility into access security risks by generating a comprehensive audit of your Active Directory. With clear, easy-to-read reporting, you can quickly identify password weaknesses and misconfigurations that attackers commonly exploit.
To learn more about how Specops can help protect your passwords and organization’s data, or to speak directly with an expert, please contact us here. For more insights and access to our research, please visit the Specops blog.
Last updated on December 3, 2025

