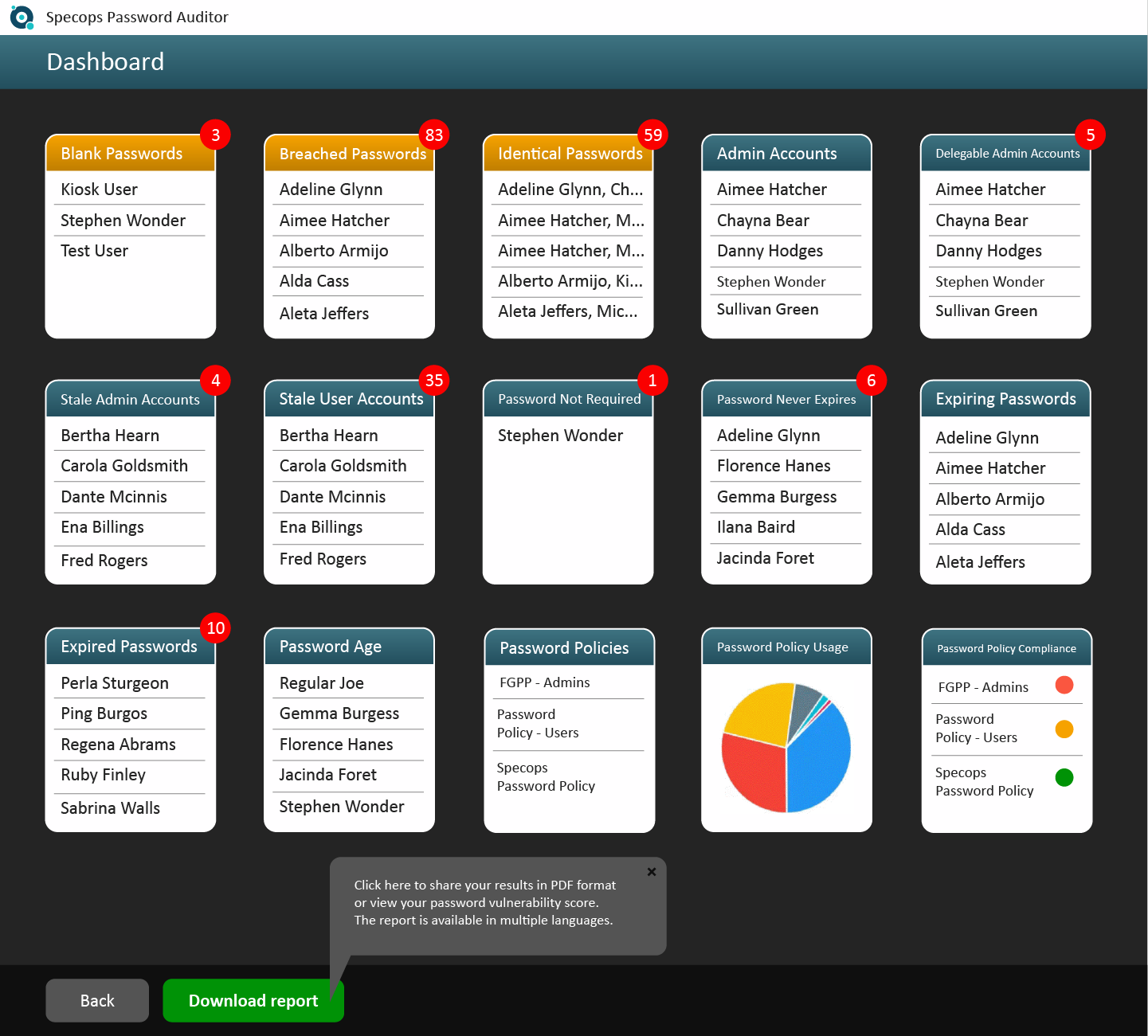
How to Audit Active Directory
If Active Directory security audits are a part of your ongoing IT operations, you’ve likely developed a methodology to evaluate your risks. With the sophistication of cyberattacks growing, you must rely on auditing tools to support your security plan. While there is no single tool or formula that can help you win the battle against cybercrime, your security risks can be distilled into a minority of vulnerabilities creating the majority of problems.
What are the top security threats facing your organization? It is a well-known fact that users reuse passwords across different systems. It is also common for applications to require corporate email addresses as the username. The duplication of corporate credentials on external systems is a serious threat facing IT departments.